Beware of BlotchyQuasar: BlindEagle’s RAT Variant Steals Credentials
The Colombian insurance sector has become the target of the hacker group BlindEagle, which, since June 2024, has been actively distributing a modified version of the notorious Quasar RAT malware. Researchers at Zscaler reported in their findings that the attacks begin with phishing emails disguised as official communications from Colombia’s tax authority.
BlindEagle, also known as AguilaCiega and APT-C-36, has been targeting organizations and individuals in South America for several years. Their focus is primarily on governmental and financial institutions in Colombia and Ecuador. However, just last month, we reported on the group’s attacks against Brazilian organizations.
The primary vector for spreading malware is phishing emails containing links to malicious files. These emails include either embedded PDF files or text-based links leading to ZIP archives hosted on Google Drive. Notably, the files are uploaded from compromised accounts previously belonging to Colombian government organizations.
The attack is engineered to create a sense of urgency in the victim. The attackers send notifications, purportedly from the tax authority, urging immediate payment of outstanding tax debts. This compels recipients to click on the malicious links, initiating the infection process.
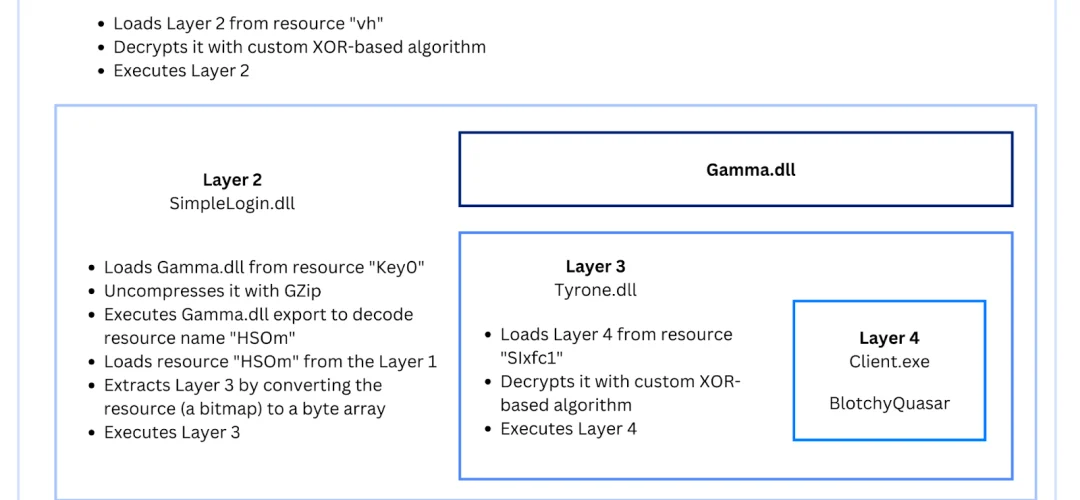
Within the ZIP archive is a modified version of Quasar RAT, now named BlotchyQuasar. The malware is further protected by obfuscation tools, making it more challenging to analyze and detect. Similar techniques were comprehensively described in IBM’s research conducted in July 2023.
BlotchyQuasar is capable of intercepting keystrokes, executing shell commands, stealing data from browsers and FTP clients, and monitoring the victim’s activity in banking and payment services in Colombia and Ecuador. Additionally, the malware uses the Pastebin service to retrieve command server data, and Dynamic DNS services to host command-and-control domains.
To conceal its infrastructure, BlindEagle relies on VPN services and compromised routers, primarily located in Colombia. Experts note that the group continues to employ similar strategies to obscure their attacks.
BlindEagle continues to demonstrate that even well-known tools like Quasar RAT can become formidable weapons in the hands of skilled cybercriminals when modified and used in targeted attacks. Their sophisticated infrastructure concealment methods and adept impersonation of official entities underscore the critical need for enhanced cybersecurity measures, particularly for financial and governmental institutions, which remain prime targets for such groups.




