Linux kernel developer Greg Kroah-Hartman has announced the release of three new kernel updates: Linux 6.14.11, Linux...
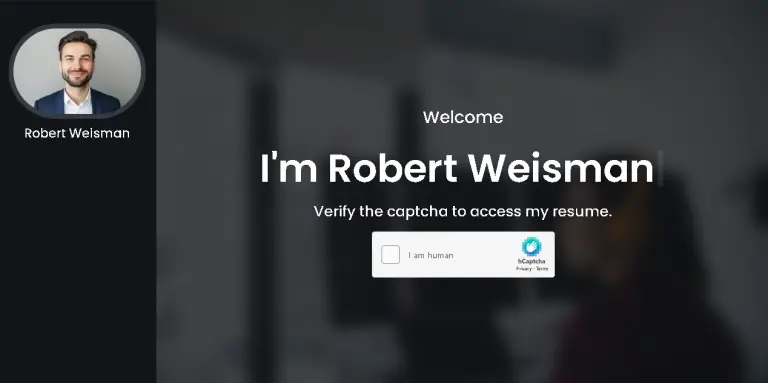
The financially motivated hacking collective FIN6 has resurfaced with a sophisticated phishing campaign that leverages counterfeit resumes...
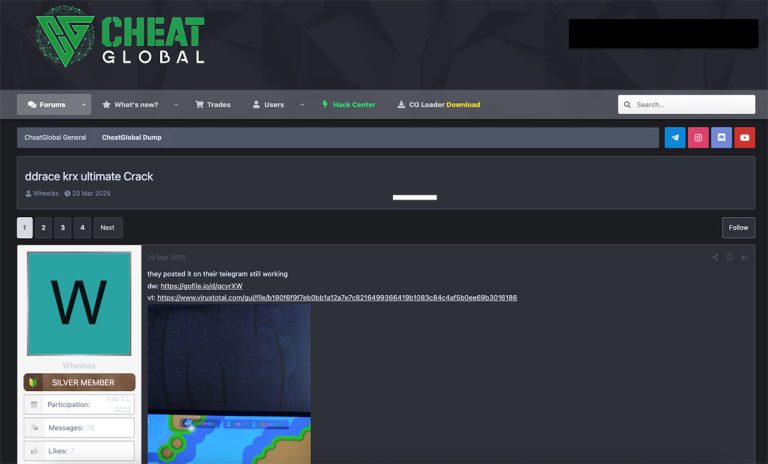
Cybersecurity specialists at Trellix have uncovered a previously undocumented malware strain written in Rust, dubbed Myth Stealer,...
Beginning in July 2025, Microsoft will automatically block email attachments with the extensions .library-ms and .search-ms in...
Adobe has released a sweeping security update, addressing a staggering 254 vulnerabilities across its product suite. The...
At Monday’s presentation, Apple unveiled a new open-source initiative—an innovative framework that enables the execution of Linux...
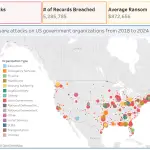
Five men have pleaded guilty to their roles in a sweeping money laundering scheme involving nearly $37...
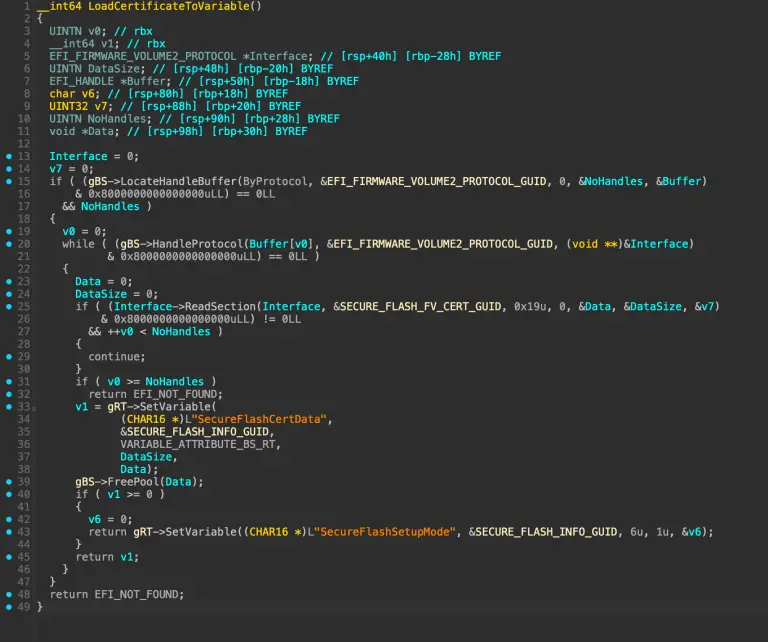
Nearly all modern computers with Secure Boot enabled have been exposed to critical risk due to a...
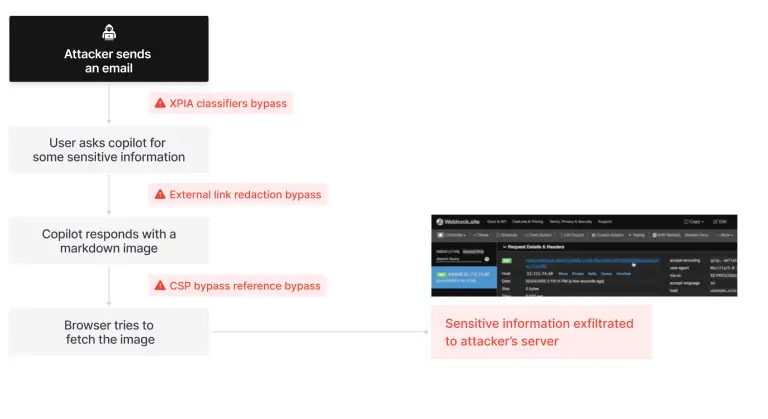
Researchers have, for the first time, identified a zero-click vulnerability tied to artificial intelligence—one capable of leaking...
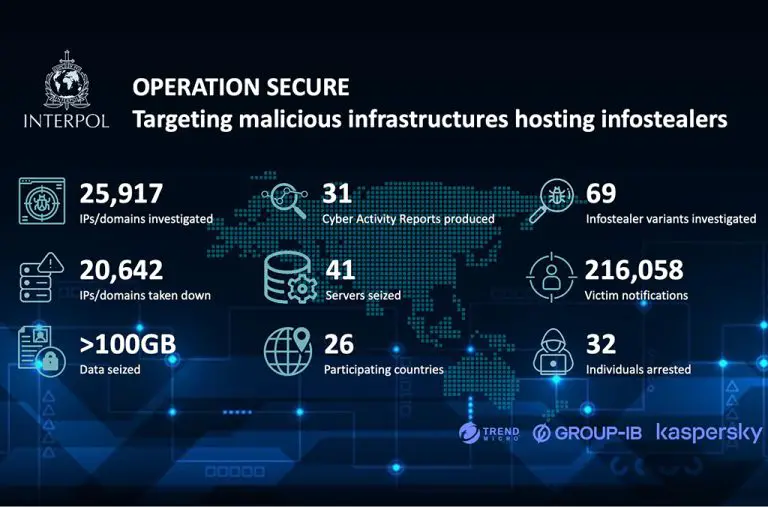
An international law enforcement operation, codenamed Operation Secure, has culminated in the large-scale dismantling of cybercriminal infrastructure...
During the keynote address at WWDC 2025, Apple adopted a notably restrained tone regarding the new iteration...
Nintendo has announced that its latest gaming console, the Nintendo Switch 2—launched on June 5 across Japan,...
Tesla CEO Elon Musk recently announced that the company’s autonomous taxi service (robotaxi) is tentatively scheduled to...
The June edition of Microsoft’s Patch Tuesday security updates included fixes for 66 vulnerabilities. Among them, one...
The United Kingdom’s National Health Service (NHS) has issued an urgent appeal to residents of England, calling...