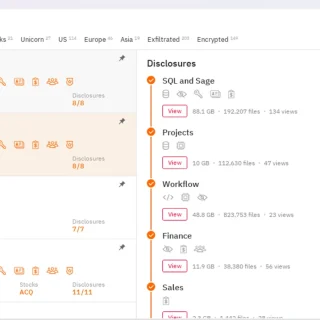
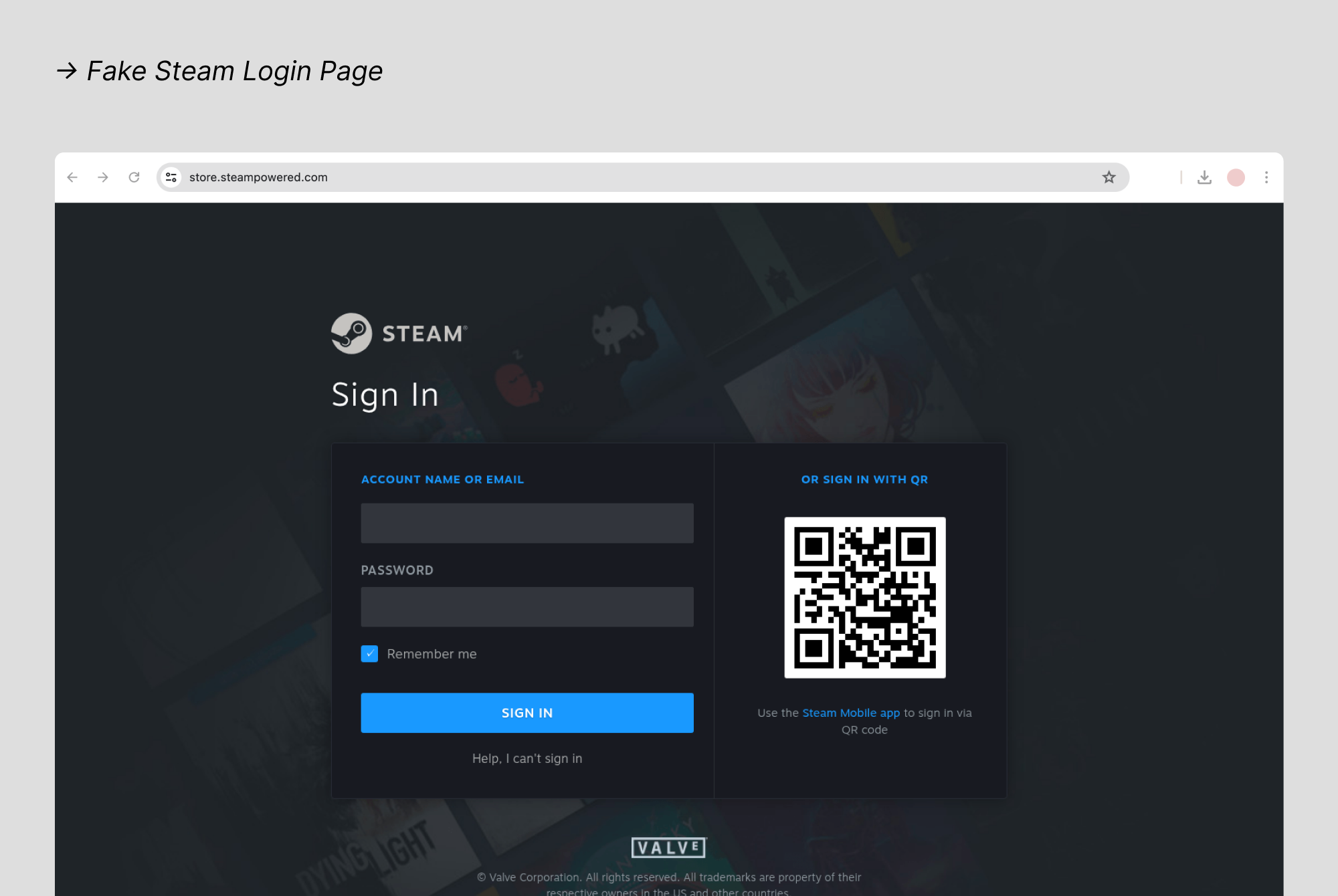
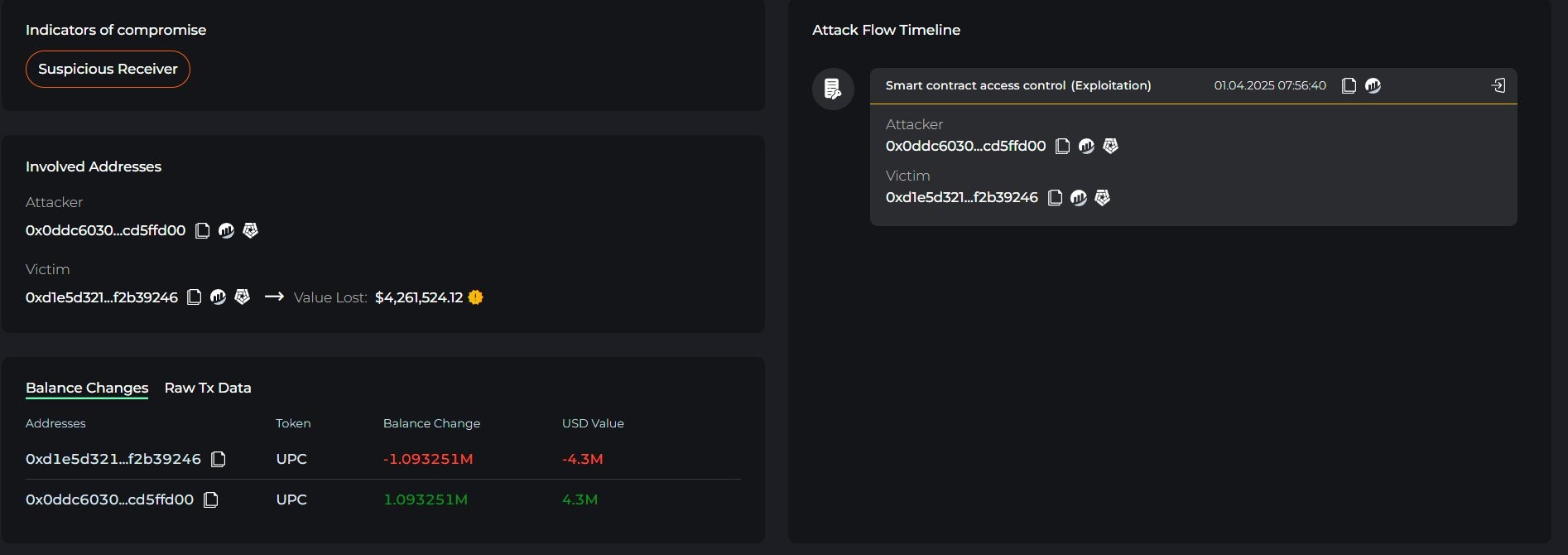
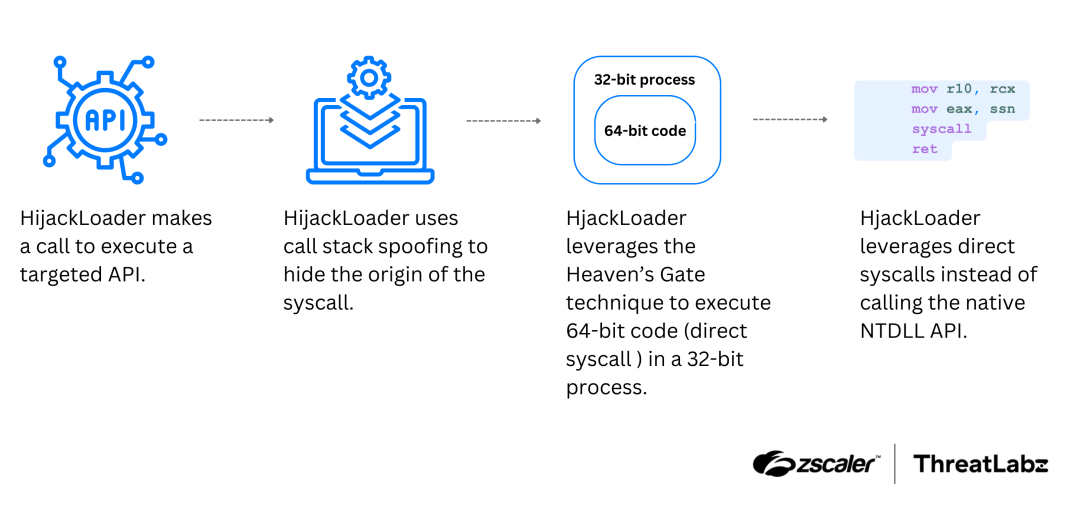
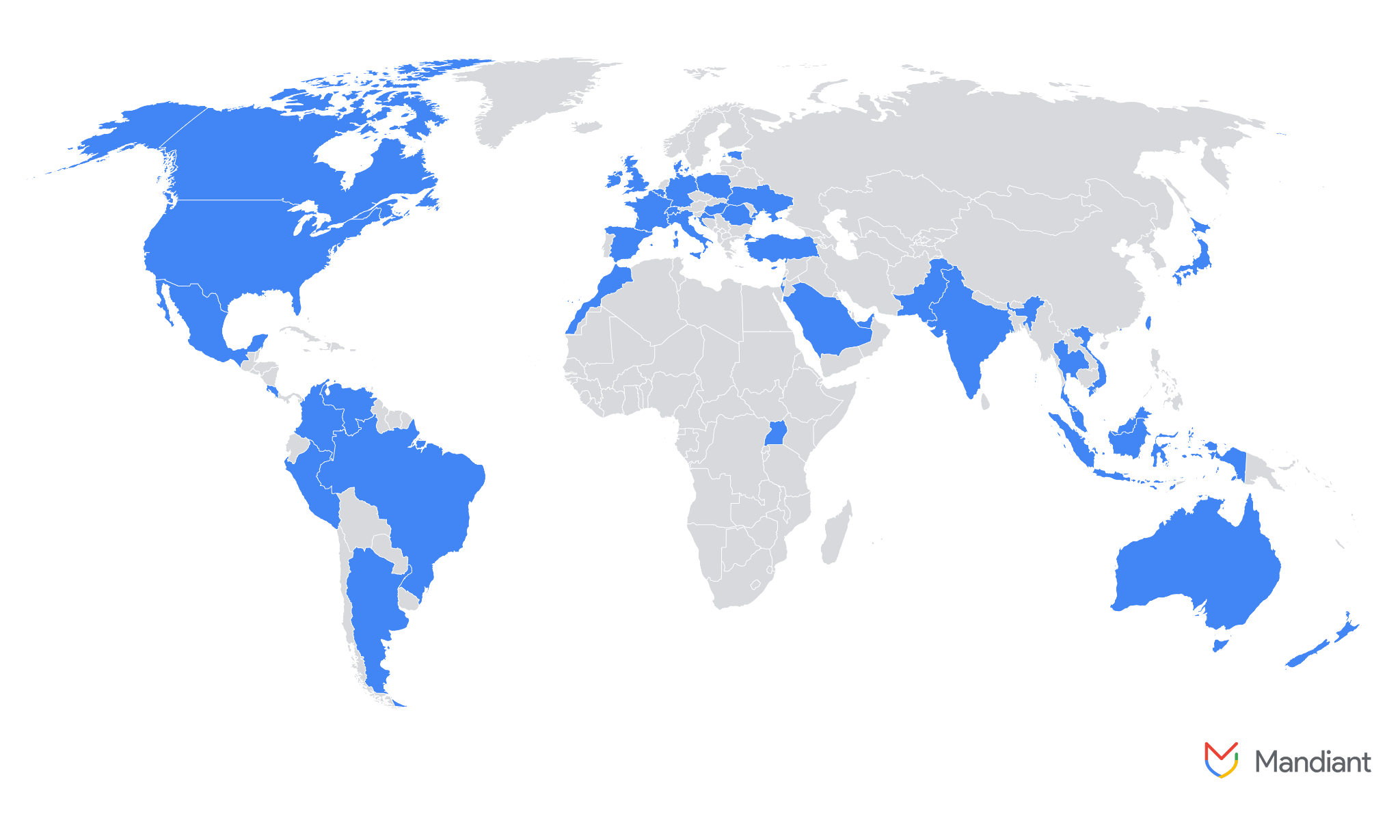
$80B AI Push Stalled: Microsoft’s Data Center Delays
In January of this year, Microsoft announced plans to invest $80 billion in data center construction by the end of fiscal year 2025, aiming to accelerate the training and deployment of artificial intelligence models....