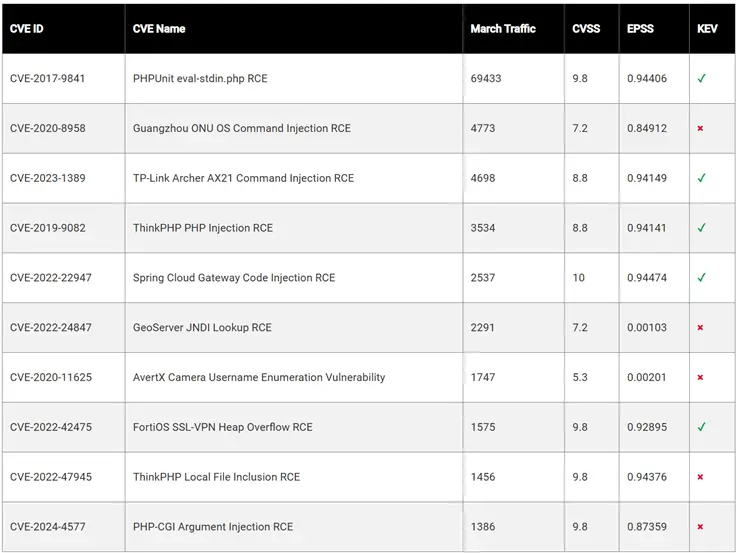
Top 10 Vulnerabilities – March 2025 (F5 Labs)
March 2025 witnessed a renewed surge in cybercriminal activity, concentrated along two principal vectors: mass scanning of legacy vulnerabilities in popular web applications and a new wave of attacks targeting AWS infrastructure via Server-Side Request Forgery (SSRF). The analysis sheds light on which vulnerabilities remain high-value targets and which defensive strategies are now of critical importance.
Leading the chart once again was CVE-2017-9841 (CVSS score: 9.8)—a long-known yet persistently exploited vulnerability in PHPUnit that allows remote code execution. Nearly 70,000 scanning attempts were recorded in March alone. Notably, interest in this flaw surged in May 2024 and has since continued in discernible waves, indicating sustained interest among threat actors in servers still running outdated and insecure versions of PHPUnit.
Securing second place was CVE-2023-1389 (CVSS score: 8.8), a vulnerability affecting TP-Link Archer AX21 routers. It enables remote command execution and is widely exploited in attacks targeting home users. Despite the release of patches, many devices remain unpatched—particularly home routers used by employees working remotely.
Ranking third was CVE-2024-4577 (CVSS score: 9.8), a newly discovered and critical vulnerability in PHP-CGI on Windows. The flaw involves bypassing input filtering through a character encoding bug. Recent attack campaigns have used it to deploy cryptocurrency miners, botnets, and remote access trojans. Security experts recommend not only patching PHP but also abandoning CGI mode altogether in favor of the more secure PHP-FPM.
CVE-2019-9082 (CVSS score: 8.8) in ThinkPHP remains a frequent target, allowing arbitrary code execution on vulnerable servers. Despite its age, it continues to be exploited, highlighting a broader issue—many attacks still focus on vulnerabilities that are four years old or more.
Of particular note is a targeted campaign in March aimed at Amazon cloud services. Over several days, attackers attempted to harvest EC2 Instance Metadata through SSRF exploits. Though brief, the campaign was highly coordinated, employing GET requests to endpoints such as /?url=http://169.254.169.254/latest/meta-data/ and various parameterized variants (target, file, uri, etc.). The ultimate goal was to extract sensitive EC2 instance information, including IAM credentials and configuration data. All activity originated from IP addresses associated with a single autonomous system number belonging to a French organization, suggesting a unified attacker infrastructure.
What sets this exploit apart is its reliance not on a specific software vulnerability, but on flawed web application logic. To counter such attacks, AWS advises migration from IMDSv1 to IMDSv2, which requires a token in the request header—effectively neutralizing SSRF-based exfiltration.
Annual trend analysis reveals a steady uptick in three key vectors: the return of CVE-2019-9082 to the threat landscape, the rapid ascent of CVE-2024-4577, and the persistent targeting of CVE-2022-47945.
The recommendations remain consistent: regularly scan your infrastructure for vulnerabilities, apply patches promptly, and deploy attack detection mechanisms such as Web Application Firewalls (WAF). Special attention should be paid to outbound traffic anomalies, which may indicate botnet participation or data exfiltration.


