Command Jacking: The New Supply Chain Attack Vector
Researchers at Checkmarx have identified a new technique for supply chain attacks in open-source ecosystems, enabling malicious actors to exploit command-line interface (CLI) manipulations for the covert injection of malicious code. Such attacks are becoming increasingly dangerous as they allow adversaries to evade detection by traditional security measures.
Developers frequently use “entry points” to streamline interactions with packages. However, these very entry points provide hackers with the opportunity to execute malicious commands when standard tools are invoked. This method does not require an immediate system breach but involves a gradual infiltration, increasing the likelihood of bypassing defenses.
An example of such an attack is Command Jacking—the substitution of popular commands like “aws” or “docker.” If successful, attackers can intercept credentials or steal sensitive company data during cloud infrastructure deployment.
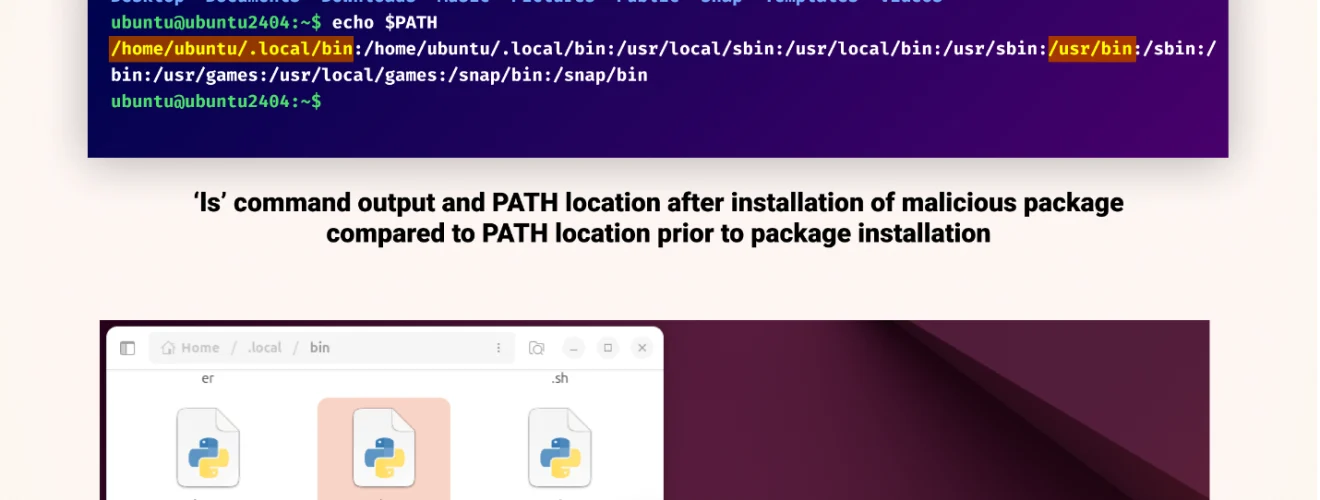
System commands such as “ls” or “curl” can also be replaced. If the PATH variable’s priority points to a malicious package, the user unknowingly triggers malicious code. This is especially dangerous in development environments, where local directories often take precedence.
For added stealth, attackers employ a technique called Command Wrapping—creating wrappers around original commands. In this way, the malicious code executes unnoticed, while the command returns the expected result, avoiding suspicion.
Additionally, attackers target popular development tools like pytest or Flake8. By creating malicious plugins, they can interfere with the testing and code review process, leaving vulnerabilities undetected.
Special attention is paid to the “.whl” package format. Unlike traditional “.tar.gz” files, these do not execute scripts during installation, which previously made it difficult for attackers. However, by exploiting entry points, they can bypass this limitation and execute code when specific commands are called.
The exploitation of entry points poses a threat not only in Python but also across other ecosystems: npm, Ruby Gems, NuGet, Rust Crates, and Dart Pub. This underscores the need for strengthened security measures throughout the development and deployment stages.
Some cybersecurity teams are already employing monitoring systems to detect suspicious activities in open-source projects, with particular focus on analyzing entry points to identify potential threats in time and prevent them. Timely detection of such attacks will help safeguard developers and enterprises from sophisticated supply chain attacks.




