The technical details of one of the most perilous vulnerabilities of 2025—CVE-2025-20188—have now been made publicly available. This critical flaw resides in Cisco’s wireless controllers running IOS XE. Researchers at Horizon3 have published an in-depth analysis which, although it does not include a ready-to-use exploit script for remote command execution, offers sufficient insight for a skilled professional—or even an AI system—to construct a viable attack.
Cisco officially disclosed the vulnerability on May 7. The flaw enables a remote attacker, without any authentication, to upload arbitrary files to the device, bypass directory constraints, and ultimately execute actions with superuser privileges. The root cause, as identified by the company, is the presence of a hardcoded secret key used to validate JSON Web Tokens (JWT) in the API access control mechanism.
The threat materializes only when the Out-of-Band AP Image Download feature is enabled—a mechanism allowing controllers to retrieve firmware for access points over an auxiliary communication path. When active, the following hardware models become vulnerable:
- Catalyst 9800-CL Wireless Controllers for cloud deployments
- Embedded Catalyst 9800 controllers in the 9300, 9400, and 9500 switch series
- Standalone Catalyst 9800 series devices
- Catalyst access points with built-in controllers
Horizon3’s investigation revealed that the vulnerability stems from how the server-side logic—implemented in Lua within the OpenResty framework (a fusion of Nginx and a Lua interpreter)—handles JWT tokens. Under normal conditions, token validation uses a key stored in the file /tmp/nginx_jwt_key. However, if this file is missing, the script defaults to using the string "notfound" as the secret key.
This effectively nullifies any authentication: an attacker need only craft a JWT using the HS256 algorithm with the key "notfound" to gain unauthorized access.
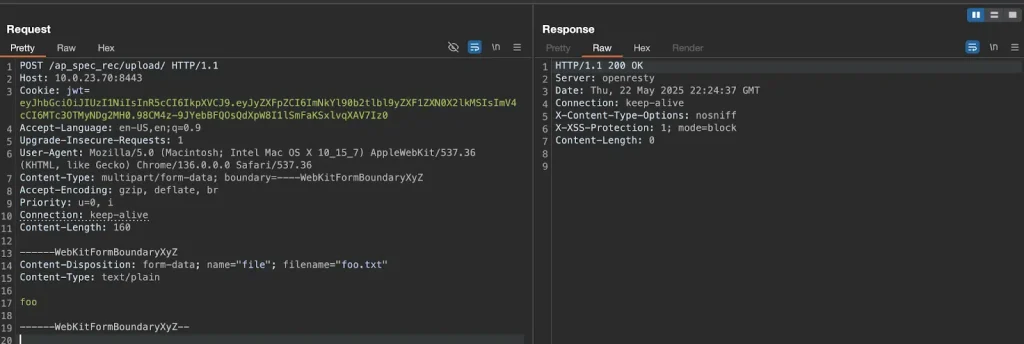
As part of their demonstration, Horizon3 sent a POST request to port 8443 targeting /ap_spec_rec/upload/, attaching a file whose path extended beyond the permitted directory. Even without malicious content, the file was accepted and stored outside the designated boundary—highlighting the server’s lack of proper path sanitization and validation.
While this initial step does not grant full system access, it establishes a foothold for deeper exploitation. By strategically placing a file in a critical directory and altering configuration parameters ingested by the system, remote execution of arbitrary code becomes feasible. In one outlined scenario, the attacker manipulates the native pvp.sh script, which monitors specific directories for changes. By tampering with its configuration and triggering a restart, the malicious payload can be executed.
This grants the attacker complete control over the controller, including the ability to implant web shells, persistent backdoors, and lateral movement within the corporate network. Notably, the attack does not require administrative credentials—merely an open port and an enabled image download function suffice.
Horizon3 underscores that the JWT handling mechanism suffers from grave architectural flaws. Since OpenResty processes JWTs directly within Lua scripts and lacks an additional cryptographic abstraction layer, any logical misstep instantly translates into a critical vulnerability.
Cisco now urges users to apply the firmware update to version 17.12.04 or later, which fully mitigates the issue. As a temporary measure, disabling the Out-of-Band image download feature—which exposes the vulnerable interface—can help reduce risk until the update is deployed.


