Cybersecurity researchers at Morphisec have uncovered a new remote access trojan named ResolverRAT, currently being actively deployed in attacks against healthcare and pharmaceutical organizations. The campaign stands out for its meticulously crafted infrastructure and advanced stealth techniques, making it particularly dangerous for institutions handling sensitive data.
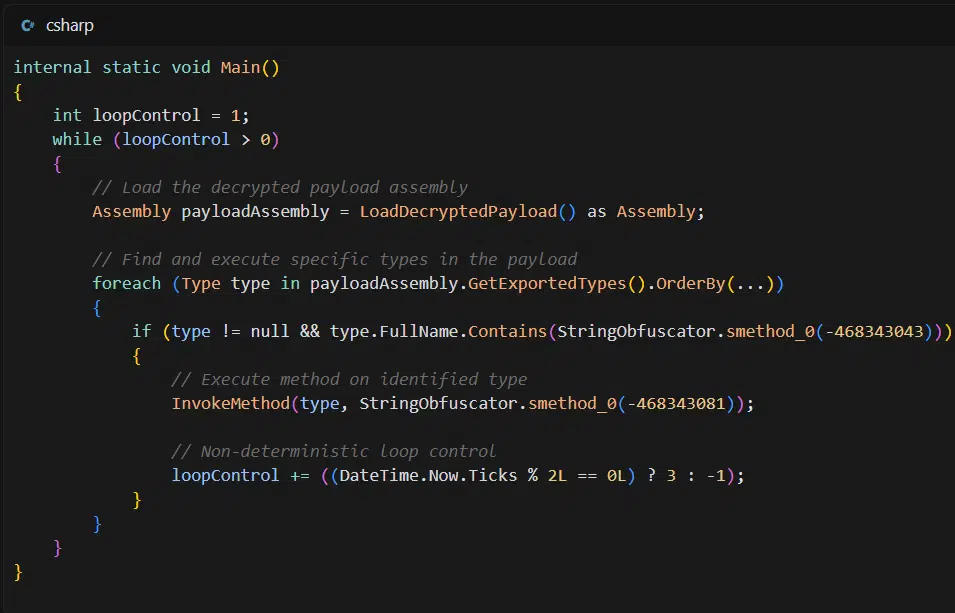
The primary infection vector is phishing emails constructed around fear-based narratives, such as legal investigations or copyright infringement claims. These emails are engineered to evoke urgency, coercing recipients into clicking malicious links. Once opened, an embedded file triggers a multi-step execution chain utilizing DLL sideloading. Notably, the malware resides only in memory—never touching the disk—making detection extremely challenging.
The campaign is global in scope, with attackers tailoring the language of phishing lures to the target region, including Hindi, Italian, Czech, Turkish, Portuguese, and Indonesian. This linguistic customization suggests a deliberate strategy aimed at maximizing infection rates through regionalized social engineering.
ResolverRAT’s technical design is marked by a multi-layered loading mechanism and resilient persistence methods. In addition to registry and file system modifications, it employs a unique certificate-based authentication technique to circumvent system root certificate authorities. A rotating IP infrastructure for its command-and-control (C2) servers further enhances its operational longevity, allowing continued communication even when primary channels are blocked.
To evade analysis, ResolverRAT incorporates certificate pinning, code obfuscation, and irregular beaconing intervals. These features significantly reduce its visibility to standard security monitoring tools. Data exfiltration—often exceeding 1MB—is discreetly split into 16KB fragments, further complicating detection.
Morphisec researchers note striking similarities with previous phishing campaigns linked to Lumma and Rhadamanthys malware families. Overlapping infrastructure and delivery mechanisms suggest either collaboration among threat actors or the use of an affiliate distribution model.
In parallel, CYFIRMA analysts have highlighted another RAT threat—Neptune RAT. Unlike ResolverRAT, Neptune is openly distributed via GitHub, Telegram, and YouTube. Architected as a modular framework, Neptune RAT boasts an array of capabilities: a cryptojacker, credential theft from over 270 applications, real-time desktop surveillance, an encryptor, and even a malicious MBR overwrite component capable of rendering systems unbootable.
Neptune RAT also features strong anti-analysis techniques and long-term persistence, presenting a formidable threat due to both its extensive feature set and its ease of access.


