Security specialists at Cleafy, a company focused on mobile device protection, have unveiled the details of a new criminal scheme threatening bank card holders. Cybercriminals have developed a platform called SuperCard X, operating under a “malware-as-a-service” model, which enables the theft of card data via a smartphone’s NFC module for subsequent fraudulent transactions at point-of-sale terminals and ATMs.
The investigation revealed that the platform’s development is linked to actors associated with China. Upon analyzing the code, the researchers identified striking similarities with the open-source project NFCGate and its malicious derivative, NGate. The latter has been actively used in attacks across European countries for over a year, underscoring the continuity of cybercriminal technologies.
SuperCard X is distributed through Telegram channels, offering not only the product itself but also direct technical support. The scale of the threat is confirmed by numerous documented incidents in Italy involving this malware. After analyzing dozens of slightly varied samples, Cleafy researchers concluded that the developers are prepared to tailor their product for specific regions or client requirements.
The attack begins with a spoofed message, allegedly from the victim’s bank, sent via SMS or WhatsApp. It warns of a suspicious transaction and urges immediate action by calling a specified number. At this stage, the attackers aim to instill a sense of urgency, prompting the victim to act with less caution.
When the cardholder calls the provided number, a scammer impersonating a support agent answers. Through social engineering tactics, the attacker extracts the card number and PIN under the guise of “identity verification.” The next step involves persuading the victim to remove transaction limits via their banking app, significantly increasing the attackers’ ability to siphon funds.
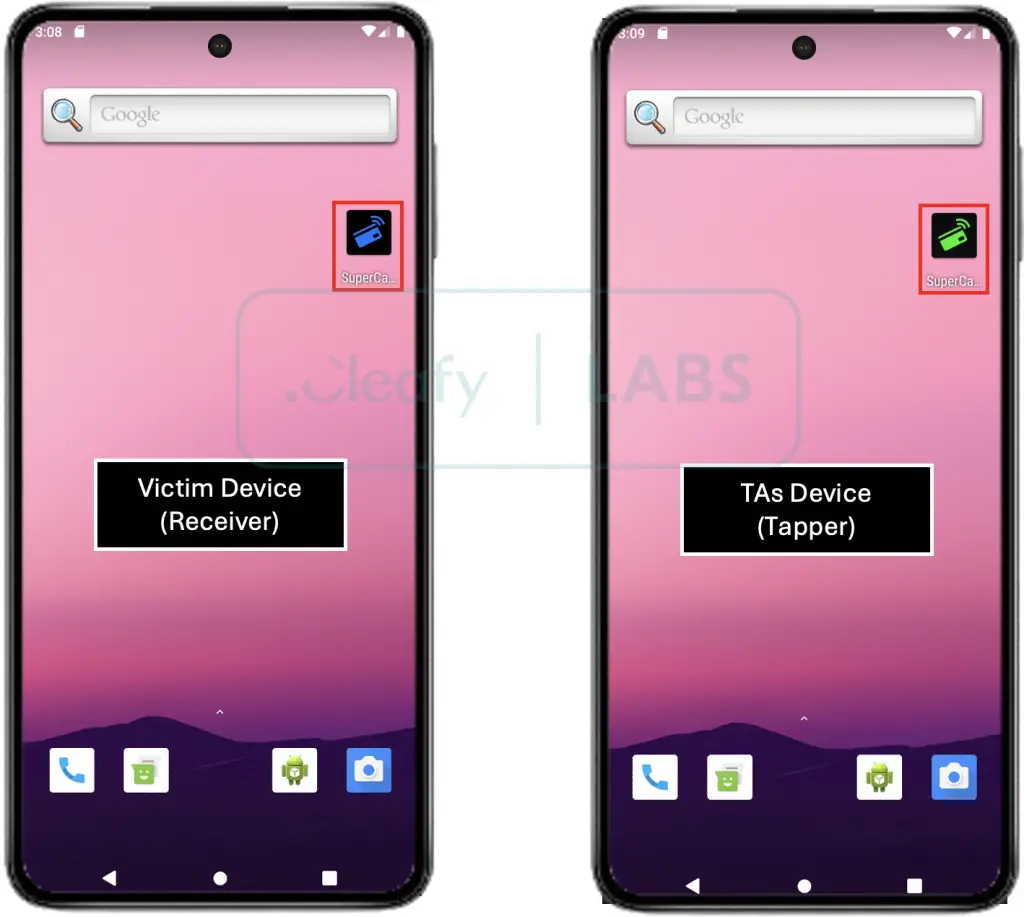
The scheme culminates in the installation of a special app called Reader, disguised as a security or verification tool. This app contains the malicious SuperCard X code. The developers exhibited notable ingenuity—Reader requests only minimal permissions, specifically access to the NFC module, which helps lull the user into a false sense of security. Yet, this access alone suffices for the attack.
Under the scammer’s instruction, the cardholder places their card near the phone “for verification.” At that moment, the application activates a process to extract data from the chip, which is then immediately transmitted to the attackers. On their Android device, they use a second application—Tapper—which creates a virtual replica of the stolen card using the captured data.
These “digital clones” enable contactless payments in retail settings and cash withdrawals at ATMs. Despite existing transaction limits, such operations are incredibly difficult to detect and reverse—they are processed instantly and appear fully legitimate to banking systems.
At the core of this malware lies the ATR (Answer to Reset) protocol—a standard mechanism triggered each time a card connects to a terminal. When the terminal sends a reset signal, the card must respond with a specific code confirming its authenticity. SuperCard X has mastered the ability to mimic these responses precisely, generating byte sequences identical to those from a genuine account.
What makes this threat particularly insidious is its sophisticated evasion techniques. At the time of analysis, no antivirus engine on VirusTotal was capable of detecting the threat. Unlike conventional malware that seeks broad permissions or overlays fake login screens atop banking apps to harvest credentials, SuperCard X requests virtually none—evading detection even by heuristic analysis, which examines apps based on behavioral patterns rather than known signatures.
The attackers also implemented a TLS-based authentication system—the same robust encryption standard used by banks and payment networks to secure online communications. All data exchanged between the malware and the attackers’ servers is encrypted using custom digital certificates. As a result, researchers are unable to intercept or decrypt the commands issued to SuperCard X, or the information it transmits back to its operators.
Responding to journalist inquiries, a Google representative confirmed that no applications containing such malicious code were present on the official Google Play Store. They emphasized, however, that Android device owners are by default protected by Google Play Protect, which warns users or blocks suspicious apps, even when installed from unofficial sources.


