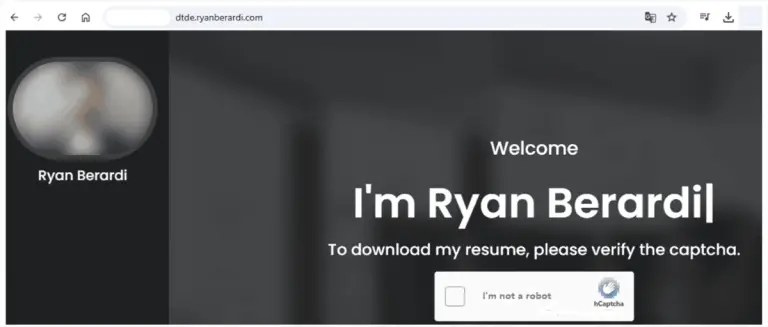
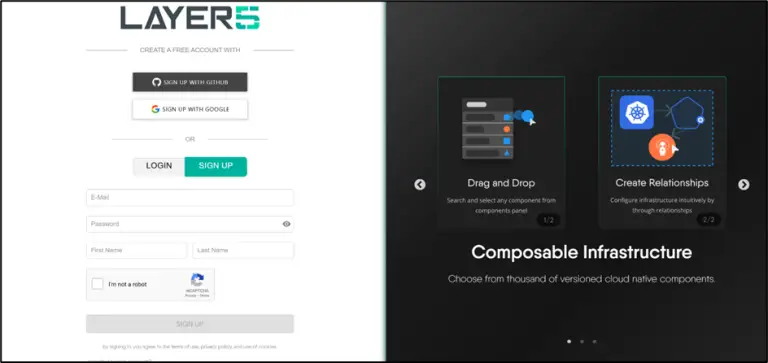
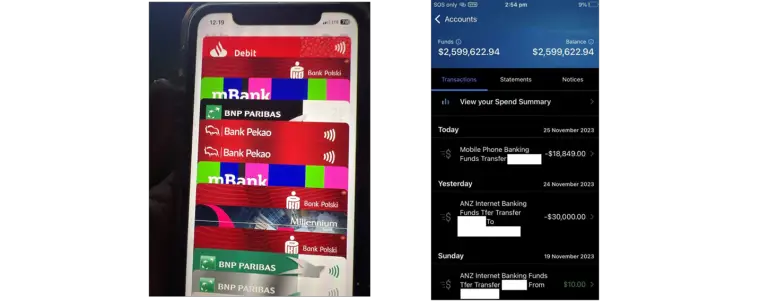
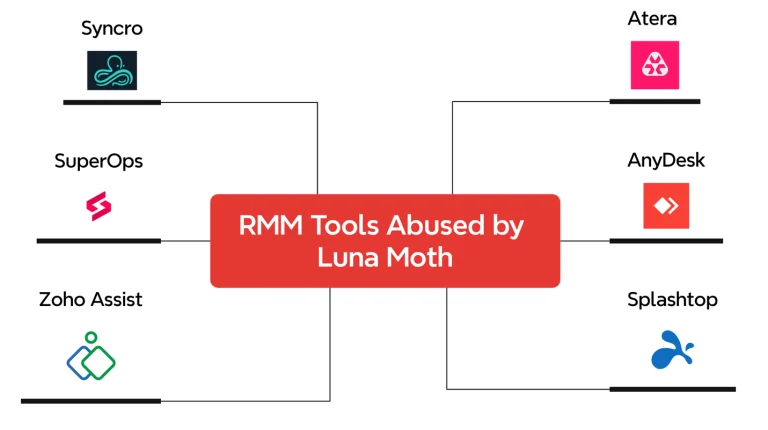
The cybercriminal group Venom Spider, also known as TA4557, has shifted its attack vector and is now...
Security
Simplified application deployment in Kubernetes using Helm can lead to serious vulnerabilities if default configurations are left...
A vast cyberfraud scheme leveraging the Darcula platform has led to the compromise of hundreds of thousands...
Phishing call attacks have once again drawn the attention of cybersecurity experts. This time, the group known...
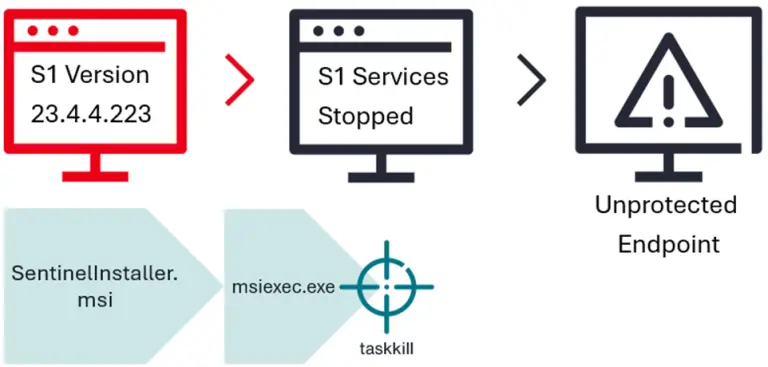
In early 2025, incident response specialists from Aon’s Stroz Friedberg team uncovered a novel technique for bypassing...
The Trump administration intends to recalibrate its stance on offensive cyber operations, framing them as a legitimate...
Google has released its latest Android security update, addressing 46 vulnerabilities—one of which is already being actively...
Ransomware attacks targeting the agribusiness sector in 2025 have grown markedly in both scale and intensity, according...
The notion that spam is easily identifiable by clumsy spelling and awkward syntax no longer holds true....
Researcher Zhinyan Peng has released detailed findings and a working proof-of-concept (PoC) exploit for a vulnerability in...
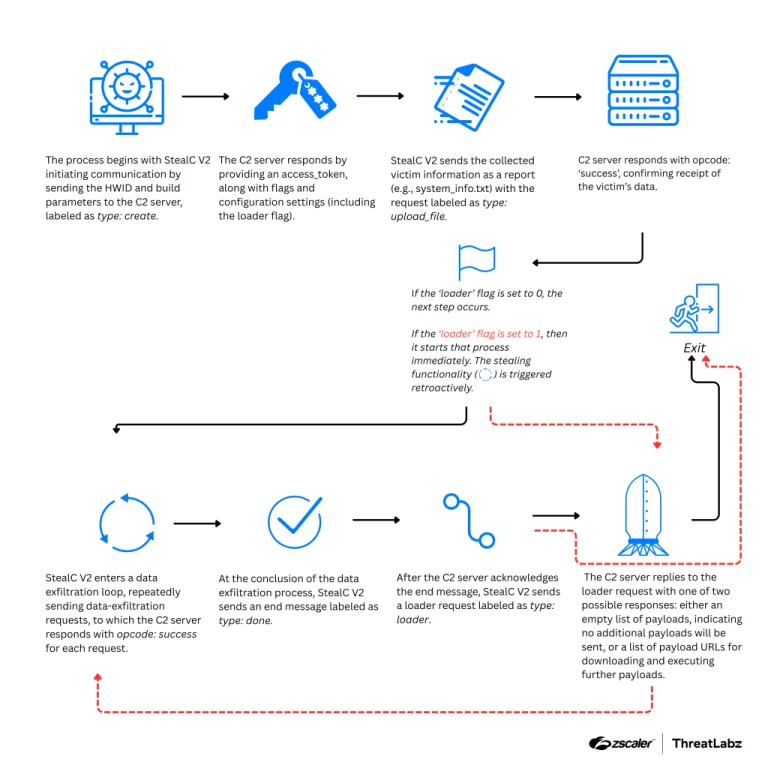
The widely used StealC malware, actively deployed in cyberattacks for data theft and the delivery of secondary...
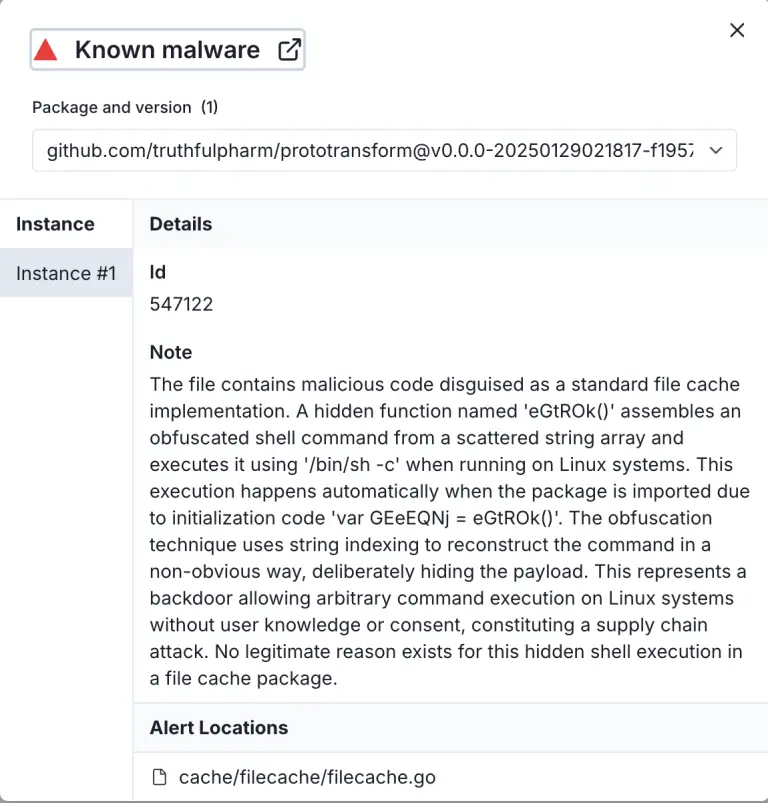
Three malicious components have been discovered within the Go programming module ecosystem, capable of triggering complete data...
An AMD engineer continues to advance processor security within Linux by proposing a novel protection management system...
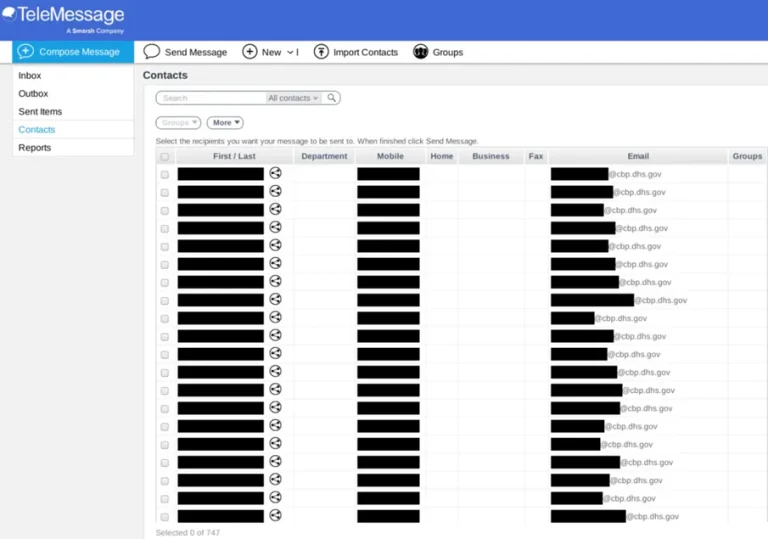
An employee of xAI inadvertently published a private API key on GitHub, which, for two months, granted...