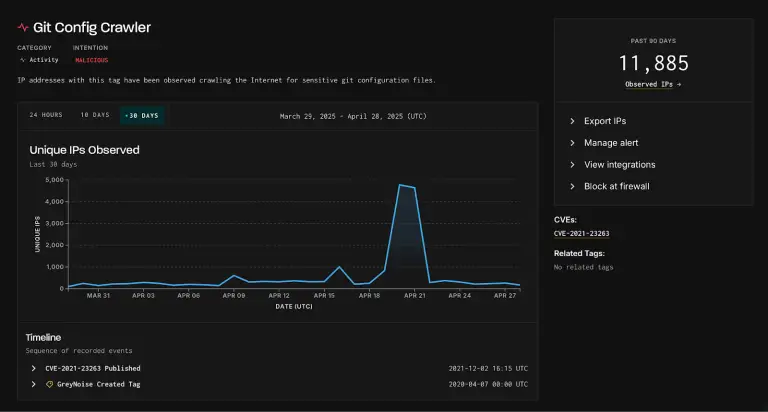
In recent days, cybersecurity experts have observed a disturbing surge in activity aimed at accessing configuration files...
Security
A comprehensive study conducted by Rubrik Zero Labs has confirmed that in 2024, nearly 90% of IT...
The majority of residents across Spain, Portugal, and southern France have resumed normal life following a widespread...
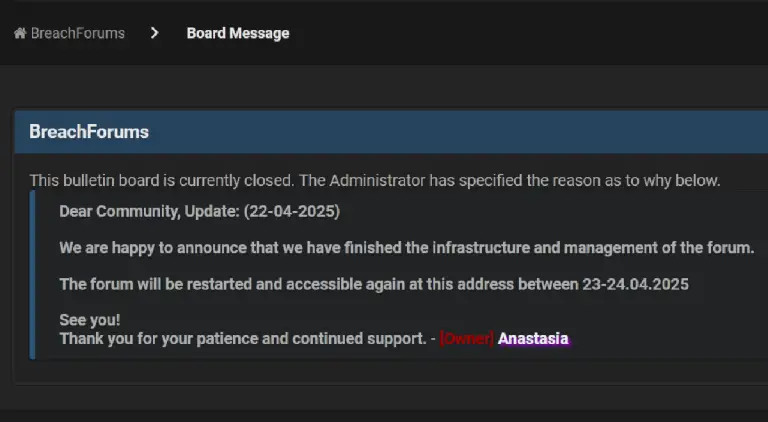
Another attempt to revive the infamous hacker marketplace BreachForums has ended in failure, as malicious actors exploited...
Iran has reportedly repelled one of the most extensive and sophisticated cyberattacks ever launched against its national...
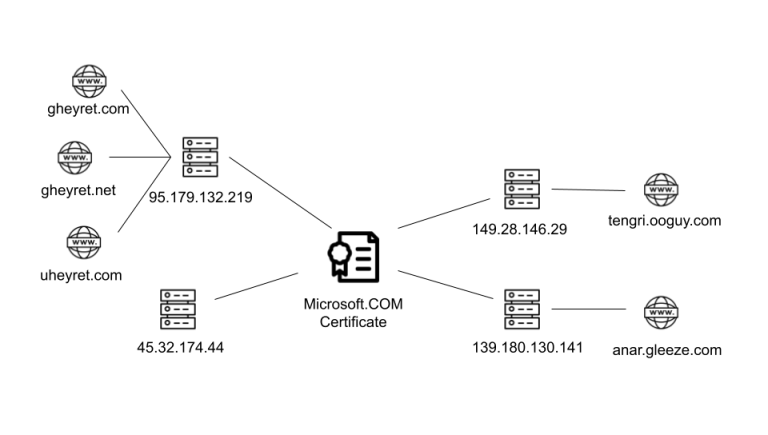
In March 2025, senior members of the World Uyghur Congress (WUC), living in exile, fell victim to...
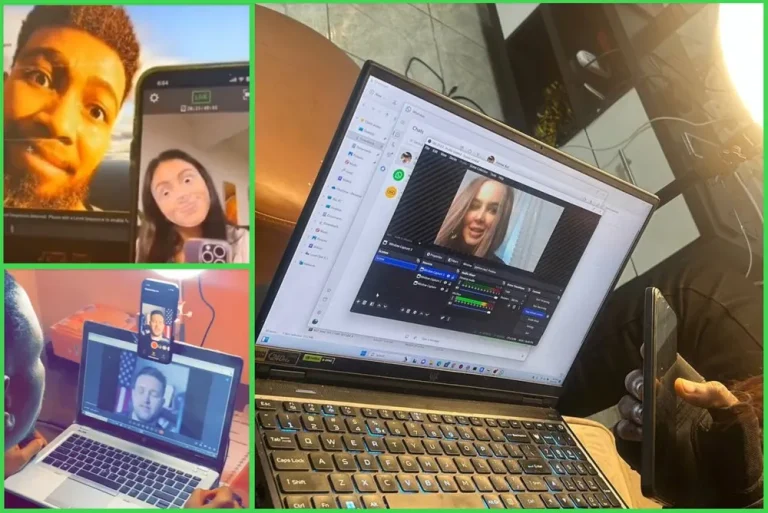
Online fraud is entering a new and more insidious era: modern scammers have learned to wield deepfake...
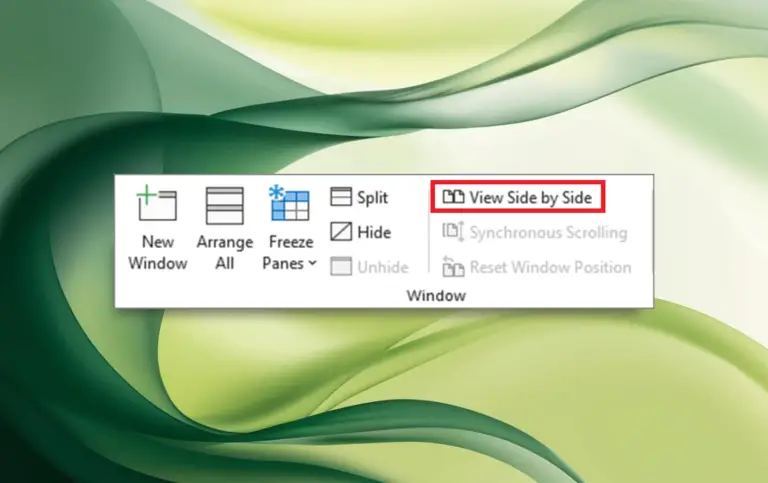
The “Side-by-Side View” feature, already available in Excel for Windows, enables users to display two worksheets within...
The United States Cybersecurity and Infrastructure Security Agency (CISA) has added two new critical vulnerabilities affecting Broadcom...
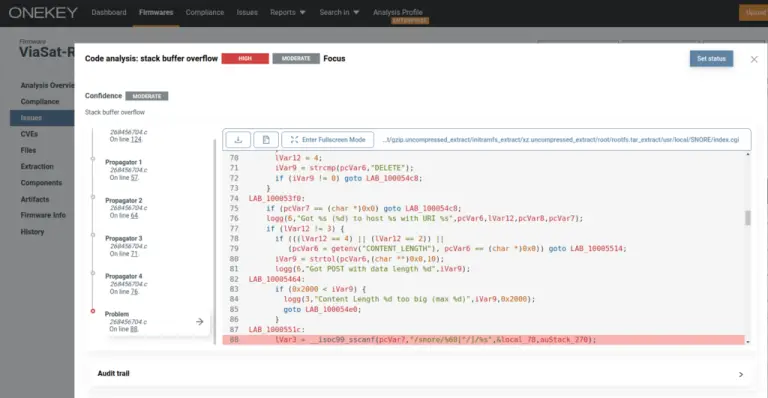
The discovery of a serious zero-day vulnerability in Viasat satellite modems has once again underscored the fragility...
On April 14, one of 4chan’s servers fell victim to an attack exploiting a vulnerability in outdated...
A major ransomware incident has struck the infrastructure of Hitachi Vantara, a subsidiary of the Japanese conglomerate...
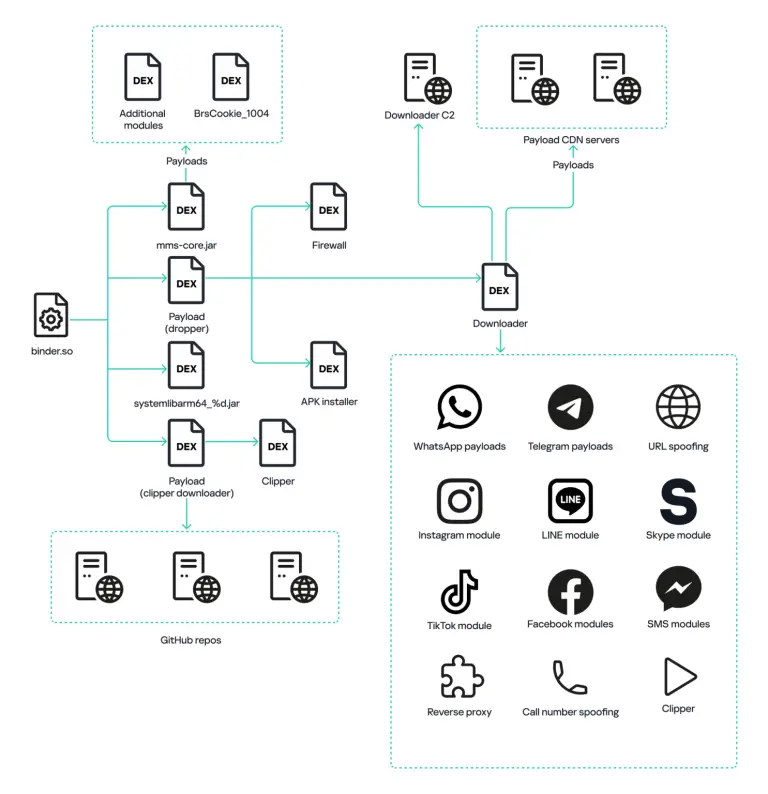
Newer versions of Android have significantly strengthened system security by prohibiting the modification of system partitions, even...
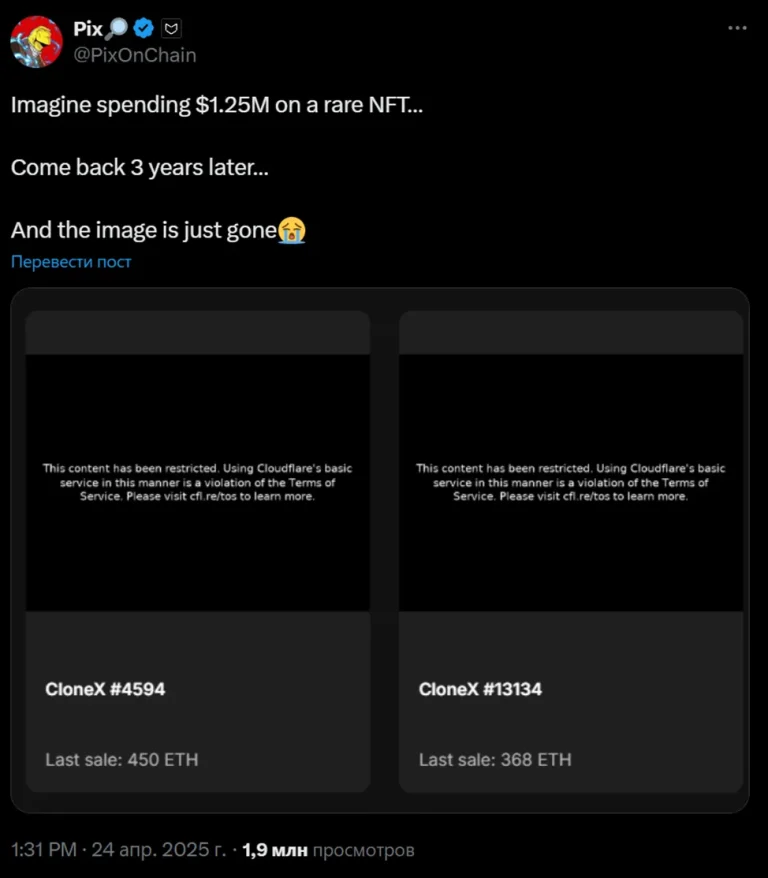
On April 25, thousands of NFTs from the CloneX RTFKT collection—once sold for millions of dollars—suddenly vanished...
A cybersecurity enthusiast from Russia reported a critical vulnerability in the Telegram messenger, which, in his opinion,...