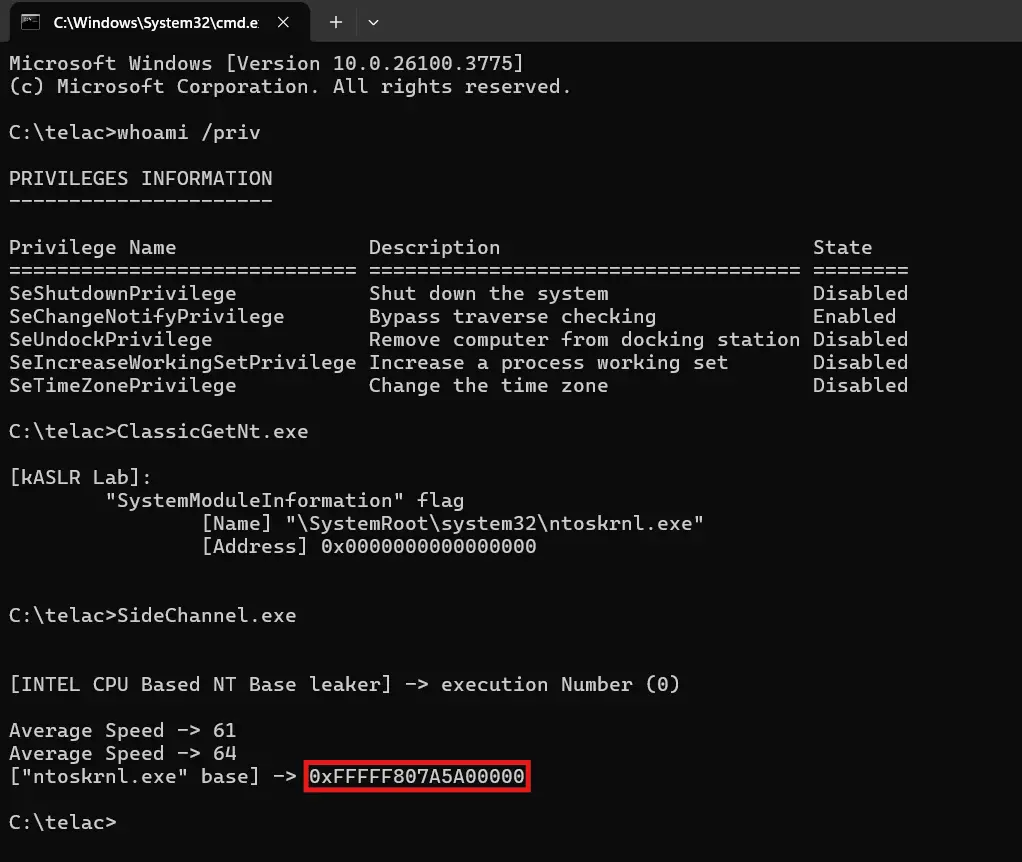
Security researchers have unveiled a method for circumventing KASLR—one of the kernel’s principal defense mechanisms—on fully updated Windows 11 systems. This attack leverages side-channel analysis based on CPU cache timing, enabling an unprivileged user to determine the precise load address of ntoskrnl.exe, the core executable of the Windows kernel.
Kernel Address Space Layout Randomization (KASLR) was implemented by Microsoft as a safeguard against attacks targeting direct kernel access. It randomizes the memory addresses of kernel components, making memory structure prediction—and thus successful exploitation—significantly more difficult. Yet, this newly demonstrated technique proves that even without administrative privileges, KASLR can be bypassed with alarming precision.
At the heart of the attack lies the Prefetch Side-Channel technique, initially described on the exploits-forsale forum. The method exploits speculative execution—a performance-boosting architectural feature of modern Intel processors—where instructions are executed in advance, leaving measurable traces in the CPU cache. These residual traces can be analyzed to infer which memory addresses the system accesses most frequently, including that of the kernel’s load address.
The attack is carried out using prefetchnta and prefetcht2 instructions, which prompt the CPU to preload specified memory addresses into its L1, L2, or L3 caches. Then, using the rdtscp instruction to precisely measure access latency, the attacker identifies whether the address was cached—lower latency indicating a cached address. By iterating this process across a range of 32,768 possible addresses, the attack reveals the region most frequently cached—i.e., the kernel’s location.
To enhance accuracy, the researchers employ response time averaging, filtering out statistical noise with mathematical thresholds. They also use the mfence and lfence instructions to suppress compiler and architectural optimizations that could distort timing measurements. This multifaceted manipulation of the cache and speculative execution makes the attack technically intricate yet reproducible.
Previously, researchers from ETH Zurich uncovered the Branch Privilege Injection vulnerability (CVE-2024-45332), which exploited flaws in branch predictor logic to extract sensitive data from the kernel. Unlike that attack, which aimed to read protected memory contents, the Prefetch Side-Channel method is designed to identify the base address of the Windows kernel. While both exploit speculative execution and Intel CPU vulnerabilities, their objectives diverge: one exposes the kernel’s location, the other its contents.
What makes the Prefetch Side-Channel particularly compelling is its ability to bypass restrictions introduced in Microsoft’s 24H2 update—specifically, limitations on using NtQuerySystemInformation. As a result, even without SeDebugPrivilege, it is now possible to obtain data that was previously deemed inaccessible under KASLR protections.
It is worth noting, however, that the effectiveness of this technique diminishes in virtualized environments like VMware. This is due to the use of Second-Level Address Translation (SLAT), which disrupts cache behavior and breaks the correlation between memory access and timing.
Although no real-world attacks using this method have been observed to date, its mere existence underscores a latent weakness in modern CPU architecture and the critical need for deeper security integration between hardware and operating systems. This discovery serves as a stark reminder of the ongoing arms race between the architects of defense mechanisms and the researchers probing their limits.


