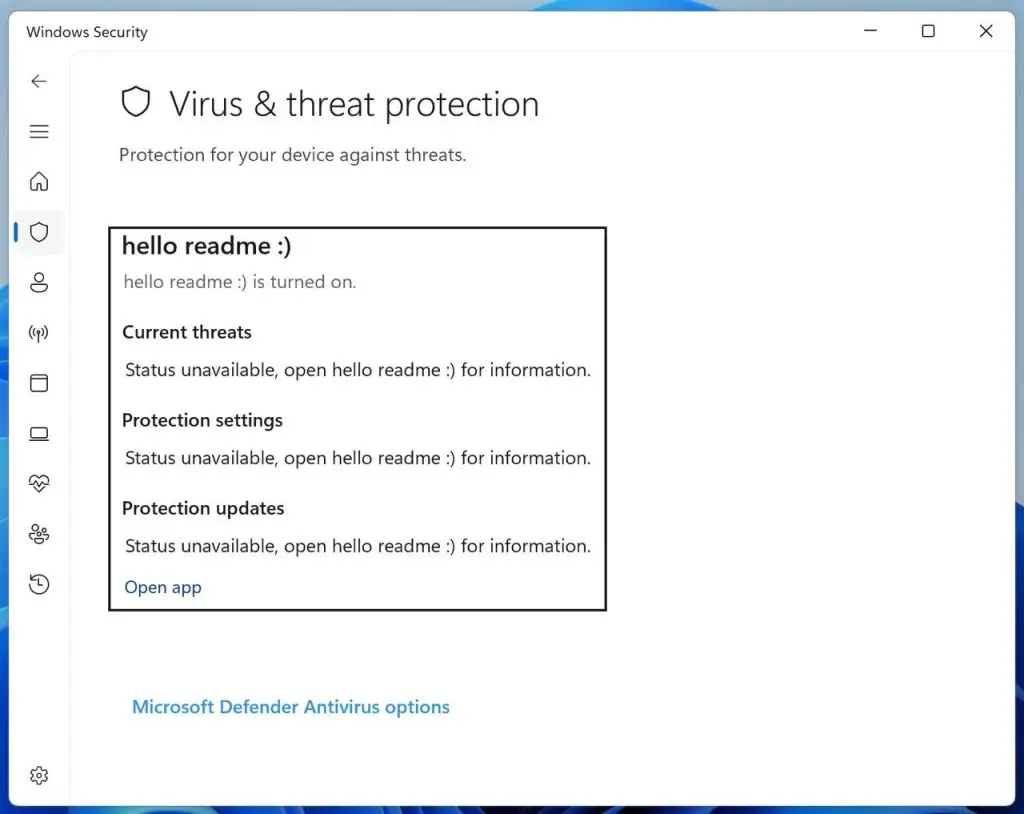
A newly released tool named Defendnot, freely available on GitHub, possesses the capability to completely disable Microsoft Defender on Windows devices while masquerading as legitimate antivirus software. Its core tactic involves exploiting a non-standard mechanism within the Windows Security Center (WSC), which is responsible for registering antivirus solutions. When the system detects that a third-party antivirus is already installed, the built-in Defender automatically deactivates to prevent potential conflicts. In reality, however, no actual antivirus is ever installed — it is merely a deception to disable the native protection.
This loophole was ingeniously leveraged by the tool’s creator, known under the alias es3n1n. He developed a library that formally meets WSC’s requirements and successfully passes Windows validation checks. As a result, the counterfeit antivirus registers as a legitimate solution, prompting Microsoft Defender to seamlessly disable its real-time protection.
Defendnot’s predecessor was a project named no-defender, which employed the code of an actual antivirus to gain registration through WSC. However, after the legitimate vendor filed a DMCA takedown request, the project was removed from GitHub. The new tool avoids similar legal pitfalls: it is built entirely from scratch and uses a fictitious DLL, steering clear of any copyright infringement.
To bypass Windows’ own safeguards — such as Protected Process Light (PPL) and digital signature verification — Defendnot injects its library into the trusted system process Taskmgr.exe. This maneuver allows it to circumvent restrictions and seamlessly register the fake antivirus under any chosen display name.
Once registration is complete, Microsoft Defender is instantly disabled, leaving the device entirely unprotected and vulnerable to all forms of attack. For persistence and ease of deployment, Defendnot employs the Windows Task Scheduler, ensuring the counterfeit antivirus launches automatically with every system startup.
The tool is bundled with a loader capable of transmitting configuration parameters via a file named ctx.bin, allowing customization of the displayed antivirus name, toggling registration, and enabling detailed logging.
Although the author frames the project as a research endeavor, it starkly illustrates the fragility of even trusted security components when subjected to skilled manipulation and elevated privileges.
At present, Microsoft Defender has begun detecting and quarantining Defendnot under the classification Win32/Sabsik.FL.!ml, indicating Microsoft’s efforts to shut down this method of neutralizing its protection. Nevertheless, the fundamental vulnerability — the blind trust placed in registered software — remains unaddressed.


