The financially motivated hacking collective FIN6 has resurfaced with a sophisticated phishing campaign that leverages counterfeit resumes hosted on Amazon Web Services infrastructure. The objective of this operation is the dissemination of the More_eggs malware—a malicious implant long associated with the cybercriminal syndicate known as Golden Chickens, also referred to as Venom Spider.
Known by a multitude of aliases—Camouflage Tempest, Gold Franklin, ITG08, Skeleton Spider, and TA4557—FIN6 has operated since 2012. Its origins trace back to intrusions targeting point-of-sale systems in the hospitality and retail sectors, aimed at harvesting payment card data. Over time, the group evolved its techniques to include Magecart-style JavaScript skimmers, compromising e-commerce platforms to siphon financial information.
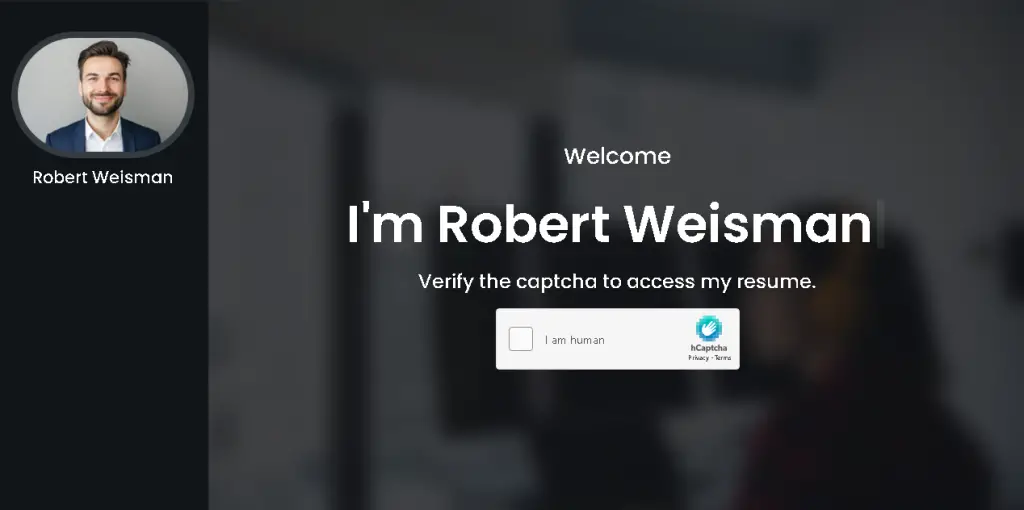
In this latest campaign, the threat actors adopted a professional façade, exploiting career platforms such as LinkedIn and Indeed. Posing as job applicants, they initiated contact with recruiters, expressed interest in vacancies, and shared links to alleged personal portfolio websites. These links, however, led to ZIP archives embedded with More_eggs malware.
The domains used in this campaign—such as bobbyweisman[.]com and ryanberardi[.]com—were registered via GoDaddy with anonymized WHOIS data, complicating attribution and takedown efforts. This obfuscation is a hallmark of FIN6’s operational security practices, designed to delay detection and response.
More_eggs is a JavaScript-based backdoor that grants stealthy access to infected machines, facilitates credential theft, and acts as a launchpad for follow-up attacks, including ransomware deployment. While developed by Golden Chickens, FIN6 has adopted it as its preferred initial access vector—according to Visa, this has been their modus operandi since at least 2018.
The group’s latest activity showcases a marked enhancement in evasion techniques. Malicious payloads are now hosted on trusted AWS services, including EC2 and S3, and are distributed via websites with embedded traffic filtering logic. Visitors are first prompted with a CAPTCHA challenge; their IP address and browser fingerprint are then evaluated. Only users with residential IP addresses and standard Windows browsers are served the infected file—others receive a benign résumé.
This meticulous filtering severely impedes automated detection systems. Corporate scanners, VPN-based traffic, and cloud-hosted analysis tools typically encounter only harmless content, allowing FIN6 to extend the lifespan and efficacy of its campaigns.
According to DomainTools, this operation exemplifies how deceptively simple phishing tactics can achieve alarming potency when combined with legitimate cloud infrastructure and low-cost, highly effective evasion strategies. The fusion of social engineering, CAPTCHA barriers, and cloud-based hosting elevates otherwise rudimentary attacks into formidable cybersecurity threats.


