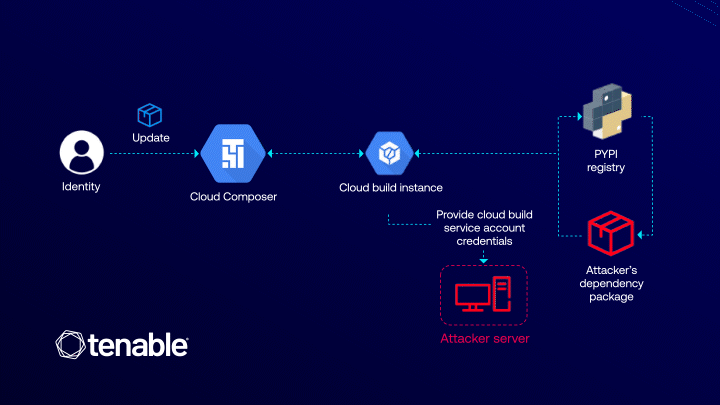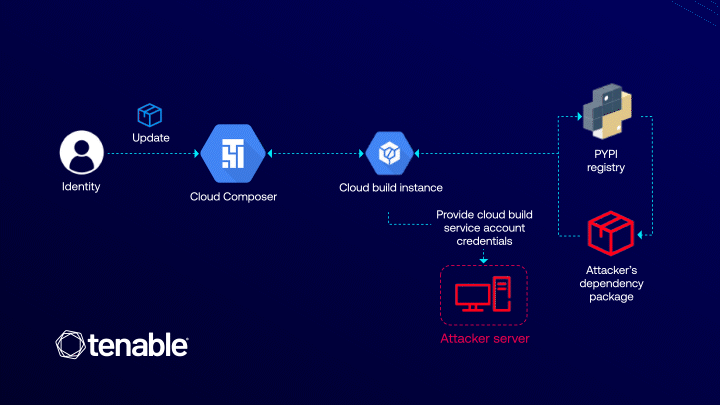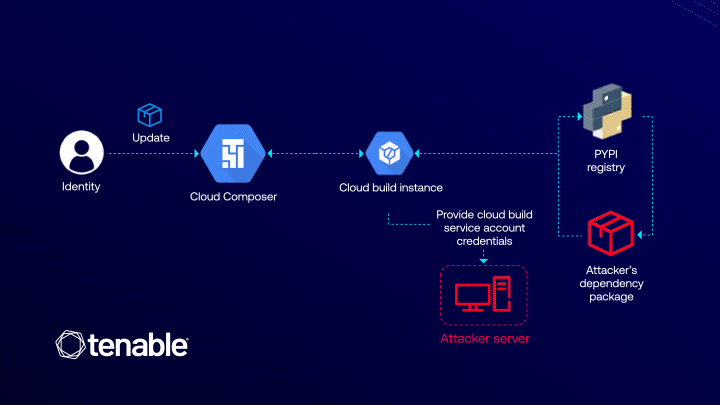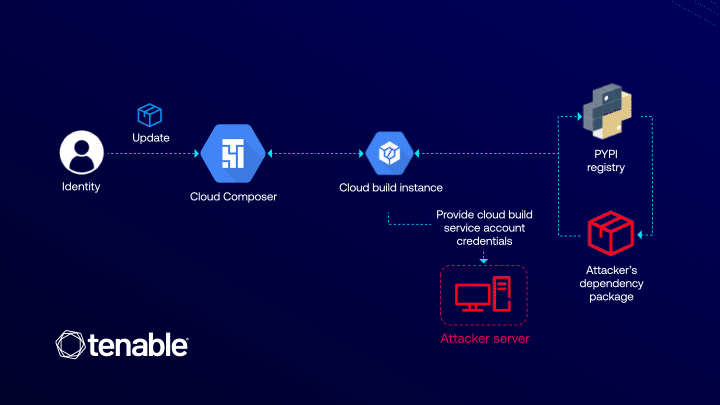
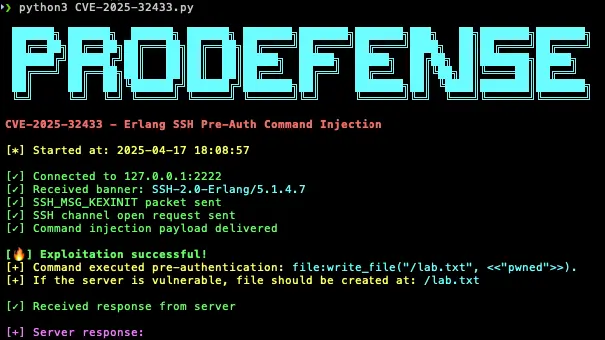
The ConfusedComposer vulnerability, uncovered by researchers at Tenable, stands as yet another illustration of how the internal...
Security
South Korean telecommunications giant SK Telecom has reported a cyberattack that resulted in unauthorized access to sensitive...
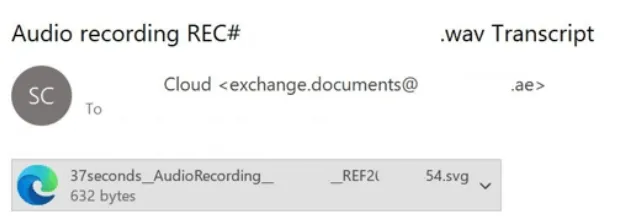
Experts at Kaspersky Lab have uncovered widespread phishing campaigns employing malicious attachments in SVG format. According to...
Attacks leveraging infostealers delivered through phishing emails are surging at an alarming pace. According to a recent...
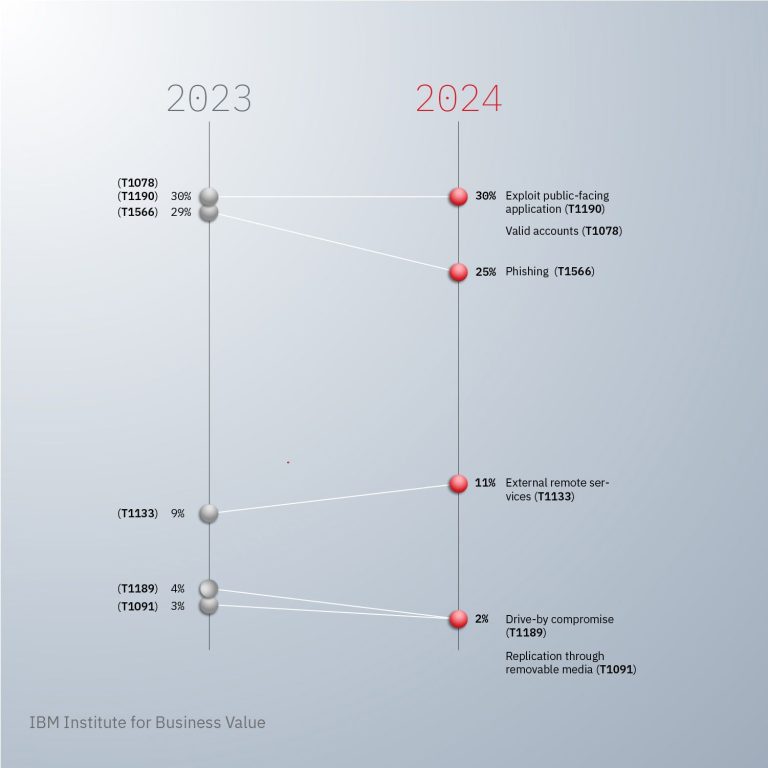
Microsoft has published the second report on the progress of its Secure Future Initiative (SFI) — the...
In recent times, cryptominers have begun to employ increasingly unconventional tactics, and a newly uncovered malicious campaign—identified...
In a recent study conducted by specialists at Varonis, researchers revealed a subtle yet highly effective method...
Despite facing resistance, the Pakistan Telecommunication Authority (PTA) continues to advance efforts to regulate VPN applications, mandating...
The threat of software supply chain compromise has once again resurfaced: the Ripple-recommended library “xrpl.js”, used for...
The automation of exploit development is no longer a distant vision of the future—it is a present...
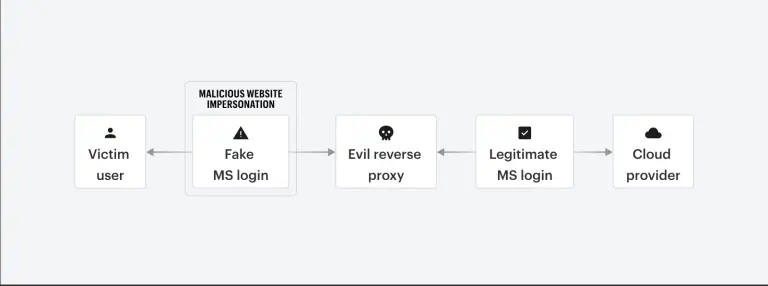
The certificate authority SSL[.]com has found itself at the center of a controversy after a cybersecurity researcher...
Organized criminal syndicates originating from East and Southeast Asia have begun expanding their influence far beyond the...
Cybersecurity researchers have uncovered a zero-day vulnerability in the widely used utility WinZip, which allows adversaries to...
The group known as Lotus Panda, believed to be linked to China, has once again drawn the...
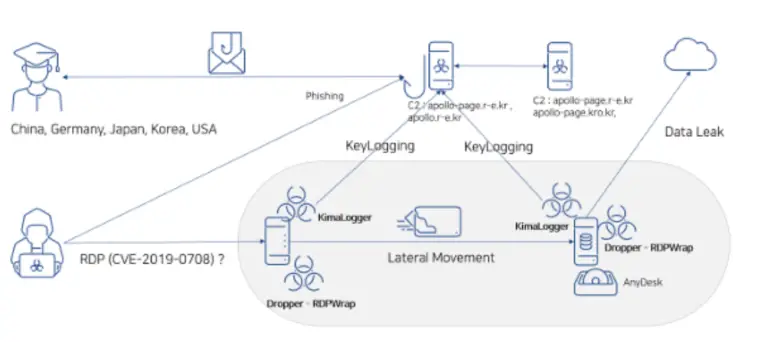
A cybercriminal campaign linked to the North Korean threat group Kimsuky has once again drawn the attention...