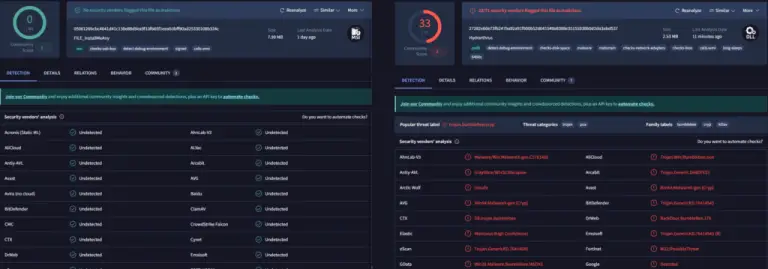
Hackers have compromised the official website of RVTools—a widely used utility for managing VMware virtual infrastructures—and replaced...
The developers have released updates for several versions of the Linux kernel, including 6.14.7 and other actively...
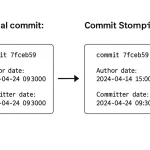
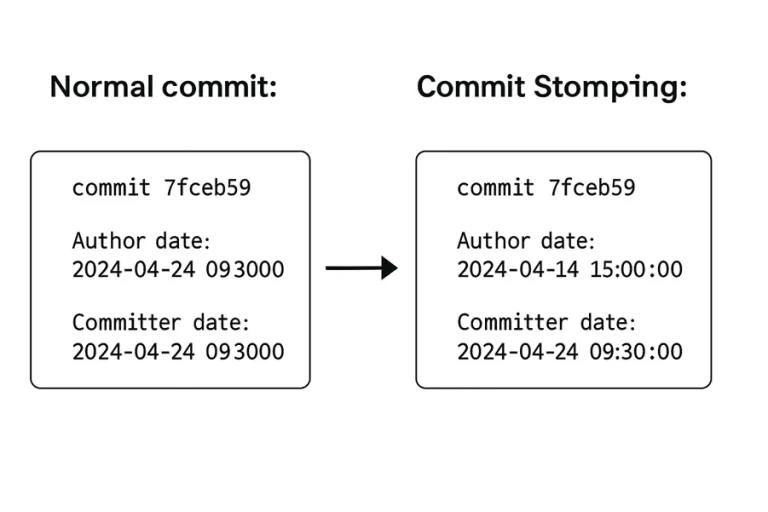
A method for concealing change history has been uncovered in Git, capable of misleading even seasoned digital...
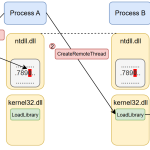
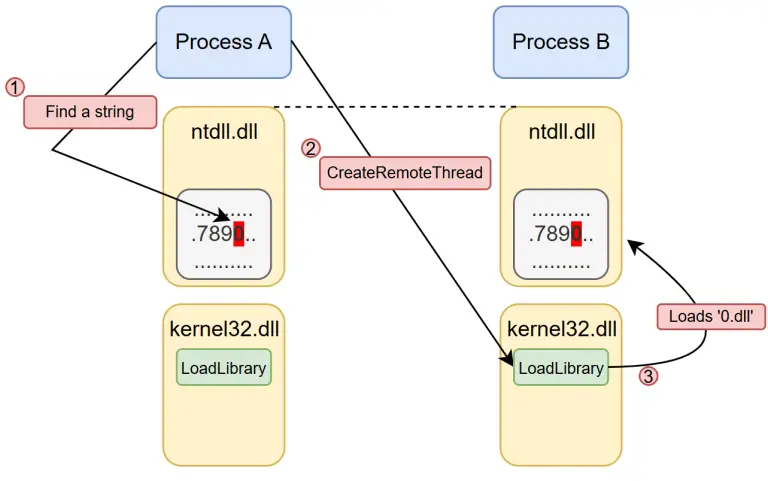
Recent research has demonstrated novel techniques for injecting malicious code into Windows processes without relying on traditional...
The Eventin plugin, widely used for event management on WordPress websites, was found to be vulnerable to...
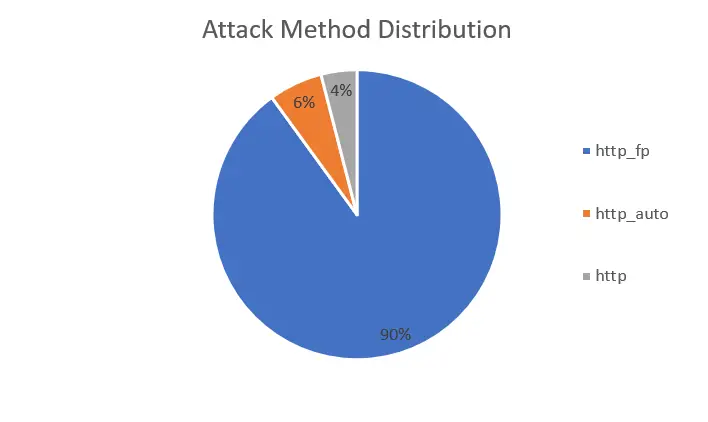
Experts at the Chinese cybersecurity firm NSFOCUS have identified an active campaign involving a new botnet known...
For at least six months, official software for Procolored printers had been silently distributing malware — including...
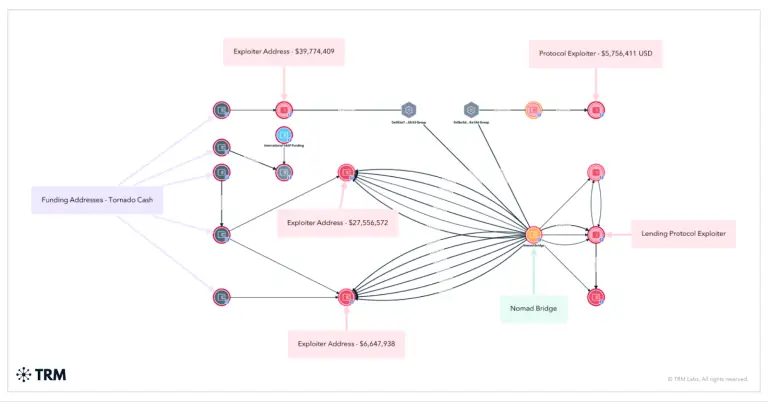
Alexander Gurevich, a dual American-Israeli citizen, has been arrested in Jerusalem on charges related to one of...
Researchers at Qualys have issued a warning about a new malicious campaign that leverages a PowerShell script...
A newly released tool named Defendnot, freely available on GitHub, possesses the capability to completely disable Microsoft...
The iPhone 17 Air is Apple’s forthcoming model, distinguished most notably by its remarkably slim and lightweight...
Japan has officially abandoned its longstanding restraint in cyberspace. On May 16, a landmark law was enacted,...
At the ongoing Pwn2Own hacking tournament in Berlin, a historic milestone was achieved: elite cybersecurity experts successfully...
Once again, AMD has demonstrated that its processors truly unleash their full potential under Linux. The new...
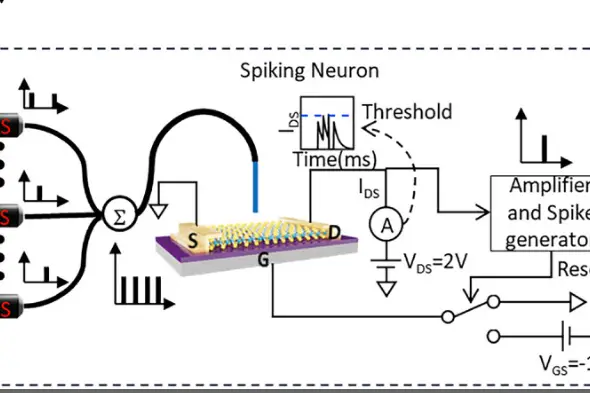
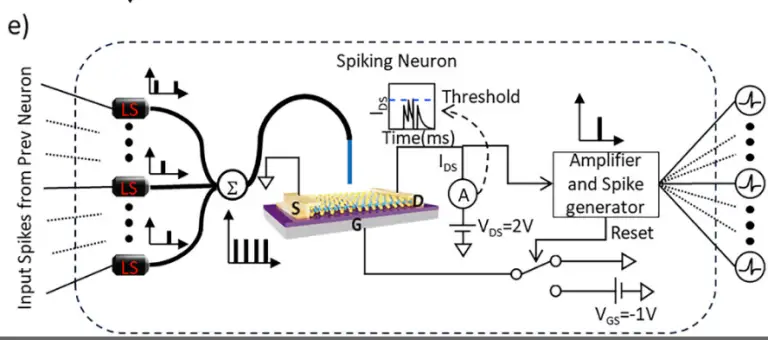
Engineers at the Royal Melbourne Institute of Technology have developed a miniature technology capable of processing visual...