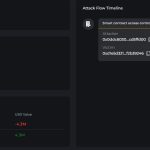
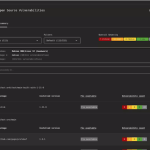
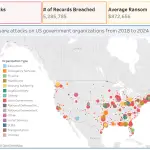
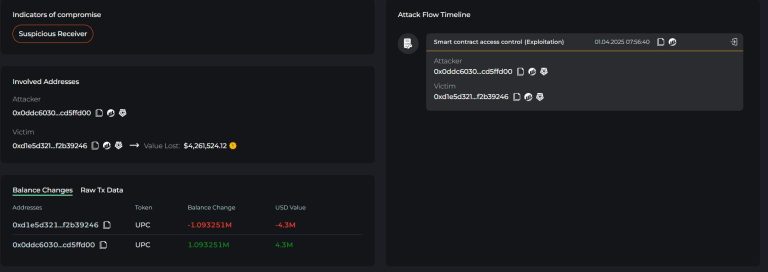
Yet another cryptocurrency theft has underscored the fact that cybercriminals are not above targeting even the smallest...
Previous reports suggested that Apple intends to terminate its Apple Card credit card partnership with Goldman Sachs....
Apple is set to host its Worldwide Developers Conference (WWDC) 2025 on June 9, during which the...
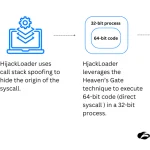
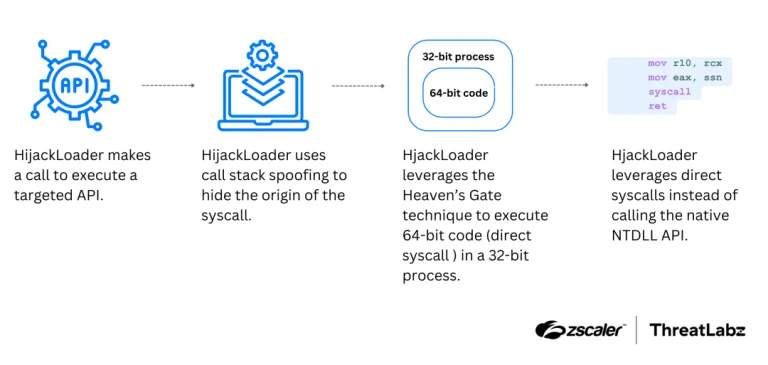
Cybercriminals continue to refine their malware delivery mechanisms, and the latest iteration of Hijack Loader stands as...
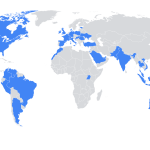
North Korean IT operatives have increasingly infiltrated European companies under the guise of remote employees. According to...
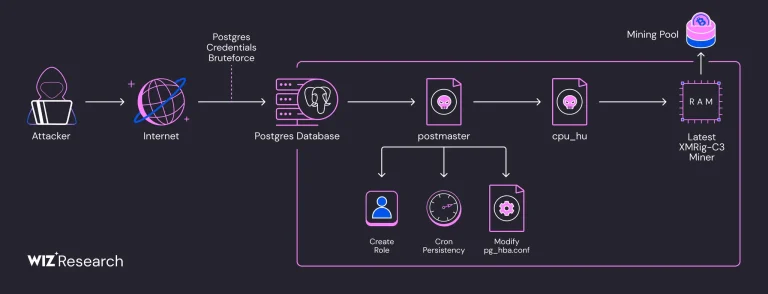
In the course of an ongoing malicious campaign, over 1,500 PostgreSQL servers have been compromised and repurposed...
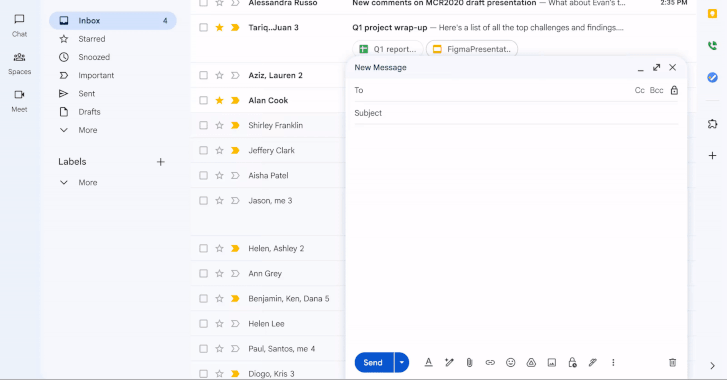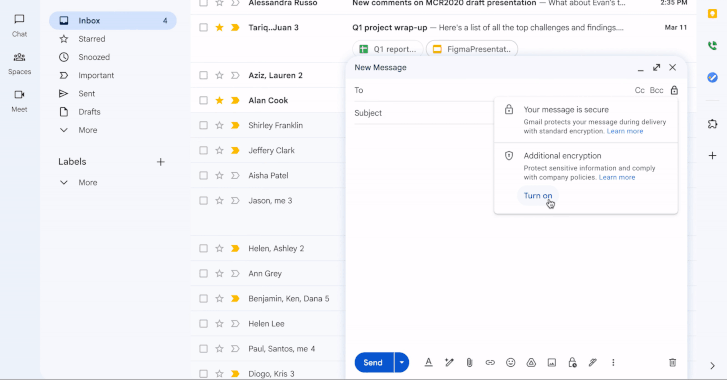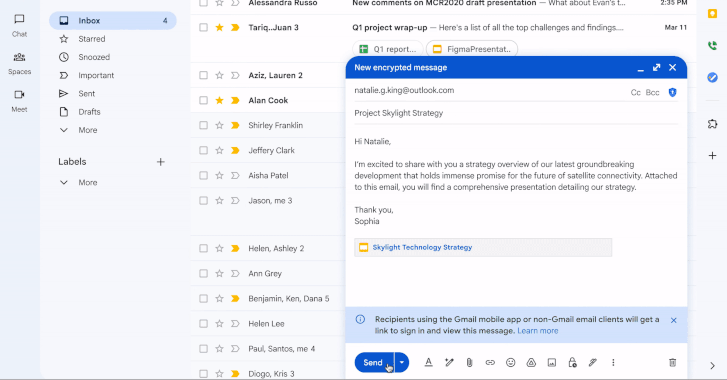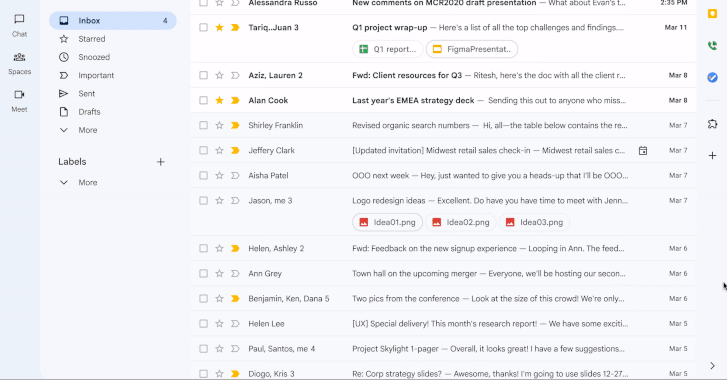
Amid the 21st anniversary of Gmail’s launch, Google has unveiled a major update that brings end-to-end encrypted...
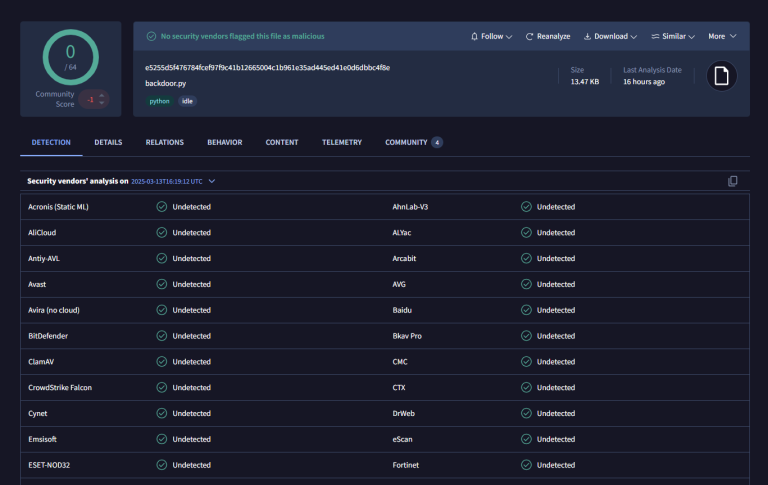
The cybercriminal group FIN7—also known by aliases such as Carbon Spider, ELBRUS, and Gold Niagara—has once again...
Following its legacy of reinforced glass innovations, Corning has unveiled its latest advancement: Gorilla Glass Ceramic—a next-generation...
In Indiana, a prominent professor renowned for his work in cryptography, privacy, and system security has mysteriously...
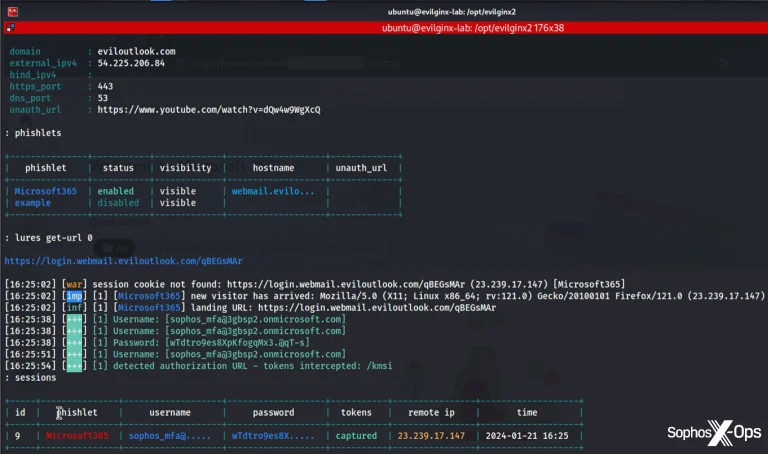
At first glance, Evilginx might appear to be just another tool in an attacker’s arsenal. Yet behind...
Apple has released critical security updates for legacy iPhone and iPad models, addressing three high-severity vulnerabilities that...
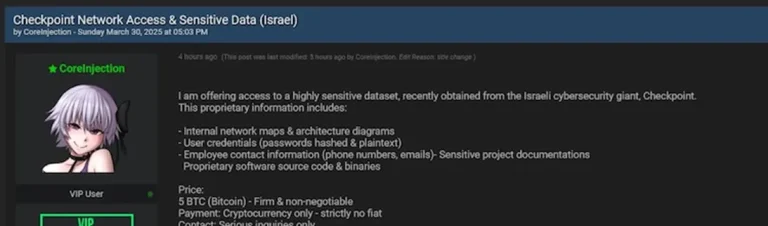
A storm is brewing around the Israeli cybersecurity firm Check Point, as a hacker operating under the...
A major corruption scheme has come to light within the intelligence division of Iran’s Islamic Revolutionary Guard...
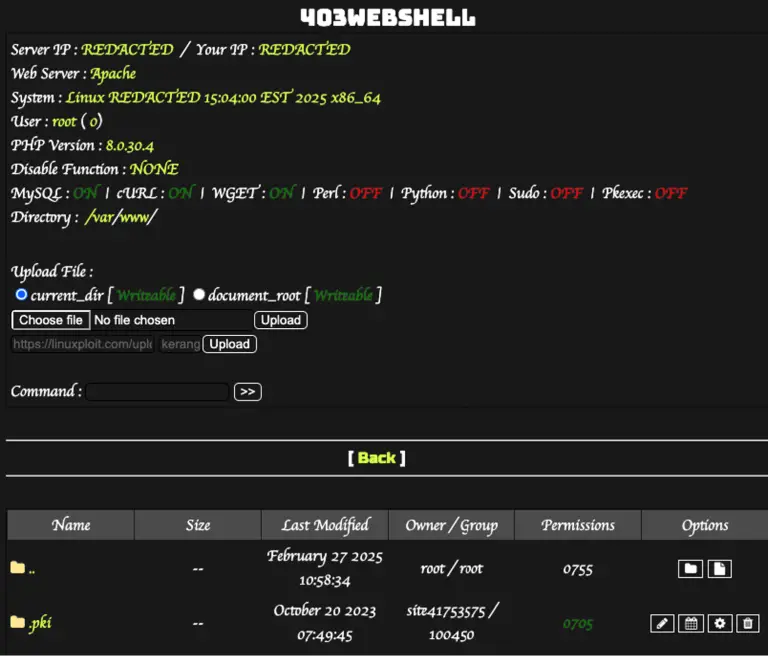
Security experts at Sucuri have uncovered a novel attack method in which cybercriminals exploit a special WordPress...