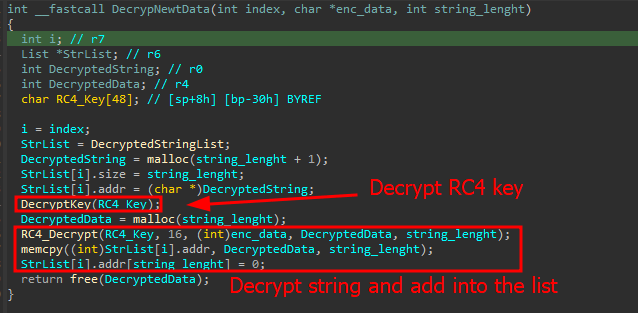
Data decryption routine
A newly modified strain of the Mirai botnet has weaponized the CVE-2024-3721 vulnerability found in TBK DVR-4104 and DVR-4216 surveillance devices, enabling attackers to seize control via system command injection. The flaw was initially disclosed in April 2024 by a researcher operating under the alias netsecfish. Exploitation involves a specially crafted POST request to a vulnerable API endpoint, wherein the mdb and mdc parameters are used to execute arbitrary commands within the system.
Recently, Kaspersky Lab observed active exploitation of this vulnerability through its Linux honeypots. According to their experts, attackers are deploying the exploit released by netsecfish to download an ARM32 executable that establishes communication with a command-and-control server, thereby assimilating the compromised device into the botnet’s infrastructure.
Once enrolled in the command network, these devices become integral components of a larger framework used for DDoS attacks, malicious traffic proxying, and other forms of coordinated network activity. The primary targets are internet-connected systems lacking adequate security—among them, thousands of DVR units that remain unpatched.
Although the researcher initially reported 114,000 vulnerable DVRs accessible from the internet, Kaspersky’s telemetry indicates that this number has since declined to approximately 50,000. Nevertheless, the scope of the threat remains considerable. The highest concentrations of infected devices have been recorded in China, India, Egypt, Ukraine, Russia, Turkey, and Brazil. It is important to note, however, that these figures reflect only regions where Kaspersky telemetry is actively deployed and may not present a complete global picture.
As of publication, it remains unclear whether TBK Vision has issued a security update addressing CVE-2024-3721. Inquiries sent to the company have thus far gone unanswered. The situation is further complicated by the fact that the DVR-4104 and DVR-4216 models have been widely rebranded and distributed under various names—including Novo, CeNova, QSee, Pulnix, XVR 5 in 1, Securus, Night OWL, DVR Login, HVR Login, and MDVR—making it difficult to determine whether specific devices have received appropriate patches.
Netsecfish has a history of uncovering vulnerabilities later exploited in similar scenarios. In 2024, he reported the existence of a backdoor account and a new command injection flaw in tens of thousands of outdated D-Link routers, which likewise led to a rapid surge of attacks. In both cases, only a few days elapsed between the publication of proof-of-concept code and its weaponization in real-world incidents—a trend that underscores how swiftly cybercriminals adapt to publicly available exploits.
Taken as a whole, this campaign highlights the inherent risks of unsupported devices and underscores the urgent need to either decommission or segment equipment that no longer receives security updates. Without such measures, these devices quickly become subsumed into ever-evolving botnets, which continue to adapt and proliferate in the shifting threat landscape.


