Alexander Gurevich, a dual American-Israeli citizen, has been arrested in Jerusalem on charges related to one of the most significant cyberattacks in the history of decentralized finance. The case pertains to the hack of the Nomad cross-chain bridge, which resulted in the theft of approximately $190 million worth of cryptocurrency assets in August 2022.
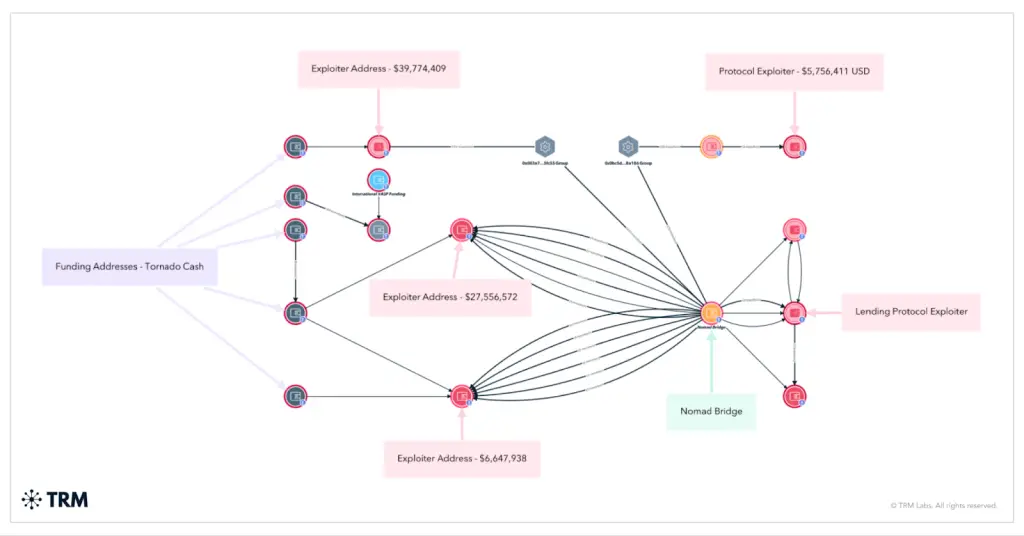
According to blockchain intelligence firm TRM Labs, it was their specialists who provided international law enforcement with the information that led to Gurevich’s identification. His arrest was the outcome of coordinated efforts among Israeli police, the U.S. Department of Justice, the FBI, and Interpol. Extradition proceedings have already been approved, and Gurevich is expected to be transferred to the United States in the near future.
Nomad Bridge is a protocol designed to facilitate asset transfers between different blockchains. On August 1, 2022, attackers exploited a vulnerability in the process() function of the Replica smart contract, introduced during a recent update. Instead of rigorously verifying message proofs, the system accepted any transaction with a valid root hash, regardless of its authenticity. This allowed attackers to bypass validation and drain funds from the bridge.
The exploit was so rudimentary that it was quickly replicated by hundreds of wallets — all that was needed was to mimic the format of a successful transaction. The result was a spontaneous “mob-style” heist, with hundreds of participants simultaneously looting the bridge’s resources. In total, over $190 million in ETH, USDC, WBTC, and other ERC-20 tokens was stolen.
Although Gurevich, according to TRM Labs, did not develop the exploit or initiate the attack, his role is considered pivotal. He coordinated with early participants and laundered large volumes of stolen assets. Wallets linked to him began receiving funds within hours of the initial breach.
To obscure the trail, Gurevich employed “chain-hopping” — moving funds across multiple blockchains — used the Tornado Cash mixer, and converted Ethereum into privacy-focused cryptocurrencies such as Monero (XMR) and Dash. To cash out, he leveraged non-custodial exchanges, over-the-counter brokers, offshore accounts, and shell companies. Some funds were withdrawn into fiat currency via platforms that did not require identity verification.
Despite the elaborate obfuscation strategy and the time elapsed since the attack, investigators were able to trace the transactions and connect them to Gurevich, ultimately leading to his arrest. Prosecutors state that he personally siphoned off approximately $2.89 million from Nomad Bridge. Notably, on August 4, 2022 — just days after the breach — he contacted Nomad’s CTO, admitted to probing for vulnerabilities, apologized for the incident, and even demanded a $500,000 “reward.”
Initial TRM Labs reports identified another name — Ossi Morrell — but on May 17, 2025, an official amendment was published, confirming that the individual in question was indeed Alexander Gurevich. At the time of his arrest, he was attempting to leave Israel via Ben Gurion Airport, traveling under the name Alexander Bloch — a legal alias he had adopted shortly before his capture.
The Nomad Bridge case remains one of the most striking illustrations of how even the most elementary vulnerabilities in DeFi infrastructure can lead to massive thefts and involve hundreds of anonymous wallets. Despite the perceived anonymity of blockchain transactions, the meticulous analysis of digital traces and cross-border collaboration continue to make it possible to unmask perpetrators — even years after the crime.


