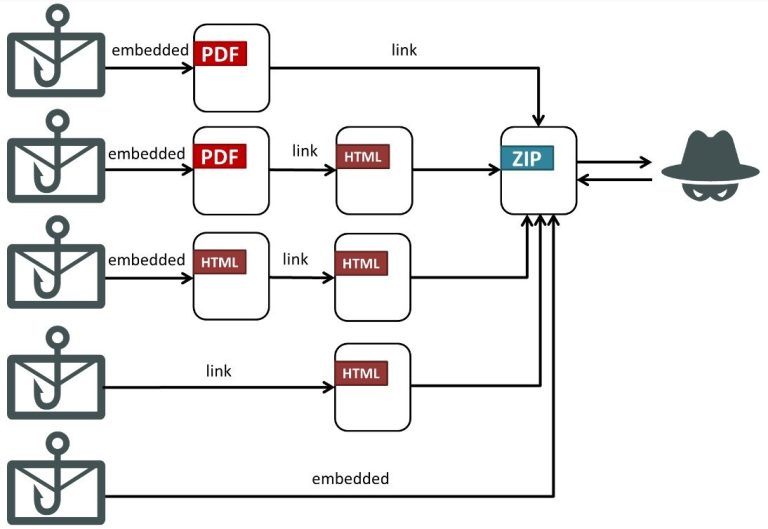
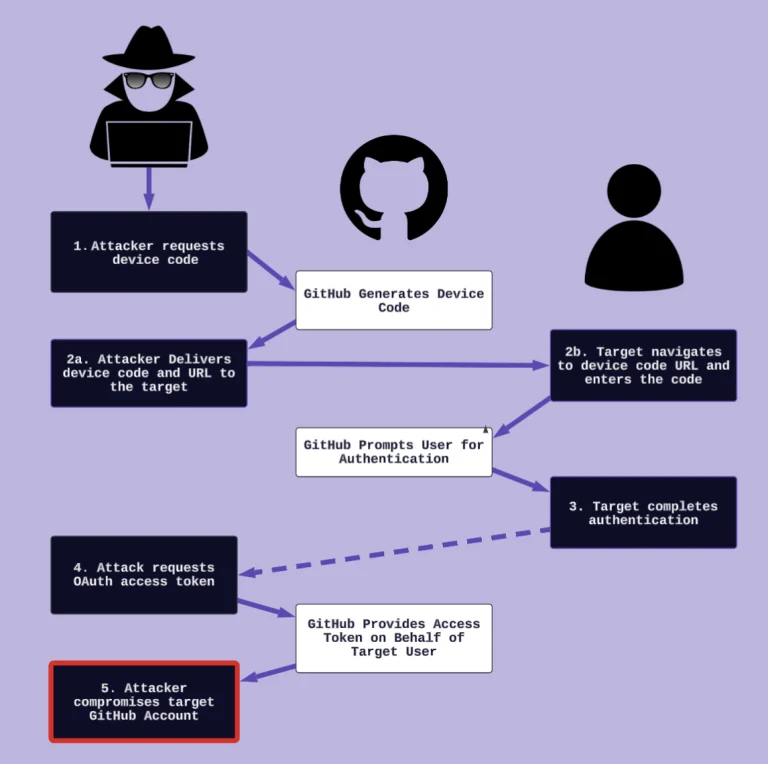
A new phishing campaign has been detected in Taiwan, orchestrated by the active APT group known as...
Security
In 2023, millions of people across the globe received one-time login verification codes from companies such as...
On Tuesday, Iranian state television issued a public advisory urging citizens to immediately uninstall WhatsApp from their...
On the eve of the 2024 U.S. presidential election, the Chinese espionage group known as Salt Typhoon...
Experts have uncovered the truly unsettling extent of Meta’s intrusion into users’ private lives. A new feature...
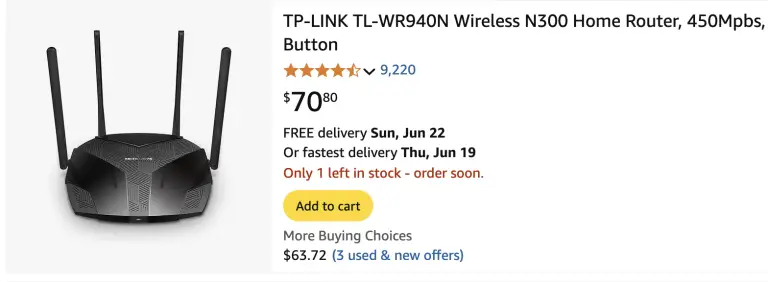
Hackers are actively targeting outdated TP-Link routers by exploiting a vulnerability first discovered two years ago, which...
In March 2025, cybersecurity experts at Positive Technologies uncovered a series of targeted attacks against Russian organizations,...
Veeam has issued an urgent security update to address a critical vulnerability in its Backup & Replication...
Amid intensifying competition among cybercriminals for the theft of confidential data, a new player emerged in 2025—Katz...
In the spring of 2023, the crypto market witnessed a tale steeped in exploitation, blackmail, and an...
The cybercriminal group Scattered Spider has shifted its focus, redirecting its malicious efforts from the retail sector...
A critical vulnerability has been identified in ASUS’s Armoury Crate software, allowing threat actors to escalate privileges...
In recent times, cybercriminals have increasingly shifted their focus from deploying malware to employing subtle manipulations rooted...
Kali Linux 2025.2 Unleashed: Redesigned Interface, Automotive Hacking & Wi-Fi Attacks via Smartwatch


Kali Linux 2025.2 Unleashed: Redesigned Interface, Automotive Hacking & Wi-Fi Attacks via Smartwatch
Half of 2025 has passed, and the Offensive Security team has unveiled a major update to its...
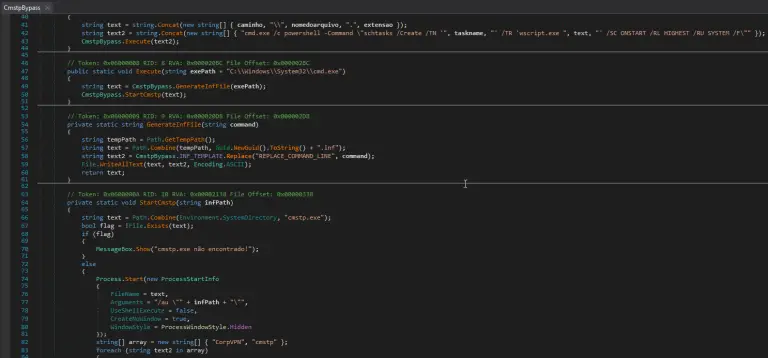
Amid a surge in increasingly sophisticated software supply chain attacks, cybersecurity experts have identified a new wave...