Obsolete routers are once again under siege — cybercriminals are transforming outdated devices into covert proxy nodes,...
Ubuntu 25.10, scheduled for release on October 9, 2025, will mark a historic milestone as the first...
Somewhere deep within the recesses of Windows, a relic of the early 1990s still endures — a...
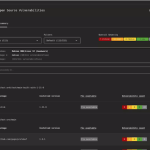
Cisco has issued an urgent security update to address a critical vulnerability in wireless controllers running IOS...
According to a report by The Information, Meta initially intended to equip its smart glasses with facial...
The U.S. Federal Trade Commission (FTC) previously filed multiple appeals against Microsoft’s acquisition of Activision Blizzard, citing...
The United States Patent and Trademark Office has recently denied Tesla’s application to trademark the term “Robotaxi,”...
Sony has announced that teamLFG—a studio incubated by Bungie and headquartered in Bellevue, Washington—will officially join the...
Nintendo recently released its financial results for fiscal year 2025, covering the period from April of the...
The Chosun has obtained reports indicating that Intel has signed a substantial chip foundry agreement with Microsoft,...
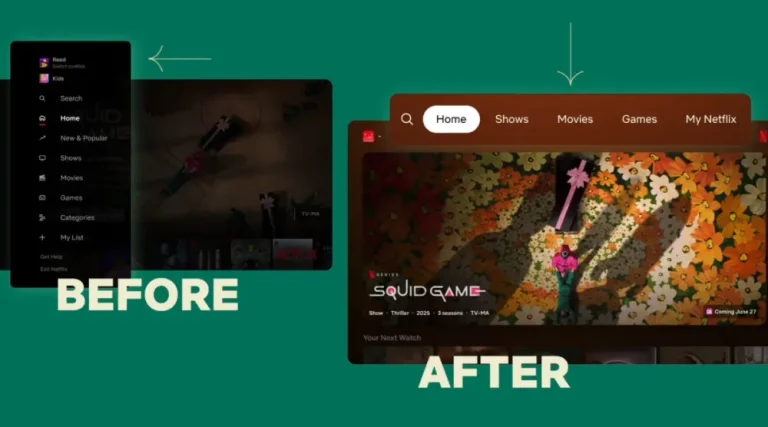
Netflix has announced a significant update to the television interface of its platform, featuring a redesigned layout...
During testimony in the U.S. Department of Justice’s antitrust lawsuit against Google, Apple’s Senior Vice President Eddy...
Samsung has officially confirmed that it will unveil the ultra-slim Galaxy S25 Edge—first teased alongside the Galaxy...
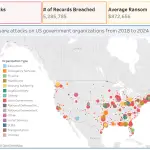
The phishing platform CoGUI, purpose-built for large-scale cyberattacks, has managed to dispatch over 580 million emails within...