A newly modified strain of the Mirai botnet has weaponized the CVE-2024-3721 vulnerability found in TBK DVR-4104...
cybersecurity
Operators of the Qilin ransomware group—also known under the alias Phantom Mantis—have begun actively exploiting critical vulnerabilities...
A new wave of cyberattacks has been recorded in Ukraine, targeting the destruction of critical infrastructure. At...
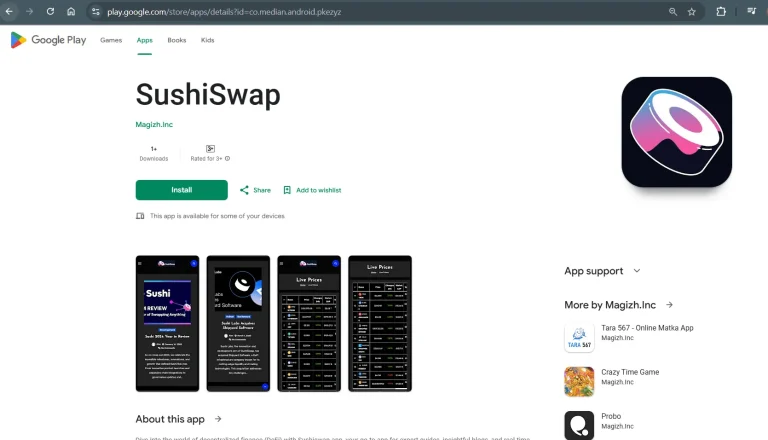
Even if you download applications exclusively from Google Play, this does not always guarantee safety—particularly when it...
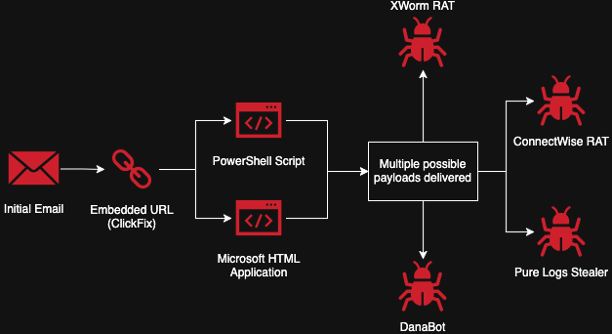
At first glance, it appears to be nothing more than a routine security check. In reality, it...
The KDE Project, a prominent force in the world of Linux desktops, has launched a campaign titled...
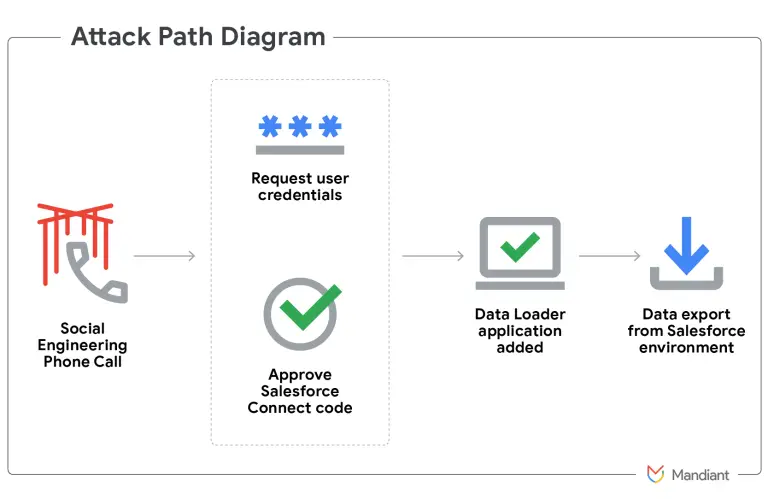
Hackers affiliated with the group UNC6040, tracked by Google’s Threat Intelligence Group, have been implicated in a...
Chinese state authorities have issued an unexpectedly harsh accusation against Taiwan, alleging that for several years, the...
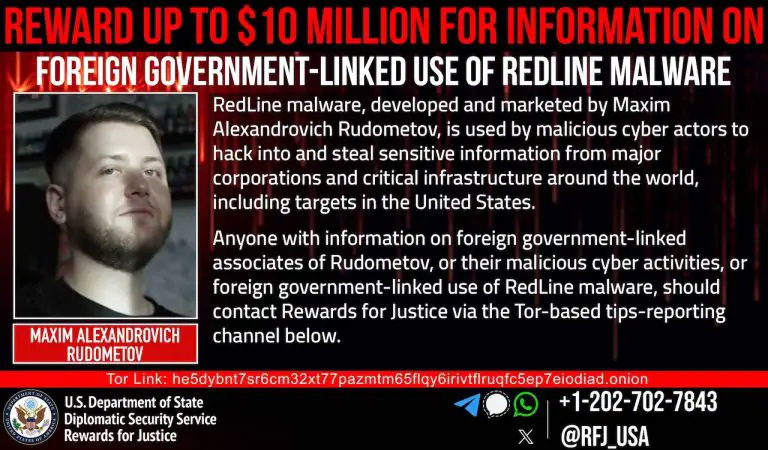
The U.S. Department of State has announced a reward of up to $10 million for information leading...
The Kettering Health network—encompassing hospitals, clinics, and medical centers throughout the state of Ohio—has yet to recover...
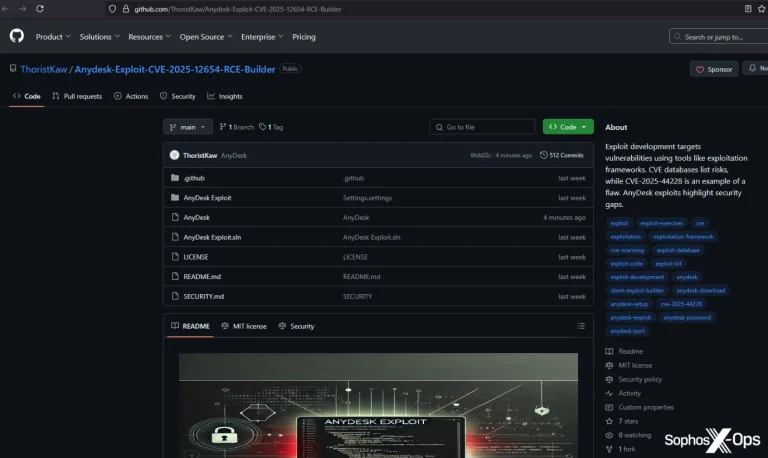
A recently uncovered malicious campaign is leveraging GitHub as a trap for security professionals, gamers, and even...
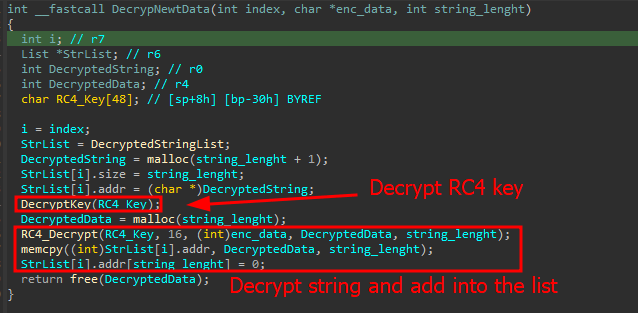
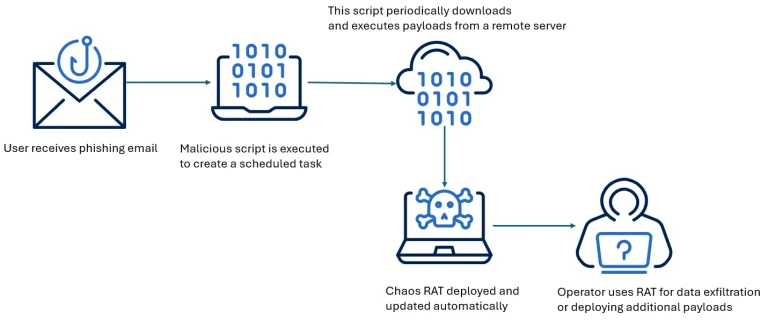
Amid a surge in cybercriminal activity, security experts have turned their attention to a new iteration of...
Mozilla has introduced a new protective mechanism aimed at combating malicious Firefox extensions that siphon cryptocurrency from...
Researchers from the DomainTools team have reported a new malicious campaign that leverages counterfeit websites masquerading as...
A critical vulnerability has been discovered in the widely used Roundcube webmail client—one that had remained undetected...