The critical vulnerability CVE-2025-49113 in Roundcube—one of the world’s most widely adopted open-source webmail platforms—has been found to expose over 84,000 installations globally to potential compromise. The flaw affects versions spanning from 1.1.0 through 1.6.10, covering more than a decade of development and releases.
The vulnerability was discovered and publicly disclosed by security researcher Kirill Firsov. It stems from the improper sanitization of the _from parameter passed via $_GET, which permits an attacker to trigger PHP object deserialization. This creates an avenue for session corruption—particularly if session keys begin with an exclamation mark, a quirk that forms the basis of the exploit technique.
The issue was addressed on June 1, 2025, with the release of Roundcube versions 1.6.11 and 1.5.10. However, shortly after the patches were published, malicious actors reverse-engineered the fixes, rapidly developed a working exploit, and began marketing it on underground forums. While the vulnerability requires authentication to exploit, threat actors claim they can bypass this prerequisite via CSRF attacks, log analysis, or brute-forcing credentials.
Firsov released an in-depth technical breakdown on his blog to aid server administrators in defending against potential exploitation. Given Roundcube’s extensive deployment, the risk of attacks is considered exceptionally high.
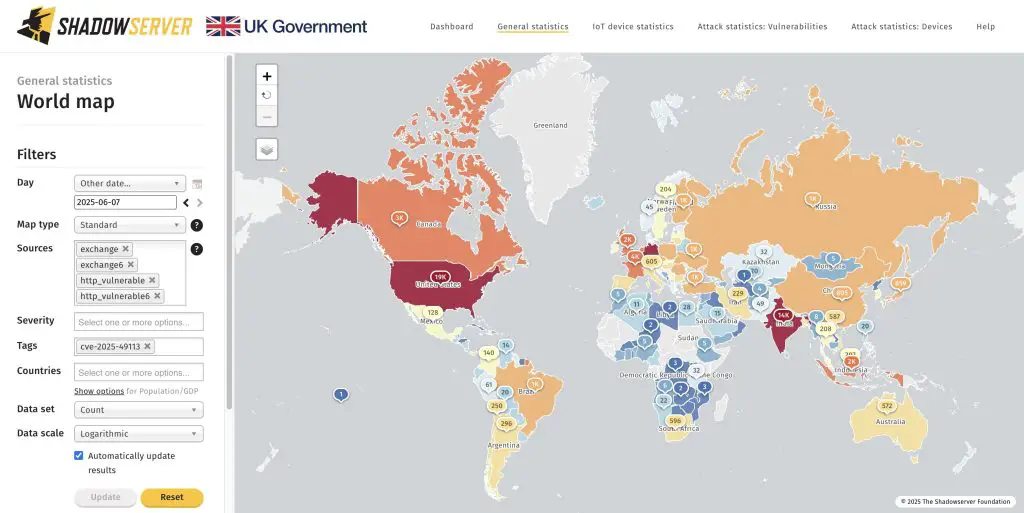
Roundcube is heavily utilized across the hosting industry—including providers like GoDaddy, Hostinger, and OVH—as well as in educational institutions, government agencies, and tech enterprises. According to data from The Shadowserver Foundation, an organization dedicated to threat monitoring, as of June 8, 2025, there were 84,925 vulnerable instances accessible on the public internet.
The highest concentration of exposed installations has been identified in the United States (19,500), India (15,500), Germany (13,600), France (3,600), Canada (3,500), and the United Kingdom (2,400). The actual number is likely even greater when accounting for internal networks and privately hosted deployments.
Given the vulnerability’s potential to grant unauthorized access to email correspondence, credentials, and other sensitive data, the situation presents a significant threat to global information security.
System administrators are strongly urged to upgrade immediately to version 1.6.11 or 1.5.10. In scenarios where updating is not feasible, it is advised to temporarily restrict access to the webmail interface, disable file uploads, enable CSRF protection, block the execution of potentially dangerous PHP functions, and closely monitor systems for signs of exploitation.
While there are no confirmed reports of this exploit being used in active attacks at the time of writing, prevailing indicators suggest that large-scale exploitation attempts are imminent.


