As previously announced by Microsoft, the company has officially unveiled a new 12-inch Surface Pro and a...
The Trump administration is preparing to undertake a sweeping overhaul of the United States’ cybersecurity framework. The...
Hackers have breached the systems of GlobalX Air, an airline heavily utilized by the Trump administration for...
South Korean telecommunications giant SK Telecom has suspended the registration of new subscribers nationwide, shifting its focus...
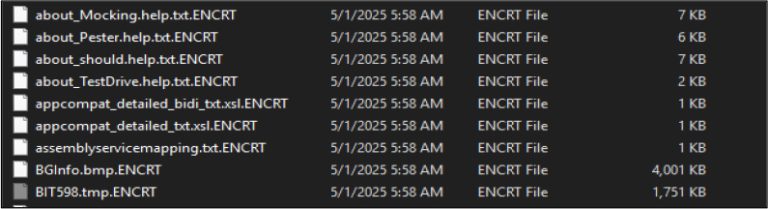
In April 2025, the cyber threat landscape witnessed the emergence of a formidable new adversary—ransomware known as...
The cybercriminal group Venom Spider, also known as TA4557, has shifted its attack vector and is now...
Simplified application deployment in Kubernetes using Helm can lead to serious vulnerabilities if default configurations are left...
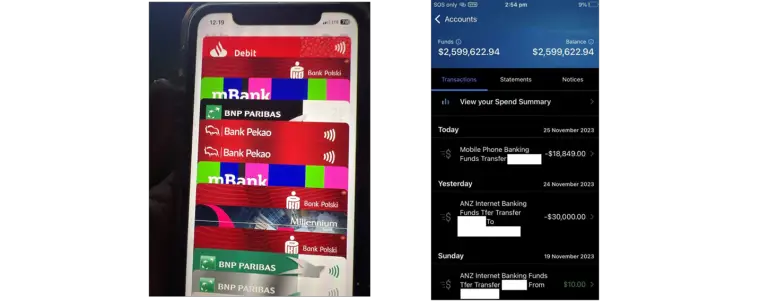
A vast cyberfraud scheme leveraging the Darcula platform has led to the compromise of hundreds of thousands...
Phishing call attacks have once again drawn the attention of cybersecurity experts. This time, the group known...
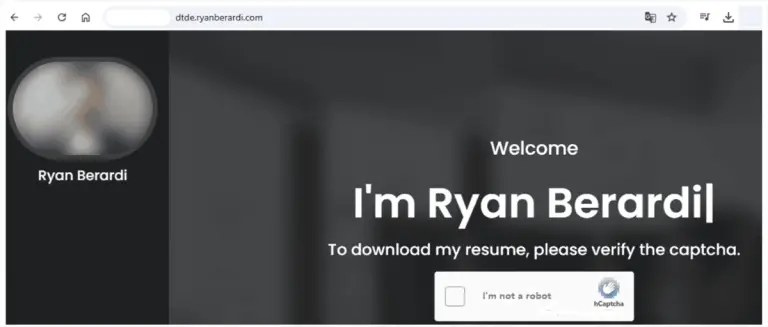
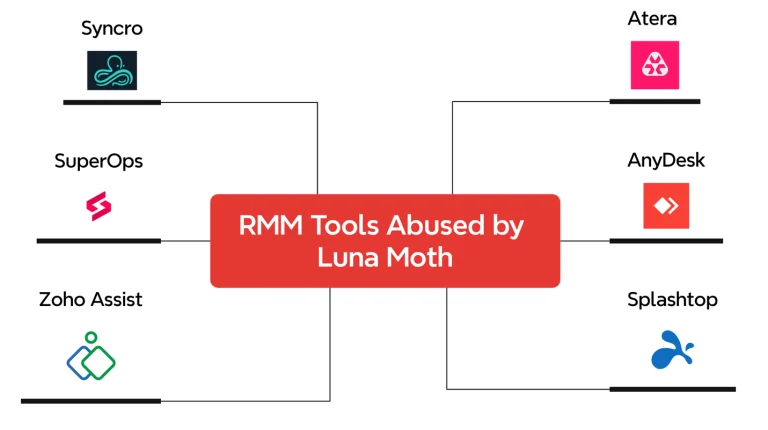
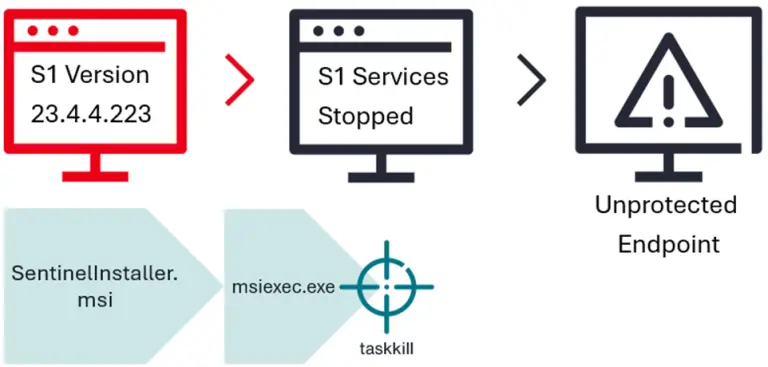
In early 2025, incident response specialists from Aon’s Stroz Friedberg team uncovered a novel technique for bypassing...
The Trump administration intends to recalibrate its stance on offensive cyber operations, framing them as a legitimate...
According to a report by Business Insider, Google has recently launched a new film initiative titled “100...
Google has released its latest Android security update, addressing 46 vulnerabilities—one of which is already being actively...
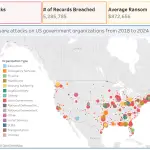
Ransomware attacks targeting the agribusiness sector in 2025 have grown markedly in both scale and intensity, according...
Global performance advertising leader Taboola has announced a new strategic partnership with Samsung, aimed at delivering curated...