The German Federal Criminal Police Office (BKA) has, for the first time, officially disclosed the true identity of the individual behind the notorious hacker groups TrickBot and Conti. According to investigators, the alias “Stern” concealed a 36-year-old Russian national—referred to as K. This revelation was made last week as part of the ongoing results of the global Operation Endgame, a coordinated initiative involving dozens of countries targeting malicious cyber infrastructures and key players within the shadowy cybercrime economy.
German authorities assert that K. was among the founding figures of TrickBot—also known by its other moniker, Wizard Spider. This group wielded an expansive arsenal of malicious tools, ranging from the eponymous TrickBot banking trojan to droppers like BazarLoader and SystemBC, trojans such as IcedID and Diavol, and ransomware strains including Ryuk and Conti, which inflicted damage upon hundreds of organizations worldwide.
An Interpol Red Notice has already been issued against the hacker, who now stands formally accused of leading a criminal organization. Though the BKA documents refrain from naming the group explicitly, the implication is clear: this is the alleged head of a transnational cybercriminal syndicate structured along corporate lines—with defined hierarchies, project segmentation, financial accounting, and centralized command.
This is not the first time the man has appeared on the radar of international law enforcement. As early as February 2023, his name was included in a list of seven Russians indicted by the United States for their roles in TrickBot and Conti. At the time, he was identified as a senior figure within the organization, operating under aliases such as Bentley, Bergen, Alex Konor, and Ben. However, his leadership status was not fully recognized until new leaks and the analysis of internal communications illuminated his central role.
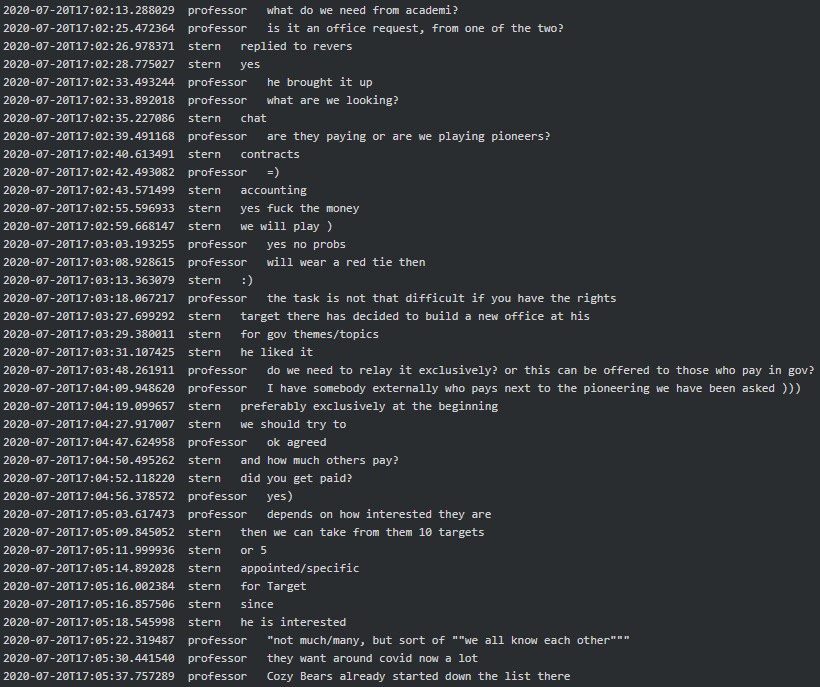
The case came into sharper focus following the publication of two major leaks: TrickLeaks and ContiLeaks. The former exposed personal data, user credentials, and contact information of TrickBot members; the latter unveiled source code and internal communications from within the Conti collective. In these messages, Stern was frequently referenced as the authority figure to whom others submitted attack plans, recruitment requests, and even appeals for legal assistance on behalf of arrested hackers in the United States.
These revelations not only laid bare the internal workings of the group but effectively dismantled Conti itself. Following the leaks, many operatives abandoned the project and splintered into new criminal factions, among them the likes of Royal, Black Basta, BlackCat, AvosLocker, Karakurt, LockBit, Silent Ransom, DagonLocker, and ZEON. In essence, a single data breach decentralized one of the most formidable cybercrime syndicates in modern history.
In its Friday statement, the BKA emphasized the scale and organizational sophistication of TrickBot. At its peak, the group comprised over 100 active members, operated on a project-based model, and was driven solely by profit. Its infection campaigns affected hundreds of thousands of systems—not only in Germany but across the globe. Victims included hospitals, government agencies, businesses, and private individuals. The financial damage is estimated in the hundreds of millions of euros.
Despite years of investigative efforts, the whereabouts of K. remain unknown. The BKA believes he is likely residing in Russia and urges both citizens and cybersecurity professionals to report any information that may assist in locating him—from online aliases and communication channels to digital footprints.
Operation Endgame, of which this investigation is a part, continues to be one of the largest international efforts aimed at dismantling malware infrastructure. In addition to TrickBot and Conti, the campaign has also targeted and neutralized servers and domains associated with other major cyber threats, including Danabot and Smokeloader. The investigation remains ongoing, with authorities clearly intent on systematically dismantling the logistics of the digital underworld—starting from the very top.


