An increasing number of cybercriminals are shifting toward the use of so-called residential proxy networks, transforming ordinary...
Cybercrime
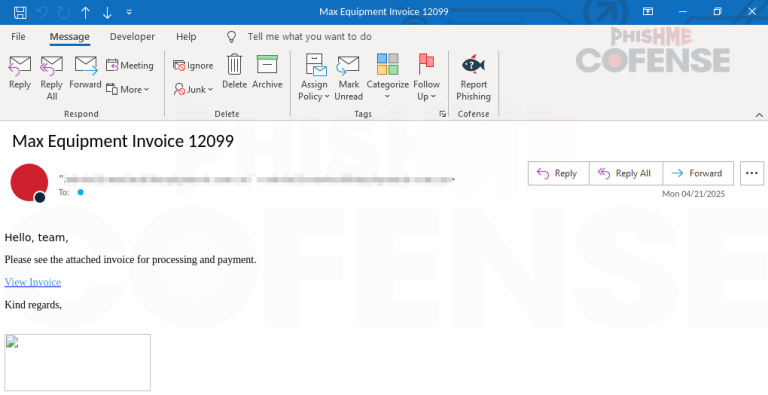
At first glance, it appears to be nothing more than a routine security check. In reality, it...
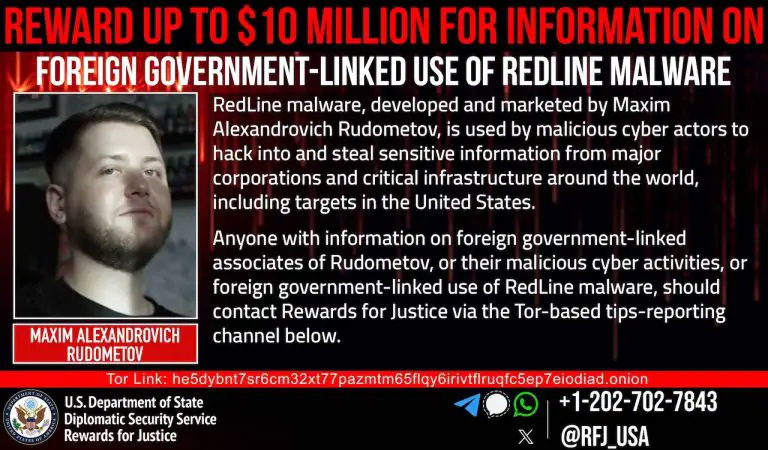
The U.S. Department of State has announced a reward of up to $10 million for information leading...
Ukrainian cyber police have apprehended a 35-year-old man who, over several years, exploited compromised servers belonging to...
One of the most notorious underground marketplaces for trafficking stolen banking data—BidenCash—has ceased operations following a large-scale...
The FBI has updated its joint advisory with the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and...
Mozilla has introduced a new protective mechanism aimed at combating malicious Firefox extensions that siphon cryptocurrency from...
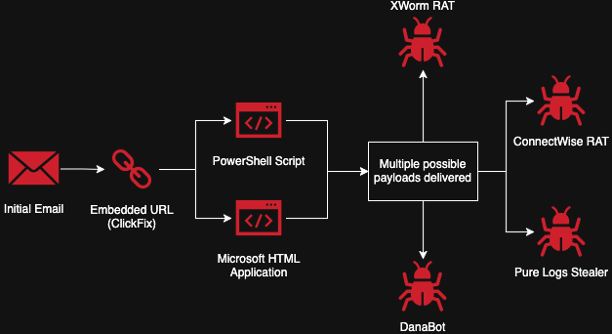
Researchers from the DomainTools team have reported a new malicious campaign that leverages counterfeit websites masquerading as...
In the cybersecurity industry, each major player has long relied on its own nomenclature for threat groups...
Cryptocurrency exchange Coinbase has found itself at the center of a data breach scandal, with sources claiming...
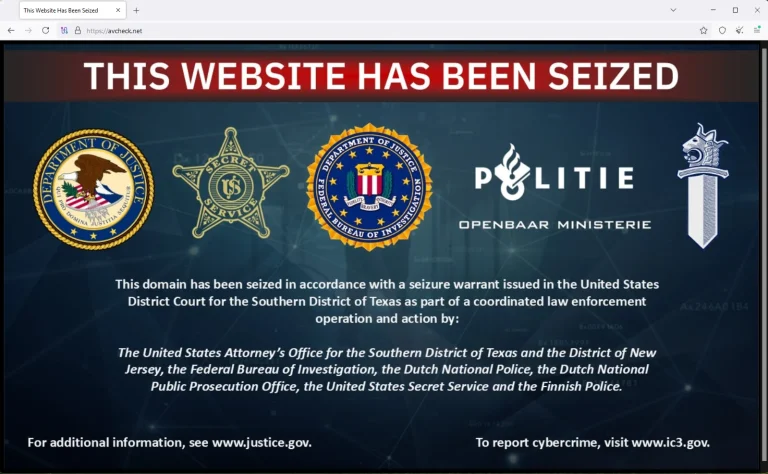
One of the most infamous underground services catering to cybercriminals—AVCheck—has come to an end. Its primary domain,...
Automotive giant Volkswagen Group has unexpectedly appeared on a darknet leak site operated by the ransomware collective...
Australia is ushering in a new chapter in its battle against cybercrime: under recently enacted legislation, major...
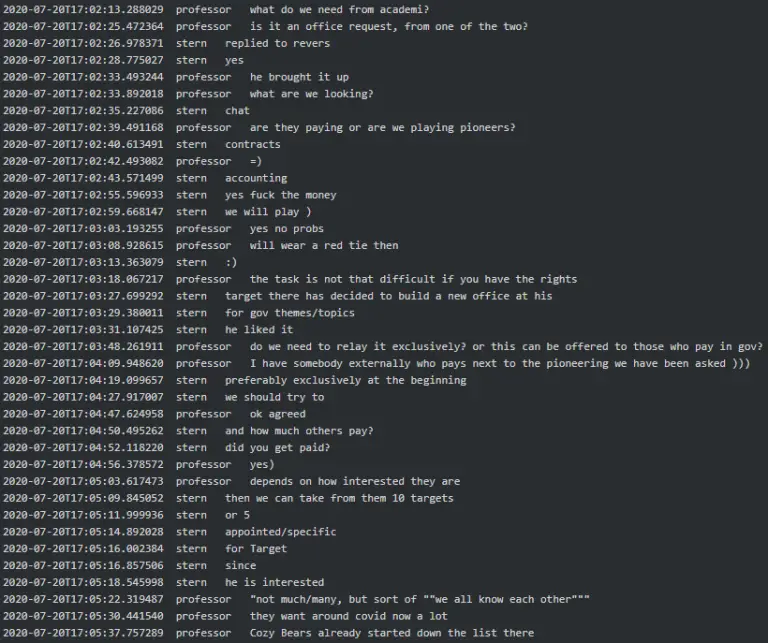
The German Federal Criminal Police Office (BKA) has, for the first time, officially disclosed the true identity...
Cybercriminals have discovered a novel method for circumventing security systems by hosting phishing pages on the Google...