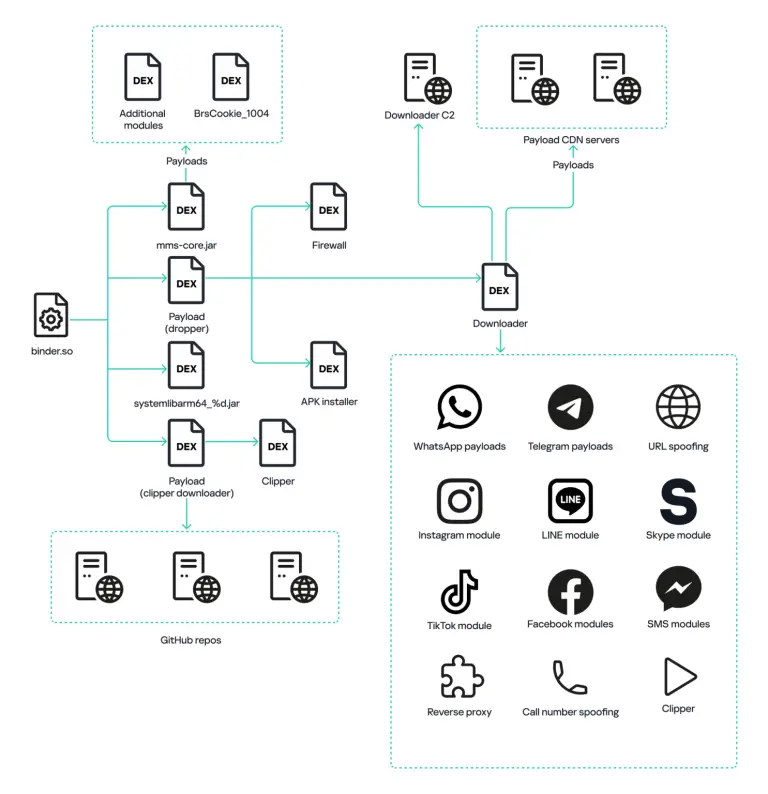
Newer versions of Android have significantly strengthened system security by prohibiting the modification of system partitions, even...
Do Son
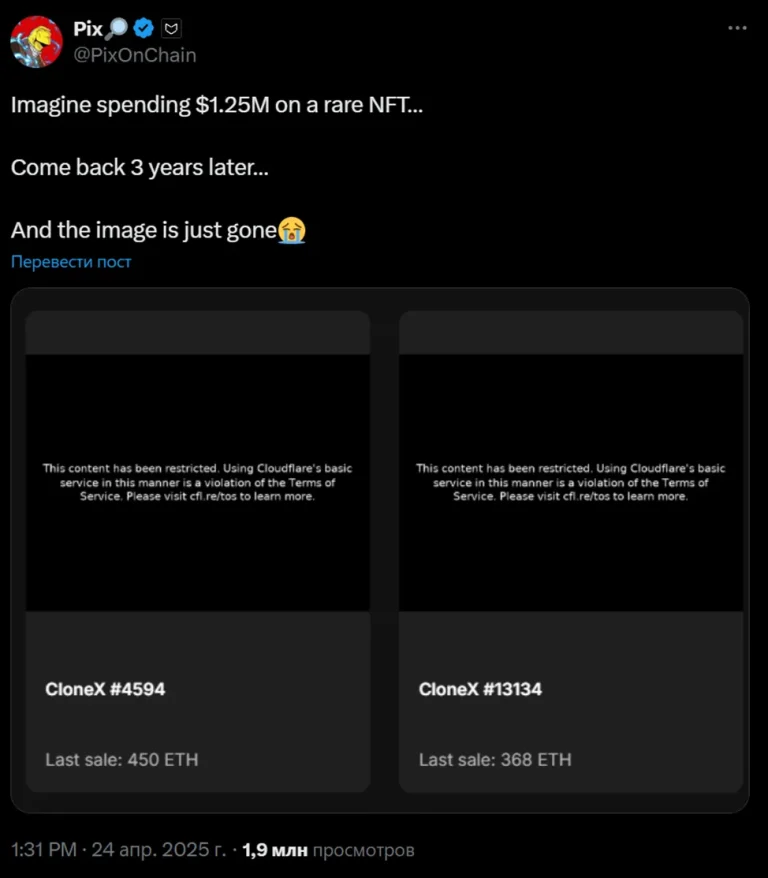
On April 25, thousands of NFTs from the CloneX RTFKT collection—once sold for millions of dollars—suddenly vanished...
The Offensive Security team has issued a warning to Kali Linux users regarding potential system update failures—preventable...
A cybersecurity enthusiast from Russia reported a critical vulnerability in the Telegram messenger, which, in his opinion,...
One of the key issues in AI security has once again come to the forefront following the...
Just as advertisers are devising new strategies to enhance brand visibility within conversational AI platforms—or to embed...
In response to the new tariff policies introduced by the Trump administration, crowdfunding platform Kickstarter has announced...
The FBI has announced a reward of up to $10 million for information regarding the hacker group...
Brave has unveiled a new tool called Cookiecrumbler, designed to combat intrusive cookie consent notifications. What sets...
Researchers at Cybernews have uncovered a massive data leak involving the popular iOS application Second Phone Number,...
The OpenBSD project has announced the release of a new version of its operating system — OpenBSD...
Google has asserted in court that its Chrome browser cannot be recreated without deep integration with the...
After spending several hours immersed in a military cyber-operations simulator, one player made a curious observation: within...
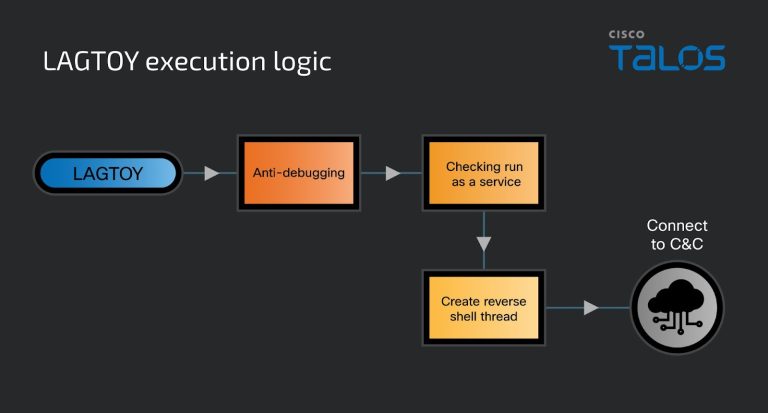
A new and formidable player has emerged on the cybercrime stage: Cisco Talos has uncovered the operations...
Coinbase has resolved a bug in its account activity log that had sparked widespread alarm among users....