A group of European white-hat hackers from the Budapest-based company PCAutomotive has demonstrated a remote hack of a 2020 Nissan LEAF electric vehicle. They managed not only to seize control of the steering wheel while the car was in motion but also to track the vehicle in real time, read text messages, record in-cabin conversations, and broadcast sounds through the car’s speakers — all achieved using a homemade simulator assembled from components purchased on eBay.
The research was presented at Black Hat Asia 2025 in the form of a 118-page technical report. The presentation meticulously details the construction of the testing platform and the exploitation of various vulnerabilities, including the use of a DNS-based C2 channel and the Bluetooth protocol. The demonstration highlighted how easily such an attack can be executed with minimal equipment and basic technical skills.
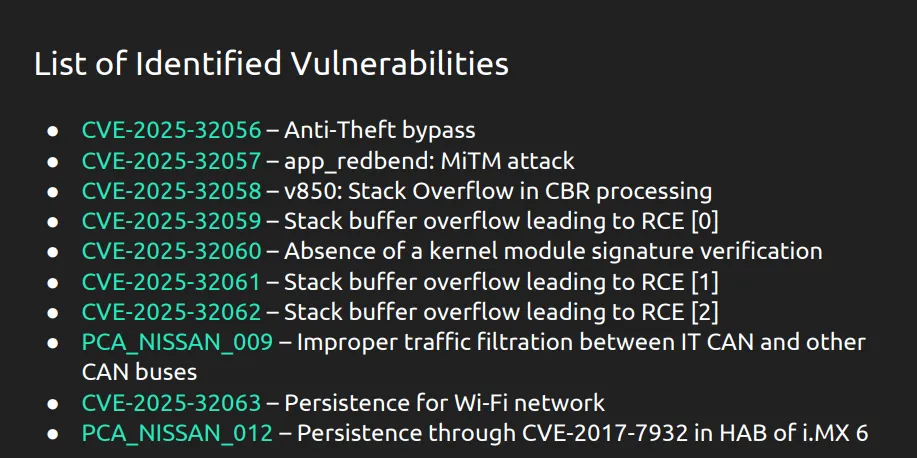
Among the disclosed vulnerabilities were: a bypass of the anti-theft system (CVE-2025-32056), a man-in-the-middle attack via the app_redbend component (CVE-2025-32057), a stack overflow during CBR processing (CVE-2025-32058), multiple RCEs via buffer overflows (CVE-2025-32059, -32061, -32062), a lack of digital signature verification for kernel modules (CVE-2025-32060), vulnerabilities enabling persistence through Wi-Fi connectivity (CVE-2025-32063) and the i.MX 6 bootloader (PCA_NISSAN_012), as well as improper traffic filtering between CAN buses (PCA_NISSAN_009).
According to PCAutomotive, all vulnerabilities were disclosed to Nissan and its suppliers between August 2, 2023, and September 12, 2024. However, the source does not specify whether or how these issues were remediated. A video has also been released, demonstrating the hack in action.
What drew particular concern was the researchers’ ability to remotely turn the steering wheel while the vehicle was moving — underscoring the gravity of risks posed by network-based vulnerabilities in electronically controlled vehicles.
According to the team, the approach illustrates how a remote operator could potentially connect to and control a vehicle in complex or unexpected scenarios. Yet the researchers stress that the invasion of privacy — including interception of messages and conversations — represents an equally severe threat.
In conclusion, the team reminds us: in a world where the automobile increasingly resembles a computer on wheels, every process may be silently observed by an unseen actor.


