A new wave of attacks leveraging the EDDIESTEALER malware has starkly illustrated the growing ingenuity of social engineering tactics and the evolving sophistication of methods used to circumvent modern browser defenses. In a recent campaign examined by experts at Elastic Security Labs, threat actors employed a Rust-based infostealer capable of bypassing Chrome’s application-bound data protections to extract unencrypted information—including cookies and user credentials.
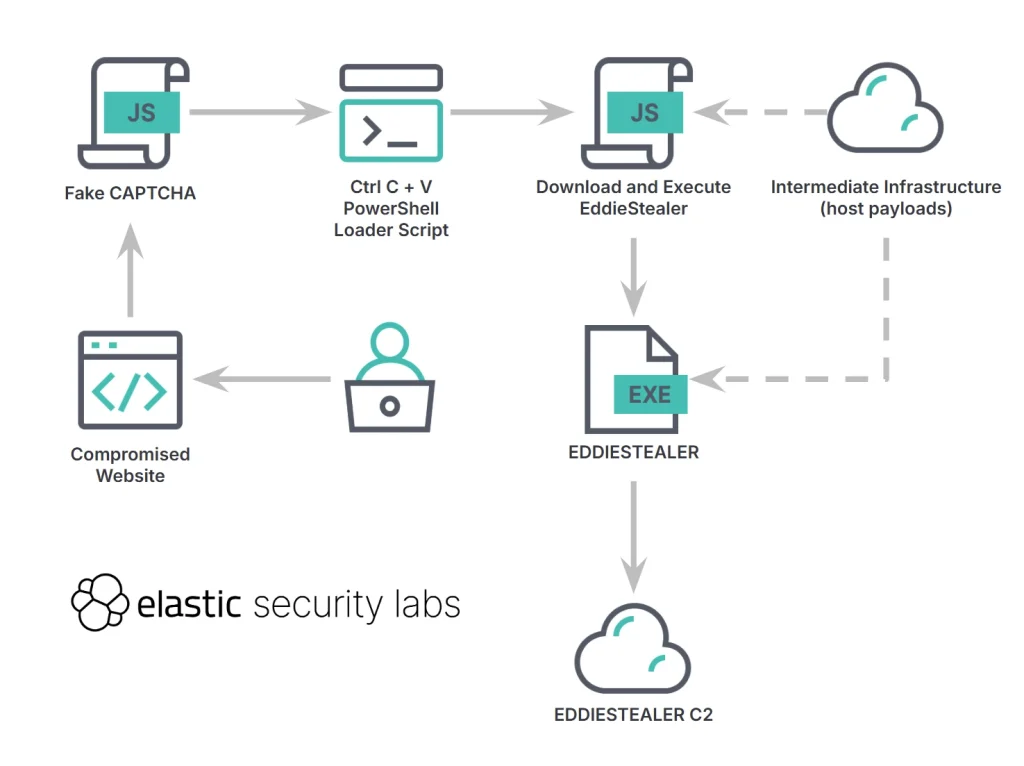
The large-scale operation begins with the compromise of legitimate websites, where malicious JavaScript is injected to replace standard CAPTCHA widgets with counterfeit “Verify you’re not a robot” prompts. Unsuspecting users are instructed to perform three simple steps: open the Run dialog, paste a copied command, and confirm execution. This tactic, known as ClickFix, has gained popularity in recent years as a form of social manipulation.
In reality, the victim unwittingly executes a concealed PowerShell script that downloads an intermediary component—“gverify.js”—which silently retrieves the primary EDDIESTEALER executable, obfuscated under a randomized name. The stealer proceeds to collect system metadata, enumerate processes, gather CPU and GPU details, and begins harvesting passwords, cryptocurrency wallets, messaging app data, FTP credentials, and information from password managers.
A defining characteristic of EDDIESTEALER is its aggressive use of modern obfuscation techniques: string encryption, unconventional API function discovery, and sandbox evasion via renaming NTFS Alternate Data Streams. These mechanisms greatly enhance its persistence and complicate detection by automated analysis tools.
Particularly noteworthy is its method for extracting unencrypted Chrome data: a reengineered ChromeKatz module written in Rust enables the malware to harvest cookies and passwords not only from active sessions but also by silently launching a browser window positioned far beyond the visible screen. This allows the malware to access the memory of Chrome’s networking process and retrieve credentials without any user interaction.
In its latest iterations, EDDIESTEALER transmits harvested data to the command server immediately upon infection—without awaiting instructions. Additionally, it incorporates support for interaction via the DevTools Protocol: the malware launches Chrome in remote-debug mode and establishes a WebSocket connection, granting direct access to sensitive data with no visible traces.
Another striking feature is the hardcoded encryption key embedded within the binary for securing command-and-control communication, further complicating network traffic analysis. Throughout the exfiltration process, the malware performs continuous checks for competing stealer instances and scrutinizes the execution environment for defensive tools.
Meanwhile, other hacker groups continue to evolve the ClickFix methodology. Security firm c/side has observed similar attack flows targeting macOS, Android, and iOS. On macOS, victims are prompted to run Terminal commands, initiating shell scripts that install another prevalent infostealer—Atomic macOS Stealer (AMOS). On mobile platforms, the scheme adapts into drive-by Trojan downloads.
Furthermore, researchers at Nextron and Kandji have noted a surge in activity involving newly emerging stealer families—Katz Stealer and AppleProcessHub Stealer. Like EDDIESTEALER, Katz Stealer bypasses Chrome protections, but does so via DLL injection and encryption key extraction—without requiring elevated privileges. AppleProcessHub Stealer is designed to siphon bash/zsh history, SSH credentials, and data from the iCloud Keychain. Its dropper disguises itself as a Mach-O binary and deploys a bash script to carry out data exfiltration.
The observed proliferation of Rust-based malware underscores a broader trend: the pursuit of analysis-resistant, modular, and adaptable malicious tooling. Increasingly, these campaigns feature forged interfaces, multi-stage payload deployment, and highly configurable targeting mechanisms—posing a formidable challenge to even the most advanced cybersecurity solutions.


