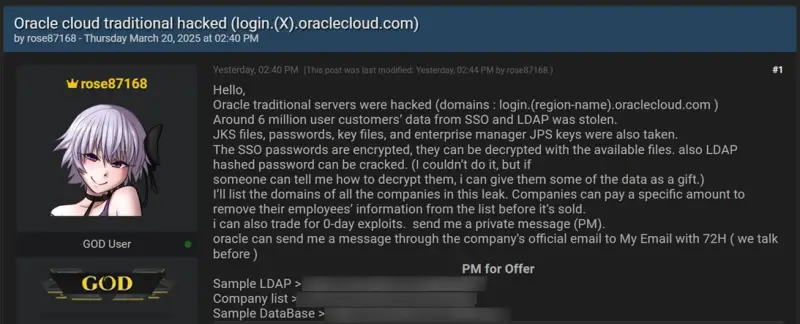
Oracle has found itself at the center of public scrutiny following claims by a hacker operating under the pseudonym “rose87168,” who alleges the theft of approximately six million user records from the company’s cloud service—a breach that could potentially impact up to 140,000 Oracle Cloud tenants.
Despite the gravity of these allegations, the vendor has formally denied any breach or compromise of its infrastructure, asserting that no indicators of unauthorized access or data leakage have been identified.
Nevertheless, according to cybersecurity firm CloudSEK, attackers did manage to gain access to the subdomain login[.]us2[.]oraclecloud[.]com, which hosted Oracle Fusion Middleware 11G. While the resource is now offline, an archived snapshot from the Wayback Machine dated February 17 confirms its previous existence.
Among the allegedly exfiltrated files are JKS files containing cryptographic keys, encrypted Single Sign-On (SSO) passwords, LDAP keys, and JPS keys from Oracle Enterprise Manager. CloudSEK reports that this data is currently being advertised for sale on dark web forums, including Breach Forums. Furthermore, the attacker is said to be extorting tenants—demanding ransom payments for the deletion of stolen data—and is offering incentives to individuals who assist in decrypting the compromised passwords.
Experts suspect the breach may have been facilitated via CVE-2021-35587, a known vulnerability in Oracle Access Manager, which is part of the Fusion Middleware suite. This vulnerability allows unauthenticated remote attackers to gain control over the system via HTTP access.
At risk are versions 11.1.2.3.0, 12.2.1.3.0, and 12.2.1.4.0 of the software. The flaw was added to the U.S. Cybersecurity and Infrastructure Security Agency’s Known Exploited Vulnerabilities (CISA KEV) catalog in December 2022. Particularly troubling is the fact that the targeted server had not been updated since September 27, 2014—indicating the use of outdated and highly vulnerable software.
CloudSEK underscores that the breach may have stemmed from poor patch management practices and insecure application architecture. Such flaws allow attackers to bypass authentication and move laterally within the cloud infrastructure.
Meanwhile, Oracle continues to categorically deny any incident has taken place. The company maintains that the credentials circulated online are unrelated to its cloud platform and affirms that none of its Oracle Cloud customers have reported any data leakage. These assertions stand in stark contrast to both the hacker’s claims and CloudSEK’s findings.
Should the breach prove genuine, the consequences could be far-reaching. The stolen JKS files, which contain cryptographic keys, are particularly dangerous, as they may be used to decrypt sensitive information and gain secondary access to systems. The compromise of SSO and LDAP credentials also raises the specter of cascading attacks against organizations relying on Oracle Cloud services.
CloudSEK recommends immediate remediation measures, including the rotation of credentials, a comprehensive forensic investigation with the involvement of cybersecurity professionals, and the strengthening of access controls and monitoring systems. Organizations are also urged to engage directly with Oracle to determine any possible exposure and ensure prompt incident response.


