Over the past two years, employees of American law firms have increasingly fallen prey to an expansive and sophisticated social engineering campaign orchestrated by the extortionist group known as Luna Moth.
The Federal Bureau of Investigation (FBI) has issued an official advisory following a spate of attacks in which threat actors, masquerading as IT support personnel, gain remote access to employee workstations and exfiltrate confidential data for blackmail purposes.
Also operating under the aliases Chatty Spider, Silent Ransom Group (SRG), Storm-0252, and UNC3753, the group has been active since 2022. Their primary tactic remains callback phishing—also referred to as TOAD (Telephone-Oriented Attack Delivery)—a scheme involving phone-based deception. Victims receive emails purporting to be about canceling paid subscriptions, accompanied by a phone number to call immediately to avoid automatic charges. Upon calling, victims are connected with fake “support representatives” who persuade them to install remote access tools—thus opening the door to unauthorized entry.
Once access is gained, Luna Moth operatives proceed to steal sensitive files, followed by extortion demands. Victims who refuse to comply are threatened with public exposure or sale of the stolen data to other cybercriminals. Notably, the attackers often employ legitimate file-transfer utilities like WinSCP and Rclone—tools that typically evade antivirus detection due to their benign appearance.
Since March 2025, the group has shifted tactics: attackers now call employees directly, impersonating in-house IT staff. They request victims to join remote sessions either through emailed links or via specially crafted websites. Under the guise of performing “overnight maintenance,” they seize device control, escalate privileges, and begin data exfiltration.
According to the FBI, these new attacks rely heavily on legitimate administrative tools such as Zoho Assist, Syncro, AnyDesk, Splashtop, and Atera—methods that allow stealthy operation while bypassing traditional threat detection systems. In cases where administrative access is not granted, attackers use portable versions of WinSCP, which require no installation or elevated permissions.
The FBI urges organizations to watch for key indicators of compromise: outbound connections from WinSCP or Rclone to unfamiliar IP addresses, unexpected emails from unknown sources threatening data exposure, suspicious subscription-related messages urging a phone call, and unsolicited calls from supposed “IT staff.”
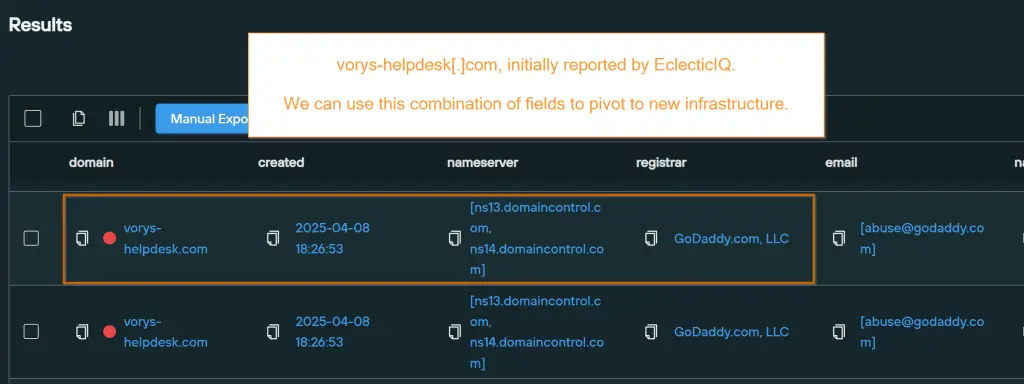
Complementing the FBI’s warning, cybersecurity firm EclecticIQ published its own analysis emphasizing Luna Moth’s aggressive focus on U.S.-based legal and financial sectors. Attackers have leveraged platforms like Reamaze Helpdesk and other remote-access software in their operations. In March alone, the group registered at least 37 deceptive domains via GoDaddy, imitating the IT portals of targeted firms.
Silent Push notes that these domains often began with the victim organization’s name and ended in phrases such as “-helpdesk.com.” A small number of domain registrars and DNS providers were favored—chief among them, “domaincontrol[.]com.”
Through the continual evolution of its attack methodologies and the cunning deployment of legitimate tools, Luna Moth has emerged as one of the most prominent extortion groups in recent times. Legal and financial institutions are strongly advised to fortify internal verification procedures and implement strict controls over the use of remote access software and data transmission beyond corporate networks.


