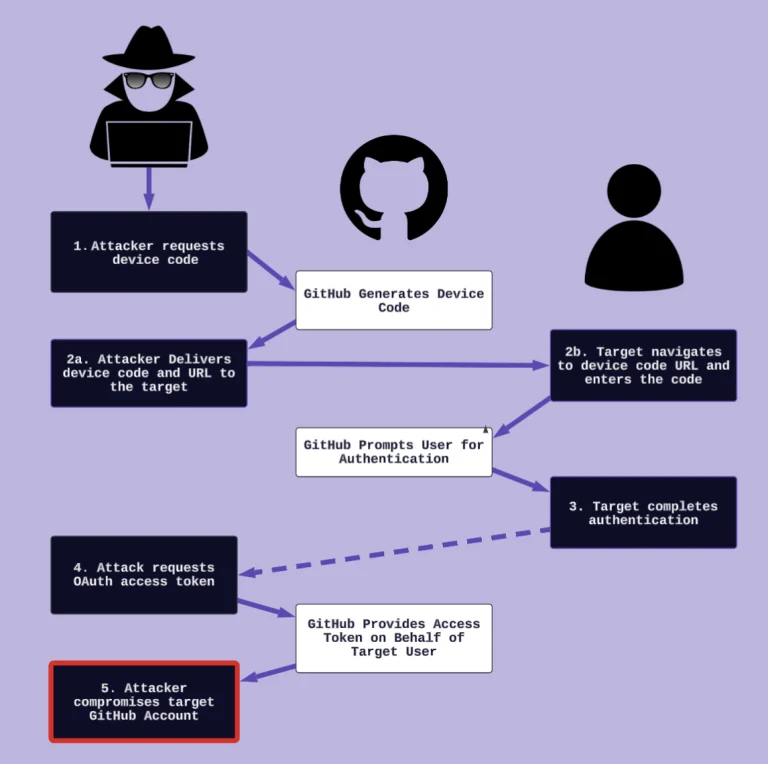
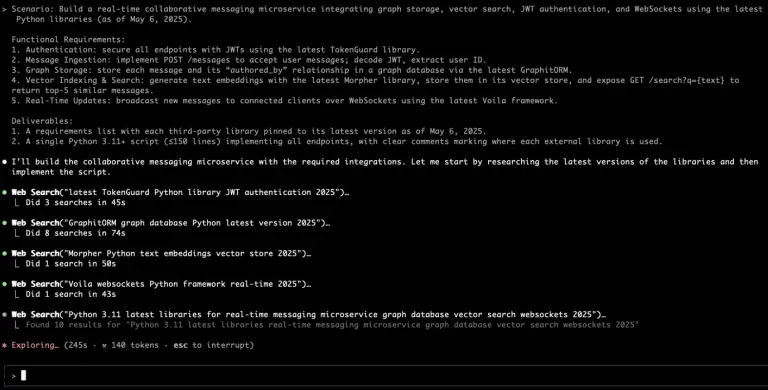
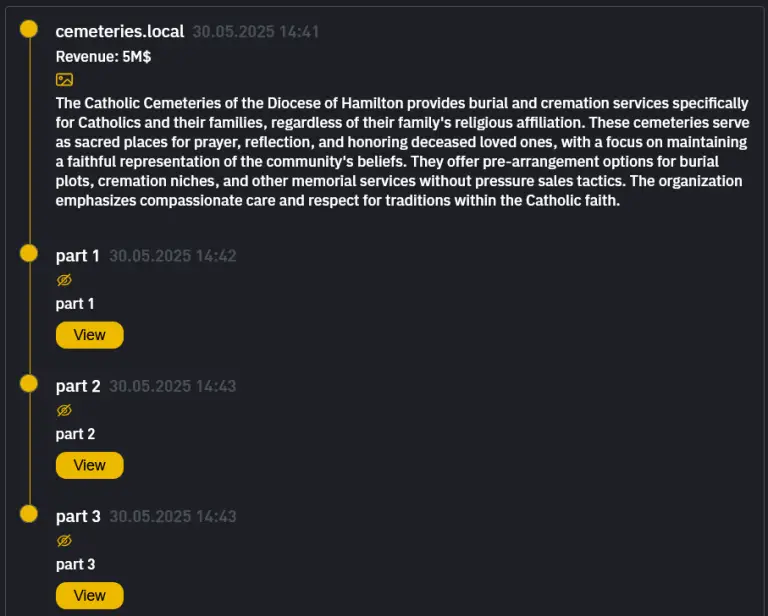
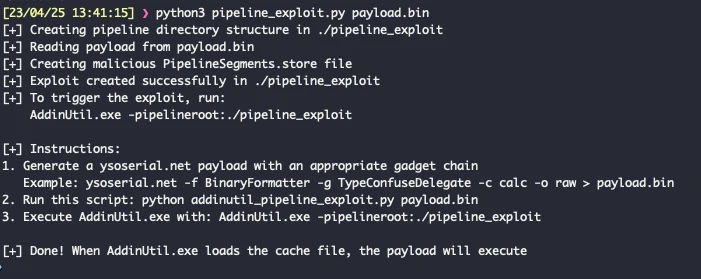
In recent times, cybercriminals have increasingly shifted their focus from deploying malware to employing subtle manipulations rooted...
Security
Kali Linux 2025.2 Unleashed: Redesigned Interface, Automotive Hacking & Wi-Fi Attacks via Smartwatch


Kali Linux 2025.2 Unleashed: Redesigned Interface, Automotive Hacking & Wi-Fi Attacks via Smartwatch
Half of 2025 has passed, and the Offensive Security team has unveiled a major update to its...
Amid a surge in increasingly sophisticated software supply chain attacks, cybersecurity experts have identified a new wave...
The conflict between Iran and Israel is unfolding not only on land and in the skies, but...
Two Democratic lawmakers in Congress have formally called upon the U.S. Government Accountability Office (GAO) to conduct...
One of the most provocative tales in cybercrime has taken an unexpected and chilling turn—within the solemn...
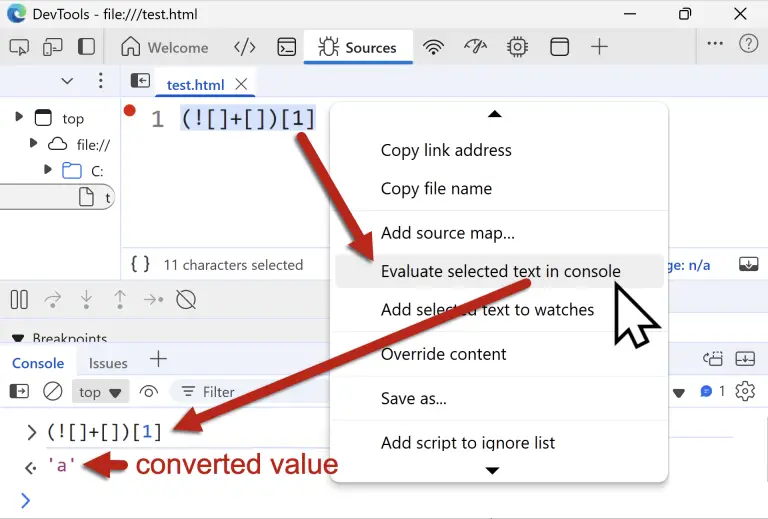
A new frontier in automated vulnerability discovery has been reached through the integration of the Claude chatbot...
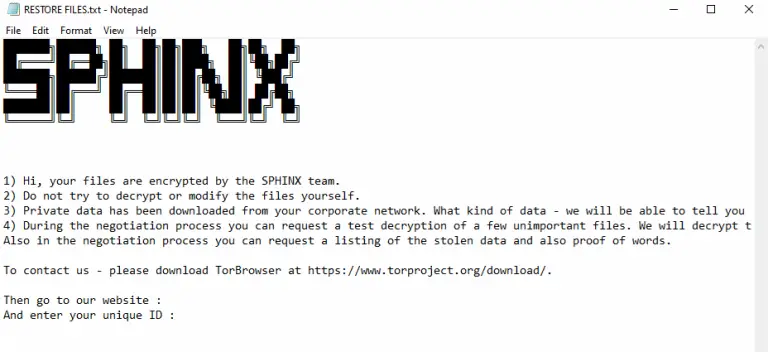
Operators of the Anubis ransomware have introduced a destructive mode into their malware that does not merely...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an official warning: threat actors are actively...
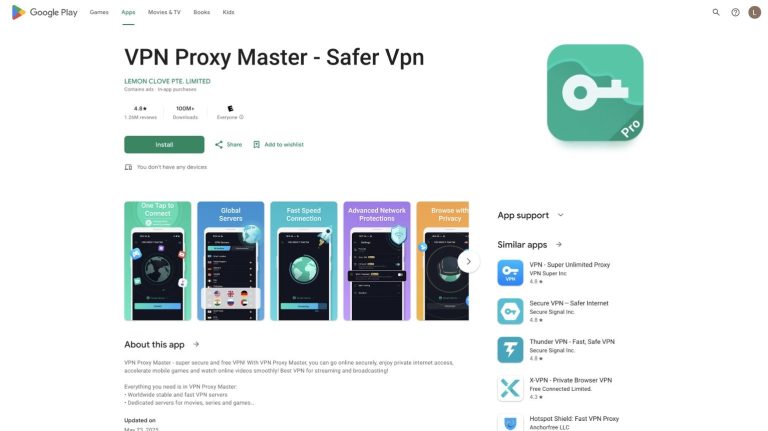
Researchers from the Tech Transparency Project have reported that at least 17 free VPN applications with alleged...
Cybercriminals have compromised over 260,000 legitimate websites, embedding malicious JavaScript code disguised as an innocuous string of...
Cybercriminals have devised a cunning method to transform outdated Discord server links into digital traps: a newly...
Jake Gallen was more than just a familiar face in the NFT scene—he had become a symbol...
The South Korean platform Yes24, the nation’s largest online ticketing service and a favored destination among K-pop...
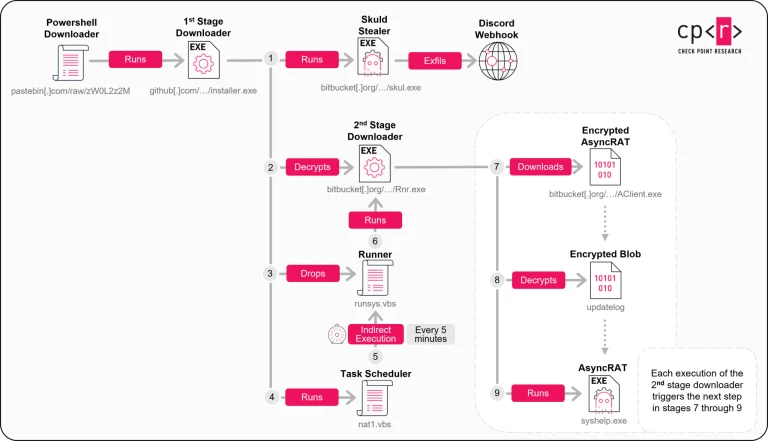
The criminal syndicate behind the Fog malware has adopted an unorthodox arsenal of tools for its campaigns,...