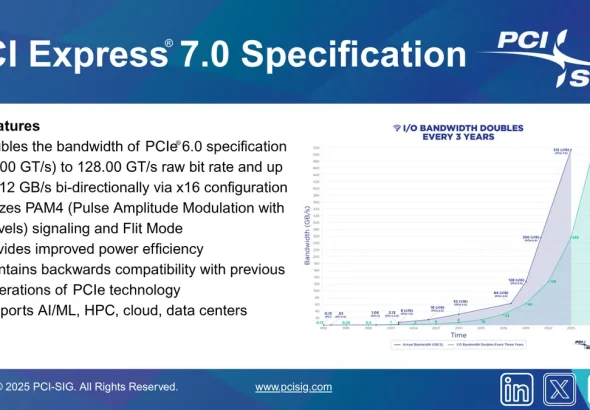
Veeam has issued an urgent security update to address a critical vulnerability in its Backup & Replication...
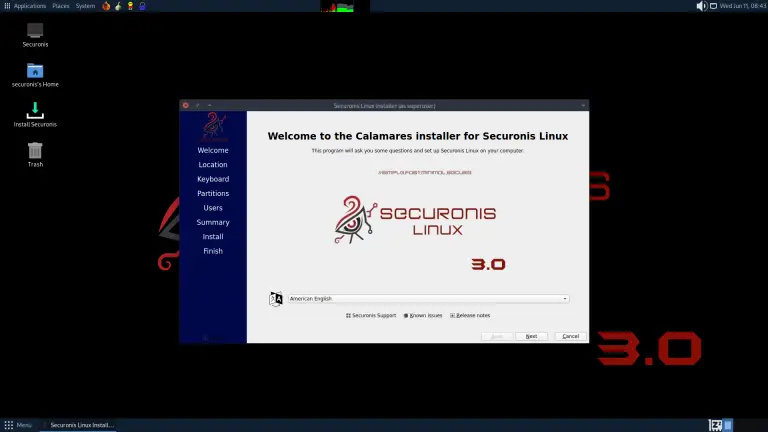
Securonis Linux has unveiled its most significant update to date — version 3.0, codenamed “Darkcloux,” along with...
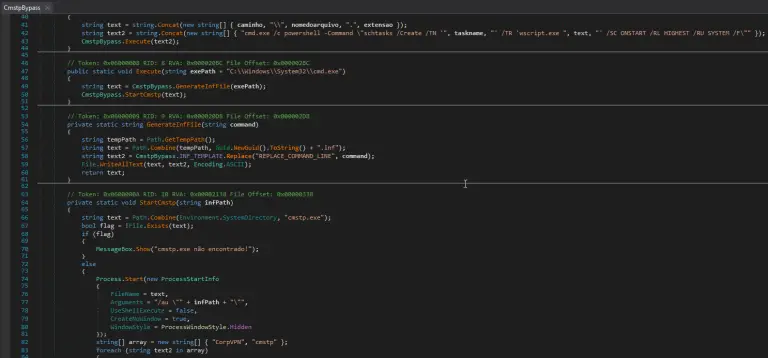
Amid intensifying competition among cybercriminals for the theft of confidential data, a new player emerged in 2025—Katz...
In the spring of 2023, the crypto market witnessed a tale steeped in exploitation, blackmail, and an...
Over the past academic year, the number of British students caught using artificial intelligence to cheat has...
The cybercriminal group Scattered Spider has shifted its focus, redirecting its malicious efforts from the retail sector...
A critical vulnerability has been identified in ASUS’s Armoury Crate software, allowing threat actors to escalate privileges...
The X.Org Server project found itself in the spotlight this week — not for unveiling new features,...
Germany is making a bold leap toward digital sovereignty: the federal state of Schleswig-Holstein is officially abandoning...
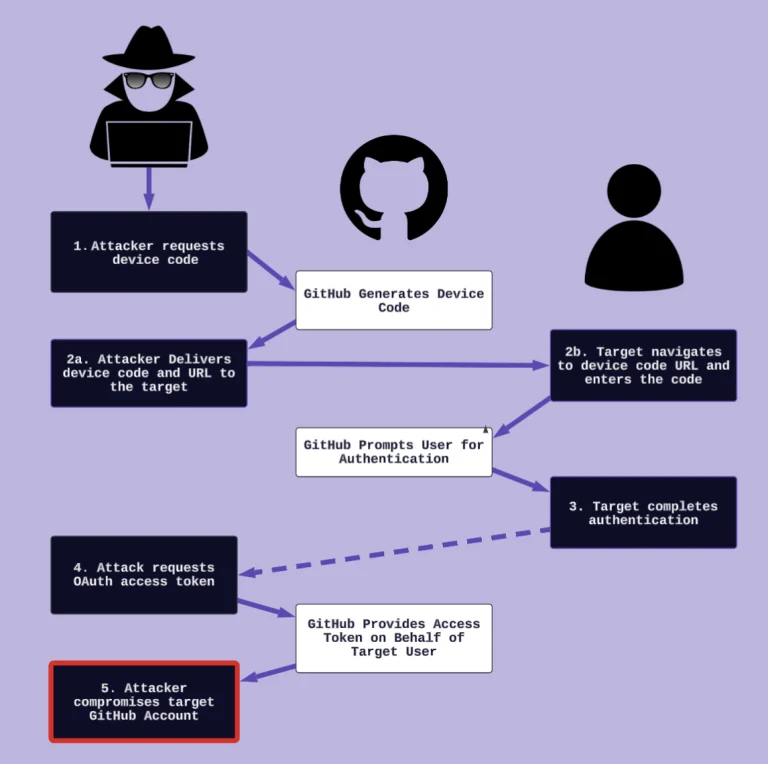
In recent times, cybercriminals have increasingly shifted their focus from deploying malware to employing subtle manipulations rooted...
Kali Linux 2025.2 Unleashed: Redesigned Interface, Automotive Hacking & Wi-Fi Attacks via Smartwatch


Kali Linux 2025.2 Unleashed: Redesigned Interface, Automotive Hacking & Wi-Fi Attacks via Smartwatch
Half of 2025 has passed, and the Offensive Security team has unveiled a major update to its...
Amid a surge in increasingly sophisticated software supply chain attacks, cybersecurity experts have identified a new wave...
Google Cloud Postmortem: Quota Bug Triggered Global Outage, Hitting Cloudflare & Discord for 3 Hours


Google Cloud Postmortem: Quota Bug Triggered Global Outage, Hitting Cloudflare & Discord for 3 Hours
Last week, the global internet landscape experienced a wave of instability—services like Cloudflare, Spotify, Discord, Snapchat, Twitch,...
The conflict between Iran and Israel is unfolding not only on land and in the skies, but...
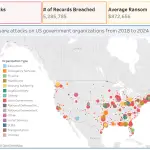
Two Democratic lawmakers in Congress have formally called upon the U.S. Government Accountability Office (GAO) to conduct...