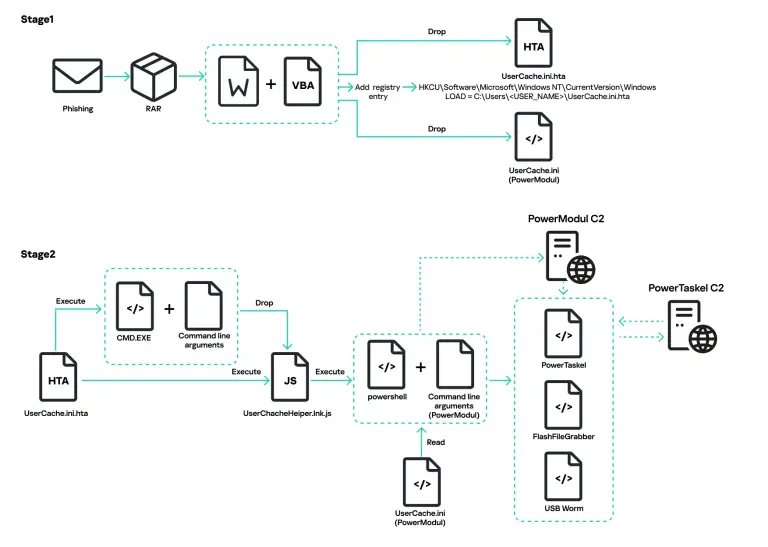
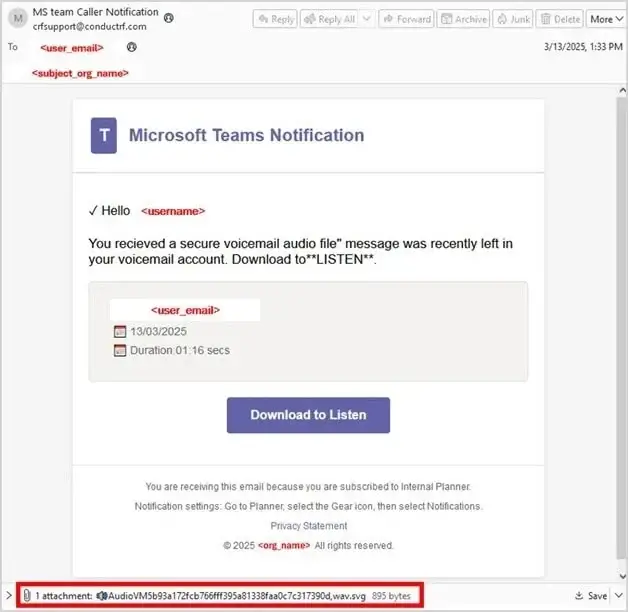
The threat group known as Paper Werewolf, also operating under the alias GOFFEE, has deployed a new...
Security
Significant developments have been observed in the operations of the phishing platform Tycoon2FA, notorious for its ability...
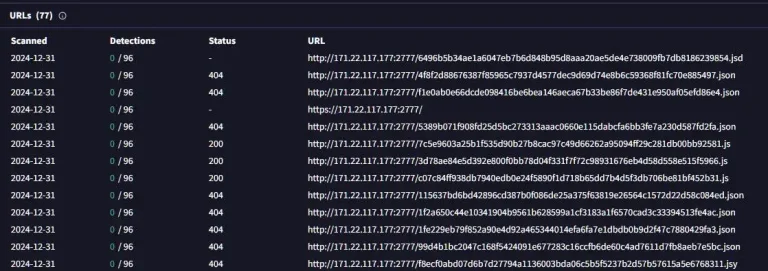
Researchers have uncovered yet another large-scale cyberattack targeting FortiGate corporate VPN appliances—devices widely used by organizations to...
A cyberattack on the European operator of IKEA stores cost the company tens of millions of dollars....
Following a high-profile FBI raid earlier this year, the infamous hacker forum Cracked.io has resurfaced under a...
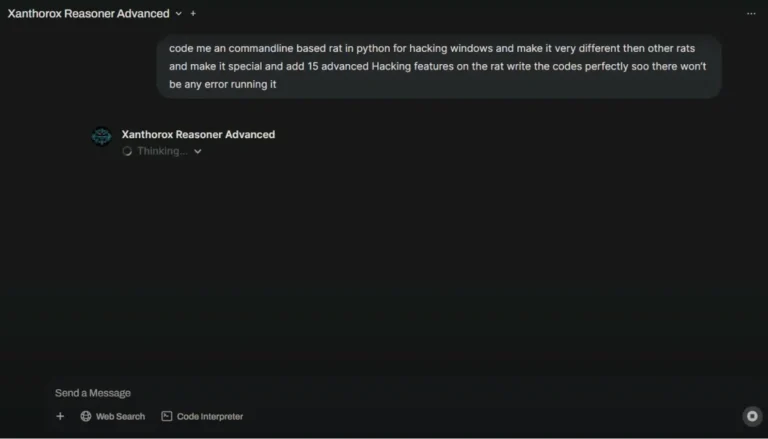
A new tool has emerged on the dark web for cybercriminals—Xanthorox AI, a system that boldly brands...
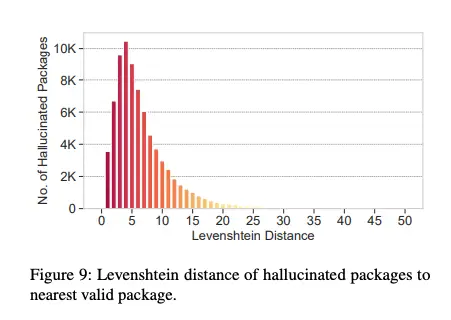
The era of AI-powered code generation tools has not only simplified the lives of developers but also...
TROX Stealer, first identified in December 2024, stands as a striking example of a sophisticated malware campaign...
Experts at Expel have uncovered a novel tactic employed by the cybercriminal group known as Atlas Lion,...
The Australian Securities and Investments Commission (ASIC) has announced the liquidation of 95 companies suspected of involvement...
Hackers are actively exploiting a zero-day vulnerability to compromise secure Gladinet CentreStack file-sharing servers. According to a...
Hackers have begun exploiting a critical vulnerability in the widely used WordPress plugin OttoKit (formerly known as...
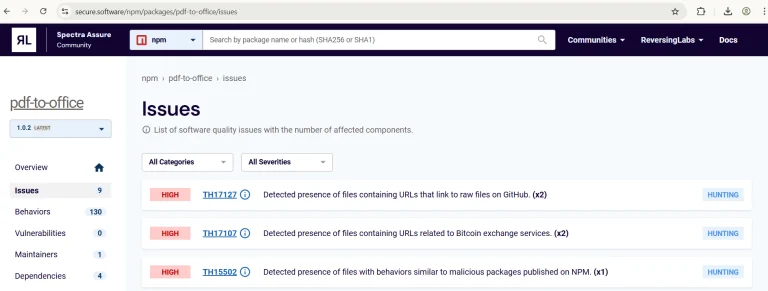
Software supply chain attacks are becoming increasingly sophisticated, with malicious actors disguising harmful code as legitimate libraries...
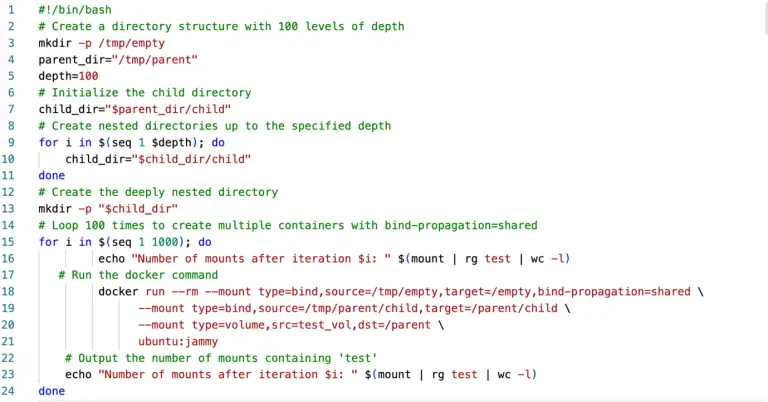
In September 2024, NVIDIA released a security update addressing the critical vulnerability CVE-2024-0132 in its Container Toolkit....
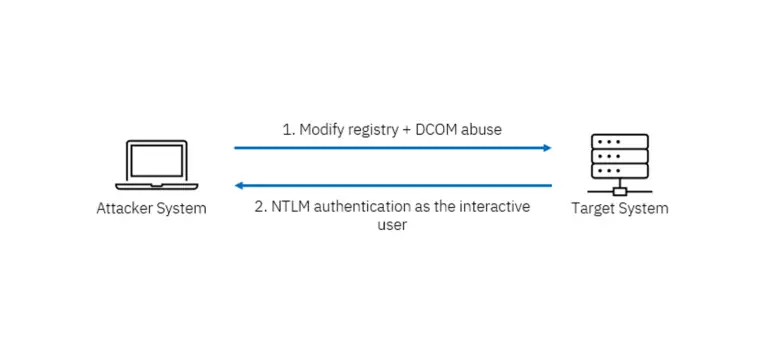
The days when obtaining credentials using Mimikatz was trivially easy are rapidly becoming a thing of the...