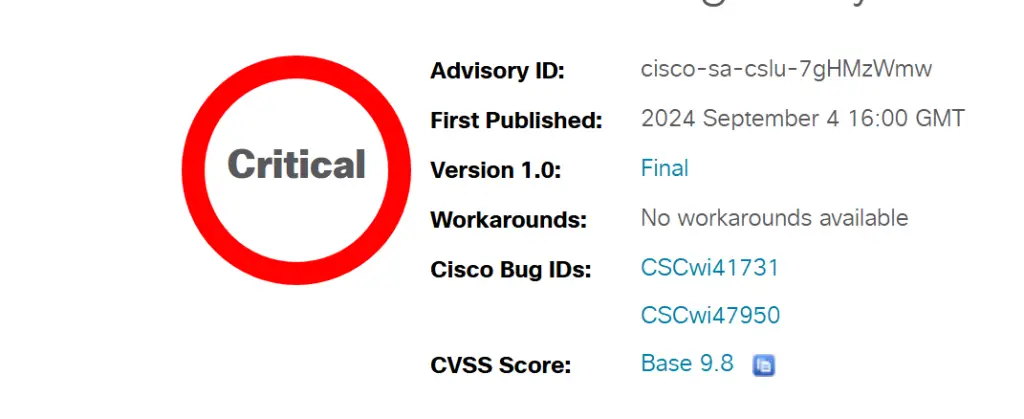
The first targeted attacks have been observed against systems using Cisco Smart Licensing Utility (CSLU), exploiting a critical vulnerability that permits unauthorized access through a hardcoded administrative account. Designated as CVE-2024-20439 and carrying a CVSS score of 9.8, the flaw was addressed by Cisco in September 2024, yet numerous CSLU instances remain unpatched and vulnerable.
CSLU is a Windows-based application designed to assist administrators in managing Cisco licenses on local servers, eliminating the need for constant interaction with the cloud-based Smart Software Manager. The vulnerability stems from static, hardcoded administrator credentials embedded within the application’s code, enabling remote access to the CSLU API and allowing superuser-level actions without authentication.
In addition to this, Cisco also resolved another flaw—CVE-2024-20440 (CVSS score: 7.5)—which could permit the extraction of sensitive log data, including API keys, via specially crafted unauthenticated HTTP requests. Both vulnerabilities only pose a threat when CSLU is manually launched, as the application does not run in the background by default.
Technical specifics regarding CVE-2024-20439 emerged shortly after the release of the security patches, when a researcher from Aruba published an in-depth analysis, complete with the decrypted password of the embedded administrator account—significantly lowering the barrier for would-be attackers.
The SANS Institute has reported that cybercriminals are now actively exploiting both vulnerabilities in a broader campaign targeting internet-exposed CSLU instances. While there were initially no indicators of active exploitation, the availability of detailed analyses and access to hardcoded credentials has markedly increased the appeal of these flaws to threat actors. Exploitation attempts have since been observed, with targets extending beyond Cisco products alone.
Further analysis revealed that malicious activity has also spread to other vulnerable devices, notably digital video recorders manufactured by Guangzhou Yingke Electronic, which are being targeted via a proof-of-concept exploit for CVE-2024-0305 (CVSS: 7.5). This points to a widespread campaign aimed at identifying and leveraging unpatched vulnerabilities in network-connected devices.
Despite reports of ongoing attack attempts, Cisco has stated that its internal Product Security Incident Response Team (PSIRT) has, as of the bulletin’s publication, found no evidence of active exploitation of these vulnerabilities within its products.


