The Gootloader malware campaign has once again drawn attention — this time, the attackers have adopted a more sophisticated strategy by distributing malicious advertisements via the Google Ads platform. Their primary targets are legal professionals searching for document templates, which now conceal a malicious JavaScript payload.
A researcher specializing in Gootloader activity and author of the blog “Gootloader Details” discovered that a British company’s ad account, Med Media Group Ltd., was used to disseminate the malicious code. According to his findings, the threat actors acquired a domain, configured hosting, and established infrastructure through Cloudflare, effectively masking the true origin of the operation.
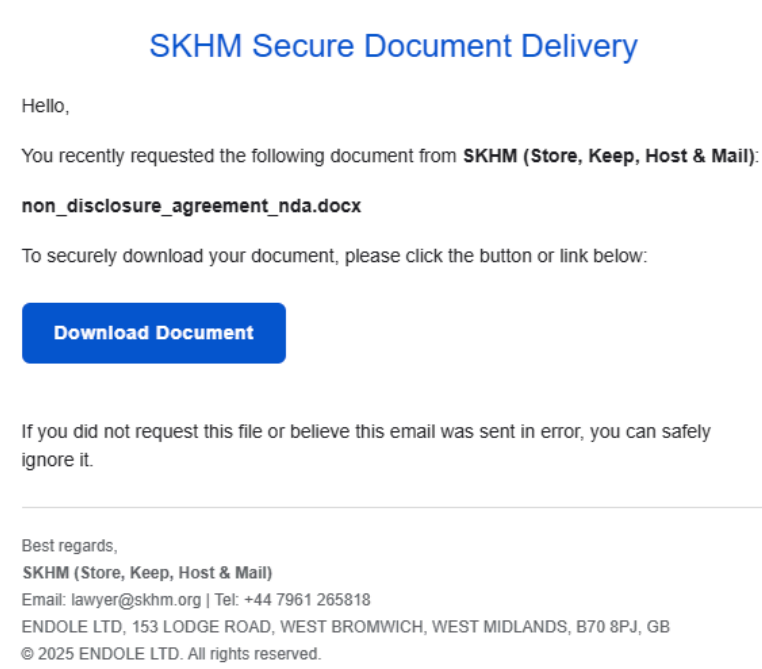
At first glance, the advertisement appears to offer popular legal templates — such as nondisclosure agreements. Users are directed to “lawliner[.]com,” a website under the attackers’ control. There, they are prompted to enter their email address, to which a supposed document is later sent.
The attached file is a compressed archive containing a JavaScript file disguised as a legal template. Upon extraction and execution, the script activates malicious code that creates a scheduled task within the system. This task executes a PowerShell script that gathers system information — including running processes, desktop files, environment variables, and available disk space.
The data is exfiltrated to a network of domains, some of which are compromised WordPress blogs that redirect the information to the attackers’ command-and-control infrastructure. Others are spoofed domains crafted to resemble legitimate services but serve solely to facilitate the data transfer.
Previously, the group employed SEO poisoning, leveraging compromised WordPress sites to appear prominently in search results for legal-related queries. Now, however, they have shifted to paid advertising, broadening their reach and enabling more precise targeting of victims.
The legal sector remains a highly lucrative target for such attacks — law firms manage sensitive client data, deal information, signed contracts, and personal details of high-profile individuals. The leakage of this data may enable blackmail or lead to further, more damaging intrusions.
Gootloader, originally part of the GootKit malware family, emerged in 2014. Its activity surged in 2020, particularly in pre-ransomware campaigns. It often deploys an additional component, GootBot, which expands the attacker’s capabilities by enabling remote code execution and further malware deployment.
Beyond targeting legal professionals, the operators have previously employed SEO poisoning against a variety of seemingly unrelated groups — including, surprisingly, Bengal cat enthusiasts in Australia. In the current wave of attacks, the domains “lawliner[.]com” and “skhm[.]org” have been identified as key indicators of compromise. Experts recommend blocking and monitoring these domains in network traffic, as well as conducting retrospective analysis of any related activity.
Gootloader’s adaptability and evolving tactics make it particularly dangerous. Its use of paid ads, dedicated infrastructure, and strategic focus on the legal industry highlight a high level of operational maturity. Timely detection of such advertisements and proactive filtering of malicious domains remain vital defenses against this evolving threat.


