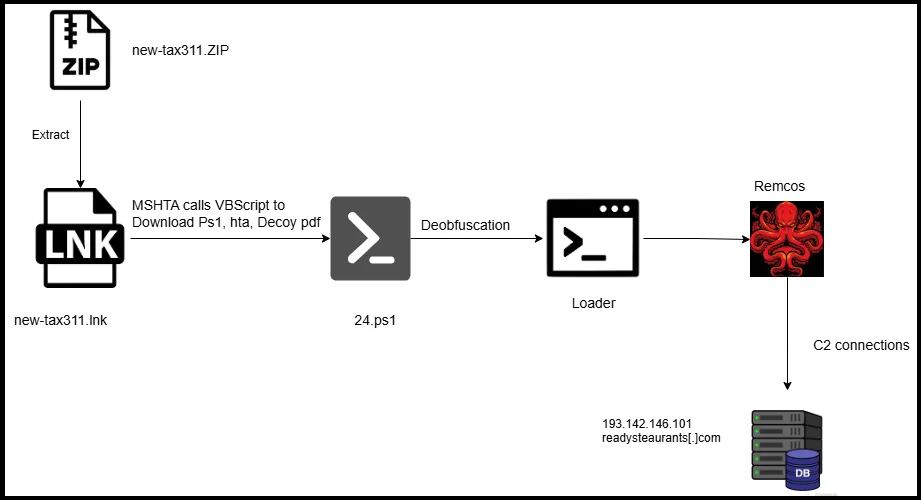
Researchers at Qualys have issued a warning about a new malicious campaign that leverages a PowerShell script to deploy the Remcos Remote Access Trojan (RAT). The infection vector relies on ZIP archives disguised as tax documents — within these archives lie LNK files masquerading as shortcuts to legitimate Office documents.
In the initial phase of the attack, a legitimate Windows system component — mshta.exe, used to execute HTML Applications (HTA) — is exploited. Through it, a remote HTA file named xlab22.hta is fetched, containing VBScript code. This script proceeds to download a PowerShell payload, a decoy PDF document, and another HTA file — 311.hta — which is subsequently registered in Windows startup via system registry modifications.
Upon execution, the PowerShell script unpacks and triggers a shellcode loader, which injects Remcos RAT directly into memory, thereby circumventing disk-based detection. This fileless approach allows the malware to evade the majority of antivirus solutions. Remcos RAT is a well-known surveillance tool capable of a broad range of remote control functions — from keylogging and screenshot capture to clipboard monitoring and process enumeration. Command and control is maintained via a secured TLS connection to the server readysteaurants[.]com.
The trend of deploying Remcos RAT through fileless methods is not new. As early as November 2024, researchers at Fortinet documented a similar campaign that used delivery-themed lures to entice victims into opening attachments that executed malicious code entirely in memory.
According to Qualys analysts, the combined use of PowerShell, LNK shortcuts, and mshta.exe signifies a shift toward “surgically precise” attacks designed to bypass both signature-based and behavioral detection mechanisms. Organizations lacking attachment control mechanisms and real-time PowerShell monitoring remain especially vulnerable.
Modern attack strategies increasingly rely on legitimate system utilities, repurposing standard Windows components as conduits for malware delivery. This underscores the critical need for a layered defense approach: filtering attachments at the email gateway, monitoring PowerShell activity, and restricting the execution of scripts via mshta.exe within enterprise environments.


