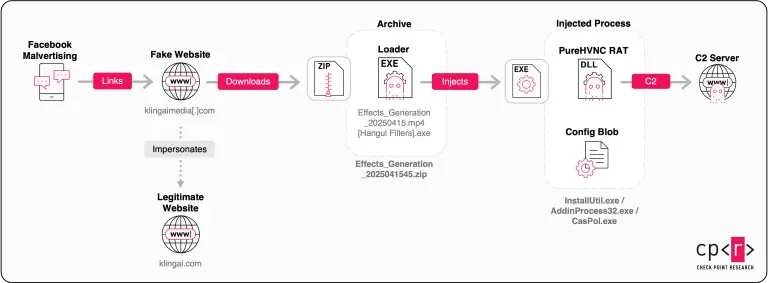
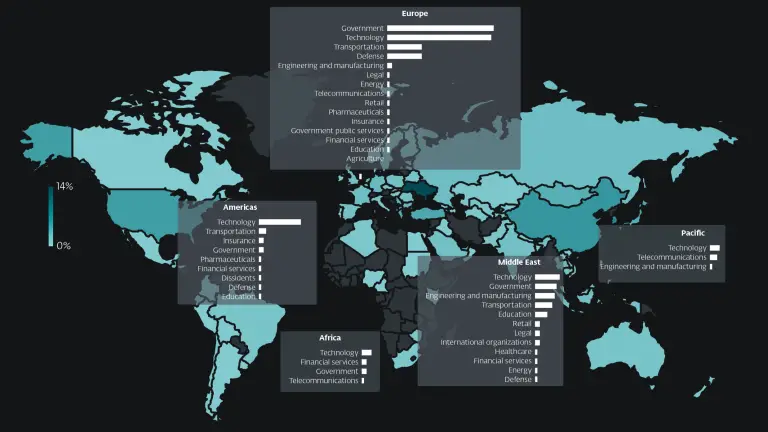
The soaring popularity of Kling AI, a platform capable of generating images and videos from text and...
Malware
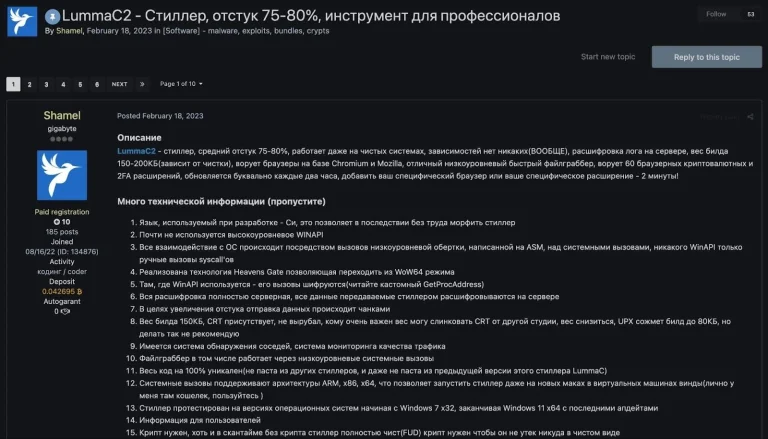
In the first half of May 2025, an international operation aimed at dismantling the infrastructure of Lumma...
A new malicious campaign targeting containerized infrastructures is spreading rapidly across the globe, transforming compromised containers into...
Several ransomware groups have begun actively deploying a strain of malware known as Skitnet during the post-exploitation...
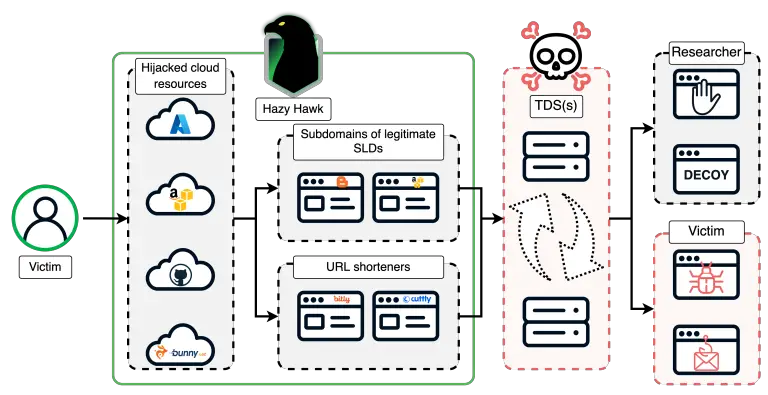
A threat actor known as Hazy Hawk has launched a widespread campaign to seize abandoned cloud assets...
Amid a surge in attacks targeting exposed internet-facing services, cybersecurity experts have identified a new malicious campaign...
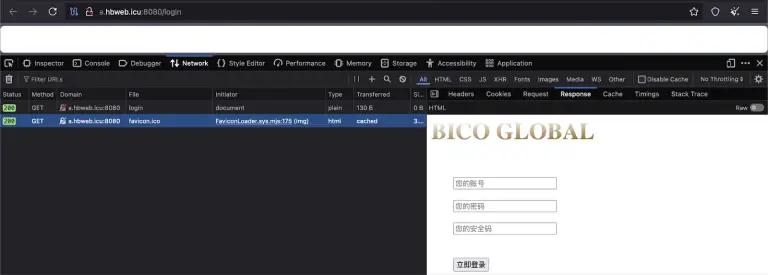
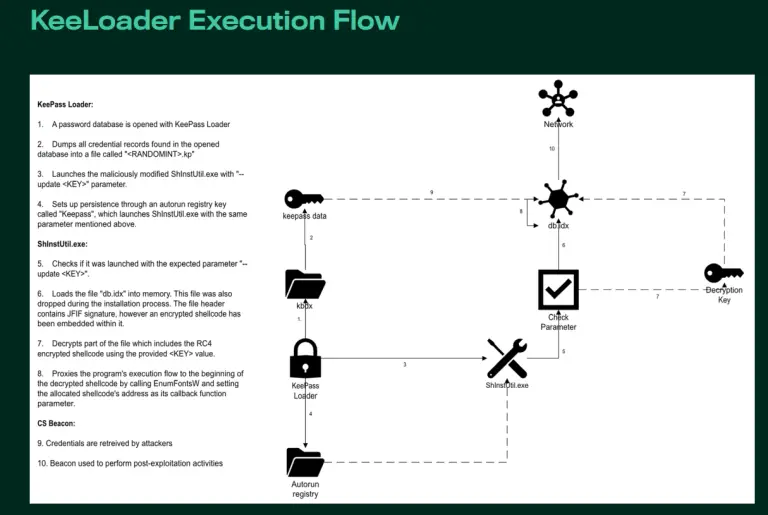
For over eight months, a cybercriminal group has been distributing trojanized versions of the KeePass password manager,...
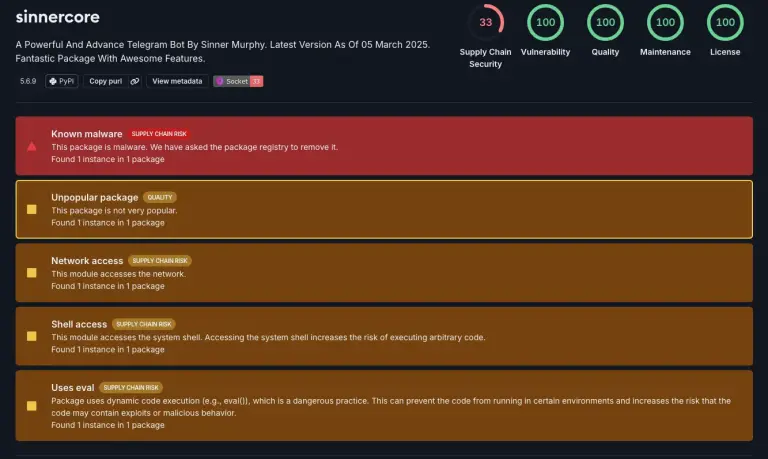
Threat actors continue to exploit popular open-source repositories as launchpads for the distribution of malicious code. This...
Researchers at ESET have uncovered the operations of a little-known yet active cyber-espionage group linked to China,...
Since February 2024, the Chrome Web Store has been hosting malicious browser extensions disguised as useful utilities,...
Hackers have compromised the official website of RVTools—a widely used utility for managing VMware virtual infrastructures—and replaced...
Experts at the Chinese cybersecurity firm NSFOCUS have identified an active campaign involving a new botnet known...
For at least six months, official software for Procolored printers had been silently distributing malware — including...
Researchers at Qualys have issued a warning about a new malicious campaign that leverages a PowerShell script...
A newly released tool named Defendnot, freely available on GitHub, possesses the capability to completely disable Microsoft...