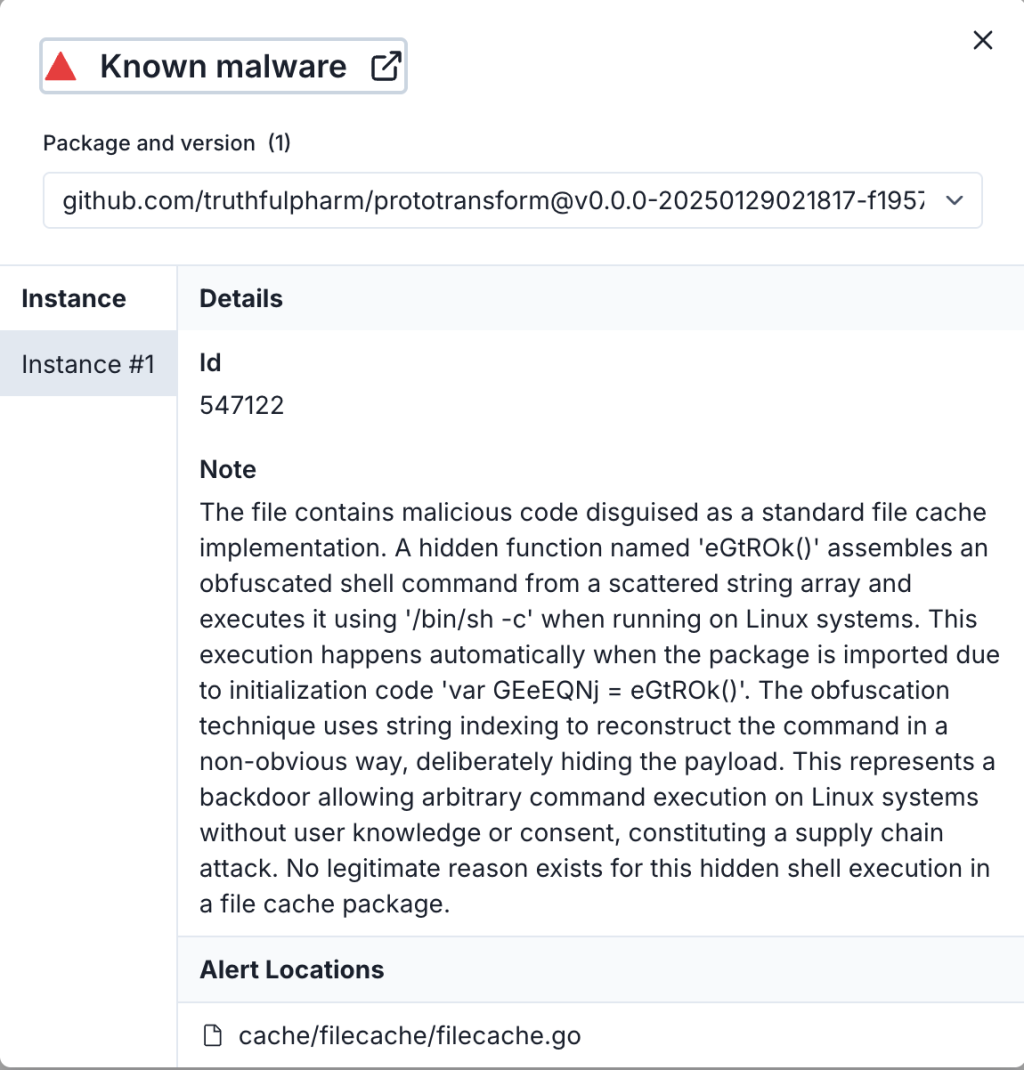
Three malicious components have been discovered within the Go programming module ecosystem, capable of triggering complete data destruction on Linux systems. These packages initially appeared legitimate, raising no suspicions among developers, yet concealed within them was obfuscated code designed to initiate the next stage of a sophisticated attack.
Once installed, the malware would determine whether it was operating on a Linux system. If so, it connected to a remote server via wget to retrieve a script engineered to obliterate the device’s primary disk. This script overwrote the /dev/sda partition with zeros, rendering data recovery impossible and the system entirely inoperable.
Analysts at Socket emphasized that this approach eliminates any possibility of forensic analysis or data restoration. The attack underscores the devastating potential of supply chain compromises, where misplaced trust in source code can lead to catastrophic consequences.
In the wake of this incident, experts also observed a surge in malicious packages infiltrating other popular repositories. In the npm registry, components capable of stealing mnemonic phrases and private cryptocurrency wallet keys were identified. Some bore names that alluded to payment systems, likely to mislead unsuspecting users. These modules were specifically crafted to harvest sensitive data and exfiltrate it to threat actors.
Simultaneously, tools with similar objectives were uncovered in Python’s PyPI repository. Among them, packages such as web3x and herewalletbot featured embedded functionality for seed phrase theft and have collectively been downloaded more than 6,800 times since their publication in 2024.
Of particular concern was a cluster of seven PyPI packages that employed Gmail’s SMTP servers and WebSocket connections to covertly communicate with remote operators. Hardcoded Gmail credentials enabled the malware to transmit installation success notifications and maintain persistent contact with the attacker. The use of a legitimate cloud service significantly reduced the likelihood of detection, as corporate networks rarely restrict traffic routed through well-known domains.
Among all identified packages, cfc-bsb stood out. Although lacking SMTP capabilities, it implemented a fully functional WebSocket protocol, granting attackers remote access to compromised machines.
To mitigate such threats, developers are urged to scrutinize package publication histories, verify repository links—particularly those pointing to GitHub—review dependencies regularly, and limit access to private keys. Special attention should be paid to anomalous outbound traffic, especially via SMTP, as even widely trusted services like Gmail can be weaponized for clandestine data exfiltration.


