Cybercriminals have compromised over 260,000 legitimate websites, embedding malicious JavaScript code disguised as an innocuous string of...
Do Son
Cybercriminals have devised a cunning method to transform outdated Discord server links into digital traps: a newly...
Jake Gallen was more than just a familiar face in the NFT scene—he had become a symbol...
The South Korean platform Yes24, the nation’s largest online ticketing service and a favored destination among K-pop...
Amid the deceleration of Moore’s Law and the surging energy demands of data centers, AMD has set...
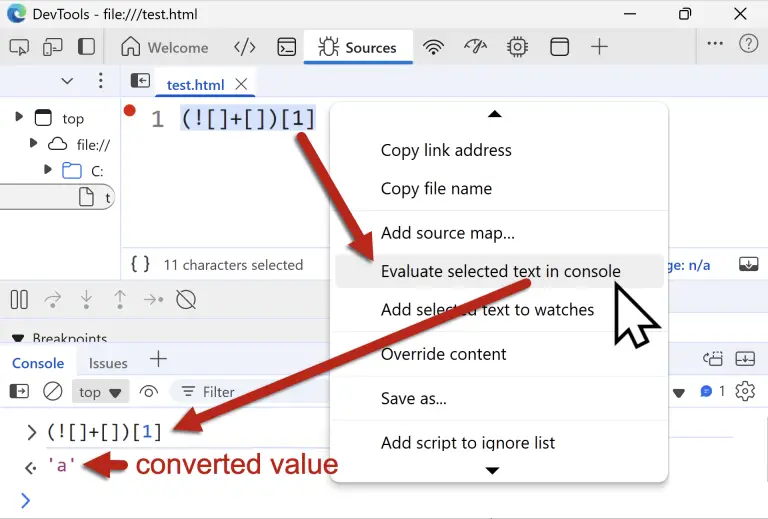
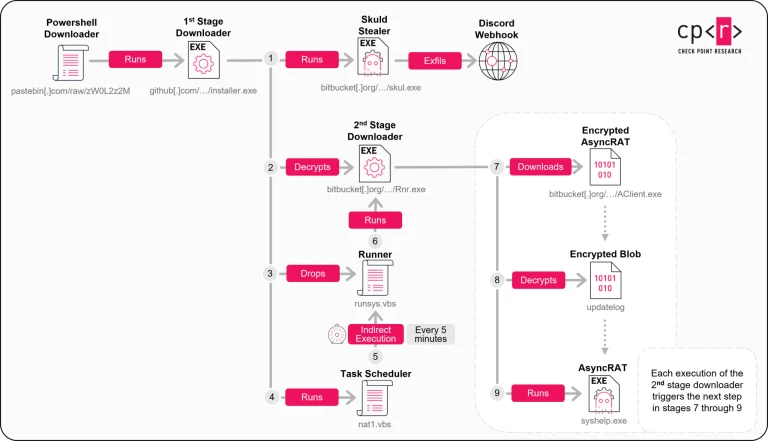
The criminal syndicate behind the Fog malware has adopted an unorthodox arsenal of tools for its campaigns,...
Researchers from HiddenLayer have unveiled a novel attack on language models that can bypass built-in moderation and...
Microsoft has unveiled a new feature called Copilot Vision—an extension of its AI assistant for Windows that...
Apple has unveiled a pivotal innovation poised to eliminate one of the key obstacles hindering the widespread...
On Thursday afternoon, the internet experienced widespread disruptions affecting hundreds of services—from global platforms like Cloudflare to...
At the beginning of the year, Google announced its decision to develop Android entirely behind closed doors,...
Google has begun testing a new feature called Audio Overviews—spoken summaries of search results delivered through two...
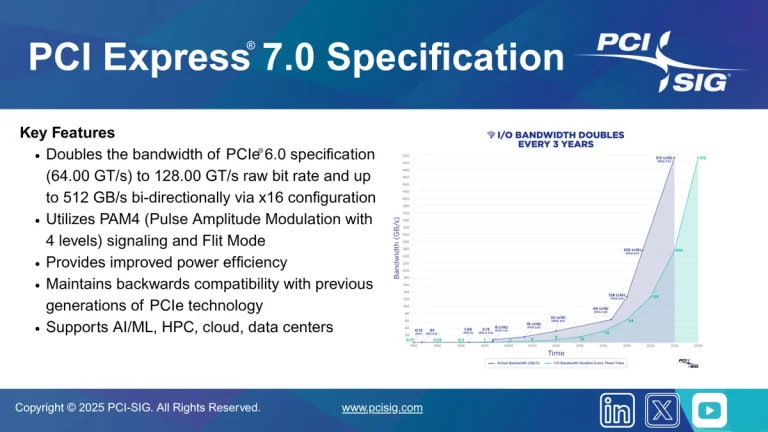
The PCI-SIG consortium, the industry body responsible for defining the PCIe standard, has officially released the PCIe...
Apple has quietly updated the security release notes for iOS 18.3.1, revealing that it has patched a...
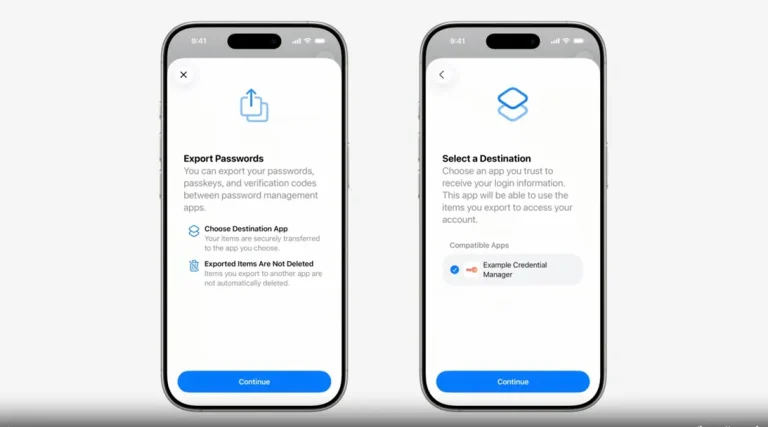
Modern smartphones have transcended their original role as mere communication tools — they have become gateways for...