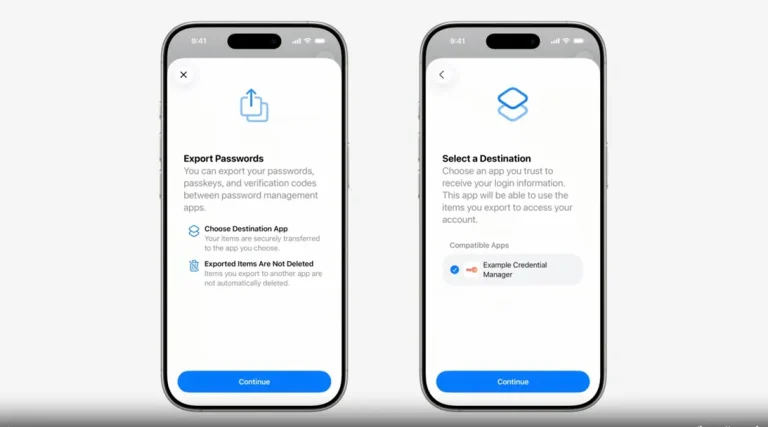
Apple has unveiled a pivotal innovation poised to eliminate one of the key obstacles hindering the widespread...
On Thursday afternoon, the internet experienced widespread disruptions affecting hundreds of services—from global platforms like Cloudflare to...
At the beginning of the year, Google announced its decision to develop Android entirely behind closed doors,...
Google has begun testing a new feature called Audio Overviews—spoken summaries of search results delivered through two...
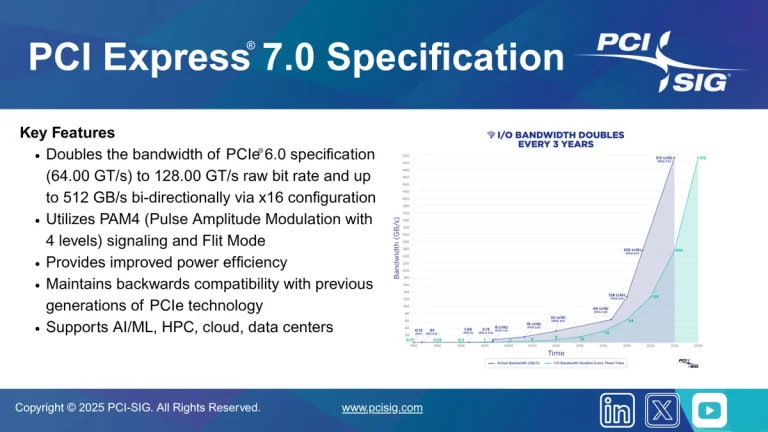
The PCI-SIG consortium, the industry body responsible for defining the PCIe standard, has officially released the PCIe...
Apple has quietly updated the security release notes for iOS 18.3.1, revealing that it has patched a...
Modern smartphones have transcended their original role as mere communication tools — they have become gateways for...
Despite the public collapse of the Black Basta syndicate following the leak of its internal chat logs...
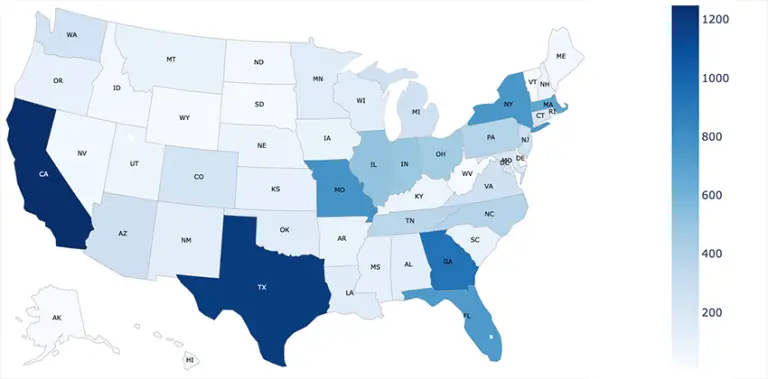
Bitsight has uncovered over 40,000 internet-connected surveillance cameras left completely unprotected—many of which could be accessed in...
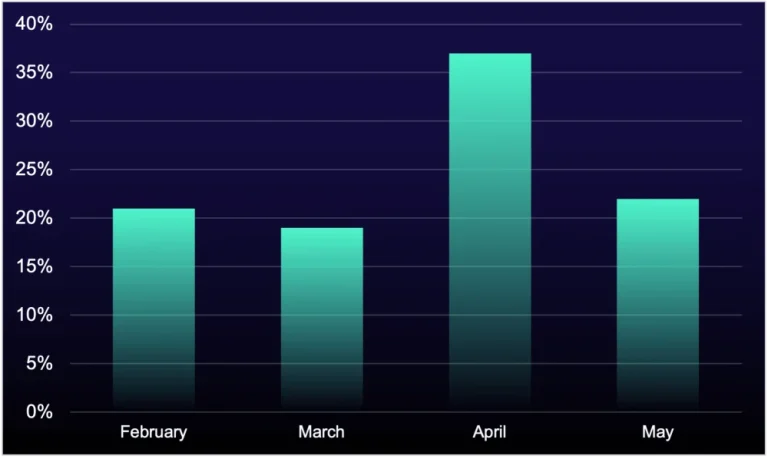
As the popularity of language models continues to surge, cybercriminals are increasingly exploiting this momentum to orchestrate...
Seven Asian nations have conducted a sweeping crackdown on transnational cyberfraud, arresting over 1,800 individuals and freezing...
Linux is not inclined toward impulsive experimentation—especially when it comes to enabling unfamiliar features in the kernel...
GPS trackers manufactured by the Chinese company SinoTrack have been found vulnerable to exploitation due to two...
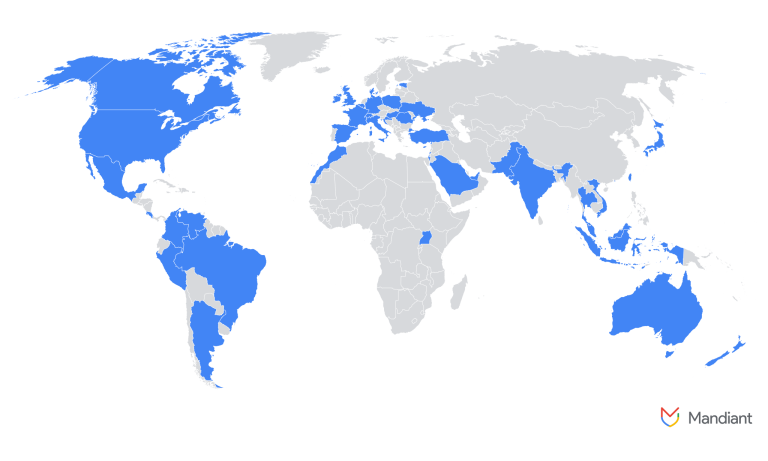
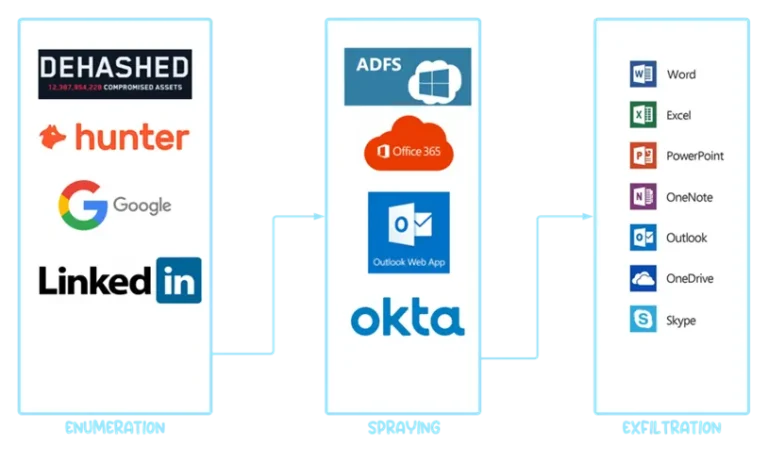
Hackers have compromised tens of thousands of corporate Microsoft Entra ID accounts by exploiting a tool originally...
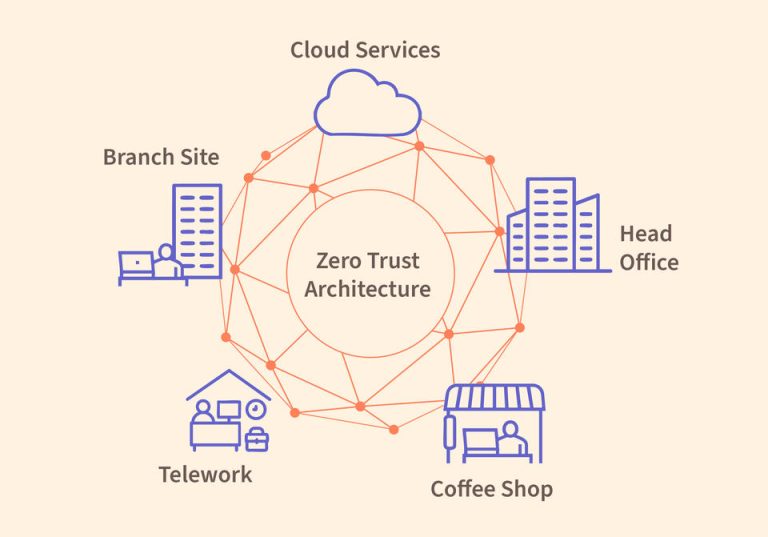
Traditional models for securing corporate networks are no longer adequate in the face of modern realities. In...