Google has released an unscheduled update for the Chrome browser, addressing three security vulnerabilities—one of which is...
Security
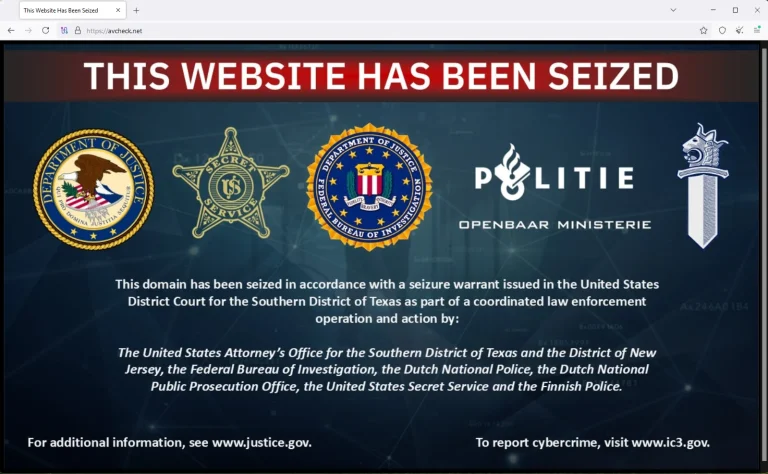
One of the most infamous underground services catering to cybercriminals—AVCheck—has come to an end. Its primary domain,...
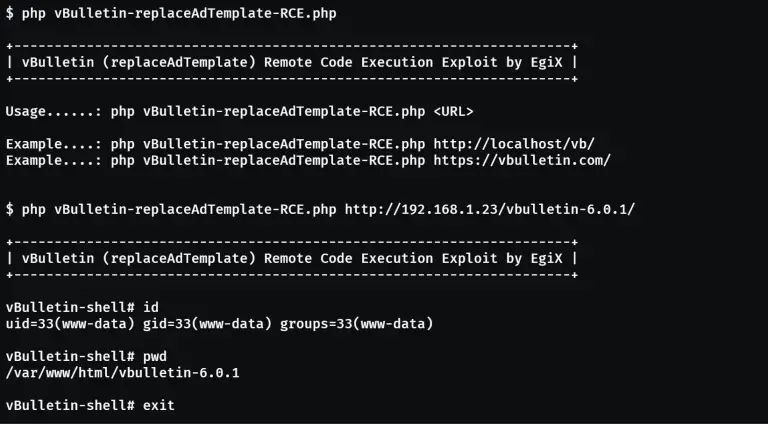
Critical security flaws have once again been discovered in popular vBulletin forums—vulnerabilities that allow for arbitrary code...
The technical details of one of the most perilous vulnerabilities of 2025—CVE-2025-20188—have now been made publicly available....
Automotive giant Volkswagen Group has unexpectedly appeared on a darknet leak site operated by the ransomware collective...
Linux 6.16 Revitalizes Confidential Computing with Major Trusted Security Manager (TSM) Enhancements


Linux 6.16 Revitalizes Confidential Computing with Major Trusted Security Manager (TSM) Enhancements
At the end of 2023, the long-anticipated feature for unified handling of attestation reports in confidential computing...
Two information disclosure vulnerabilities have been identified in Linux systems, including Ubuntu, Red Hat Enterprise Linux, and...
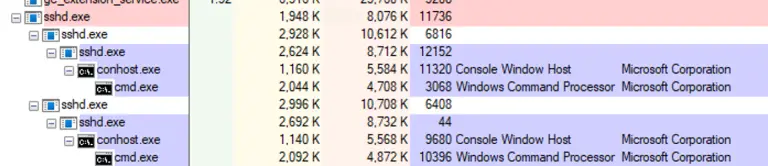
The remote management functionality of Azure Arc, designed to centralize administration across hybrid infrastructures, has proven unexpectedly...
Australia is ushering in a new chapter in its battle against cybercrime: under recently enacted legislation, major...
Newly surfaced details have shed light on the arrest of an IT department employee from the U.S....
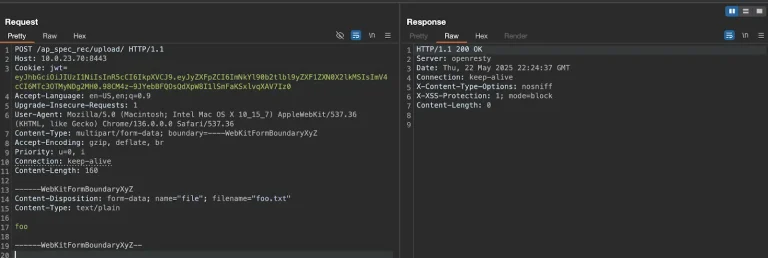
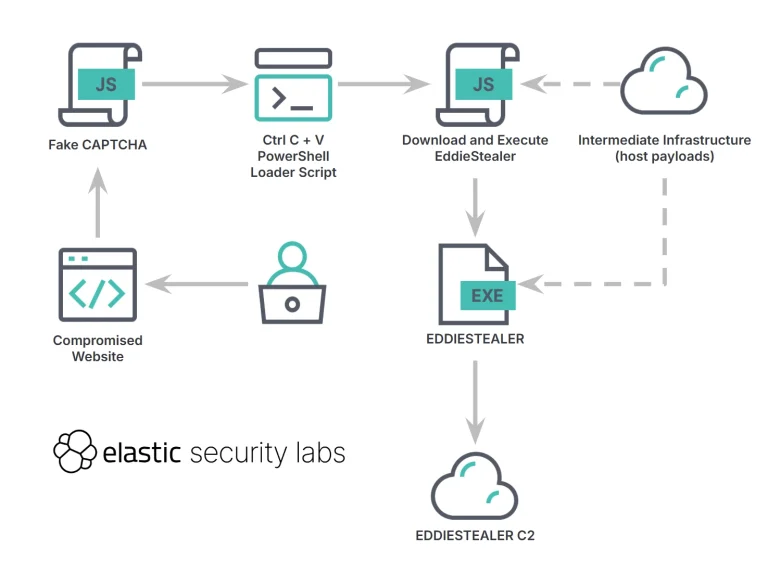
A new wave of attacks leveraging the EDDIESTEALER malware has starkly illustrated the growing ingenuity of social...
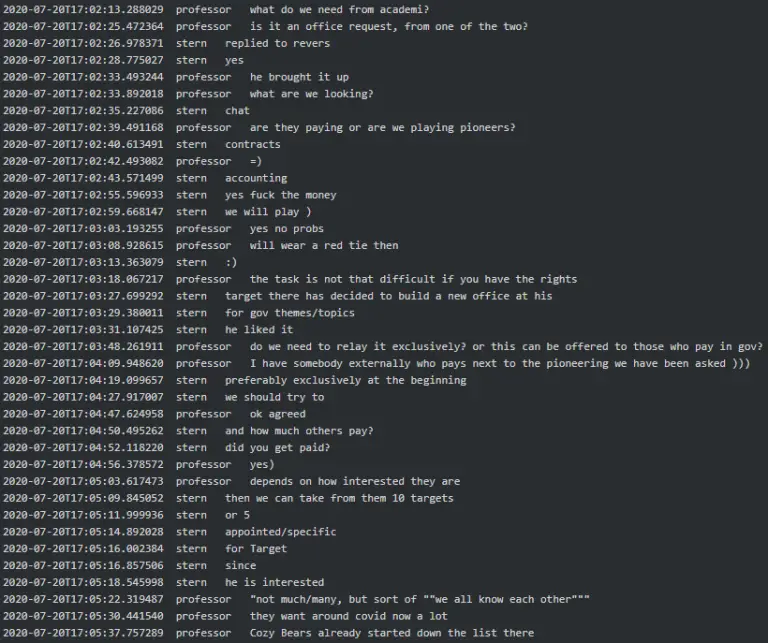
The German Federal Criminal Police Office (BKA) has, for the first time, officially disclosed the true identity...
Qualcomm has released critical security updates to address three zero-day vulnerabilities discovered in the Adreno GPU drivers,...
An investigation has been launched at the White House following reports that unknown individuals gained access to...
A research team from Palisade Research has published an extraordinary report highlighting the offensive capabilities of modern...