The discovery of a serious zero-day vulnerability in Viasat satellite modems has once again underscored the fragility of hidden components within critical infrastructure. Researchers from ONEKEY, utilizing automated static analysis of binary files, uncovered a dangerous flaw affecting models RM4100, RM4200, EM4100, RM5110, RM5111, RG1000, RG1100, EG1000, and EG1020.
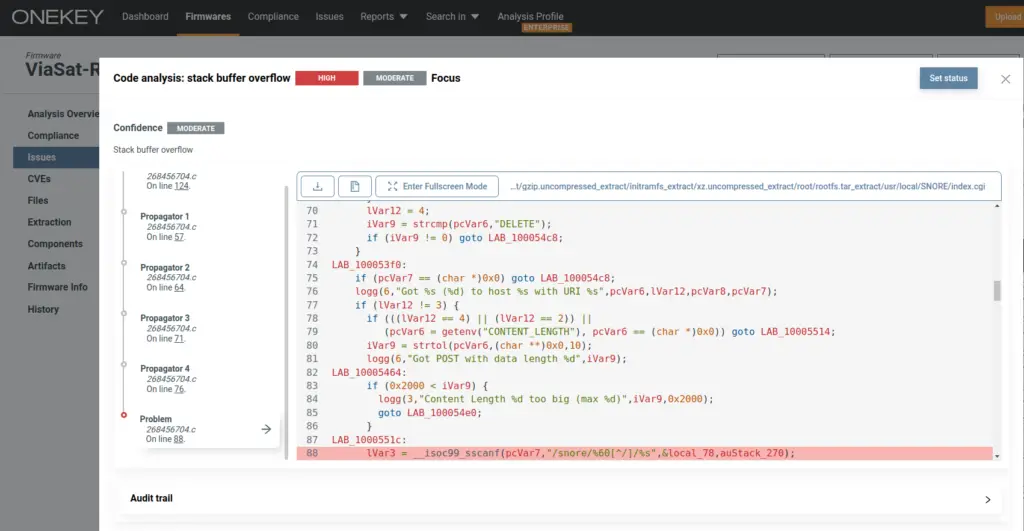
The vulnerability, assigned CVE-2024-6198 and rated 7.7 on the CVSS scale, resides in the SNORE web interface, which operates via lighttpd on TCP ports 3030 and 9882. The issue stems from insecure handling of HTTP requests within a CGI binary located at /usr/local/SNORE. Improper parsing of the REQUEST_METHOD and REQUEST_URI variables leads to a stack overflow through unsafe usage of the sscanf function, enabling an attacker to gain control over critical system registers.
According to the research team, exploitation can be achieved by sending a specially crafted request, for instance, to the address “192[.]168[.]100[.]1:9882/snore/blackboxes/” followed by 512 repeated characters. Despite the presence of a non-executable stack as a protective measure, successful exploitation remains possible through the use of Return-Oriented Programming (ROP) techniques, which allow an attacker to hijack the execution flow.
Vulnerable firmware versions include those earlier than 3.8.0.4 for the RM4100, RM4200, and EM4100 models, and earlier than 4.3.0.1 for the remaining devices. Viasat has released patches in firmware updates 3.8.0.4 and 4.3.0.2, distributed through automatic OTA updates. Device owners are advised to ensure their equipment is connected to the network to receive the latest updates and to verify installation via the administrative panel.
The revelation of this critical flaw emerged as a result of routine firmware monitoring conducted through the ONEKEY platform. The research team emphasized that this case highlights the necessity of employing such tools to safeguard complex network environments and to enhance transparency within embedded software ecosystems.
Coordinated disclosure of the vulnerability began on May 15, 2024, and concluded on May 25, 2025, after a significant number of real-world devices had been patched. Despite a few deadline extensions, the process was marked by effective collaboration between the researchers and the company.
This incident once again underscored the critical importance of early vulnerability detection within the hidden layers of network infrastructure. Given the pivotal role satellite modems play in maintaining communications, unaddressed vulnerabilities could have devastating consequences. Timely updates and independent firmware audits have thus become indispensable prerequisites for ensuring security in the modern digital landscape.


