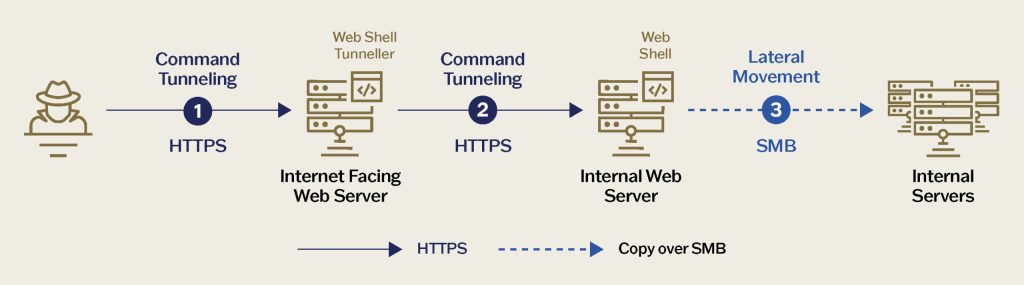
Web Shell Tunneling flow | Image: Sygnia
The Chinese cyber-espionage group Weaver Ant conducted a covert operation for over four years within the network of a major telecommunications provider in Asia. To obscure their presence and facilitate traffic routing, the attackers leveraged compromised Zyxel routers, deploying a concealed infrastructure through them.
Investigators from Sygnia, who led the incident response, observed the attackers’ resilience against multiple remediation attempts and noted their exceptional sophistication. The campaign began with the deployment of a modified, AES-encrypted version of the China Chopper web shell. Over time, the group escalated to more advanced tools, including INMemory, which executed payloads directly in server memory using an external library, eval.dll, to discreetly run code.
A defining feature of this campaign was its unique command-and-control architecture. Weaver Ant employed a method of web shell tunneling, whereby several shells, implanted across different servers, relayed encrypted commands among themselves. This approach allowed the attackers to incrementally advance deeper into the victim’s internal network, even reaching servers isolated from the internet. Each component in the chain functioned as a proxy, only processing payloads at its respective stage.
Simultaneously, the attackers established a proprietary relay network—ORB (Operational Relay Box)—built upon compromised home Zyxel routers. These devices served as gateways through which command-and-control traffic flowed between attacker servers and the internal web shells within the victim’s infrastructure.
To gather intelligence, the group relied on passive reconnaissance techniques to avoid detection, such as port mirroring and traffic collection without deploying agents. They also disabled system protections like Event Tracing for Windows (ETW) and the Antimalware Scan Interface (AMSI), minimizing the likelihood of defensive countermeasures identifying their activity.
Lateral movement was achieved through shared SMB resources and privileged accounts that had reused the same passwords for years. This granted the attackers access to configurations, logs, and other sensitive data crucial for navigating the environment and maintaining persistence.
Sygnia’s findings suggest the operation was aligned with state-sponsored espionage, focusing on the extraction of technical intelligence and the establishment of long-term access rather than data theft or financial gain. Supporting evidence of Chinese origin includes the use of tools previously attributed to Chinese actors, activity aligned with Asian time zones, and the choice of regionally prevalent router models.
To mitigate such threats, experts recommend restricting internal network traffic, enabling advanced logging for IIS and PowerShell, enforcing least-privilege access models, and regularly rotating passwords. Additionally, deploying signature-based detection for known web shells is essential for identifying intrusions in their early stages.


