A new and formidable player has emerged on the cybercrime stage: Cisco Talos has uncovered the operations of an initial access broker operating under the alias ToyMaker. This threat actor sells compromised systems to ransomware operators, notably the CACTUS group.
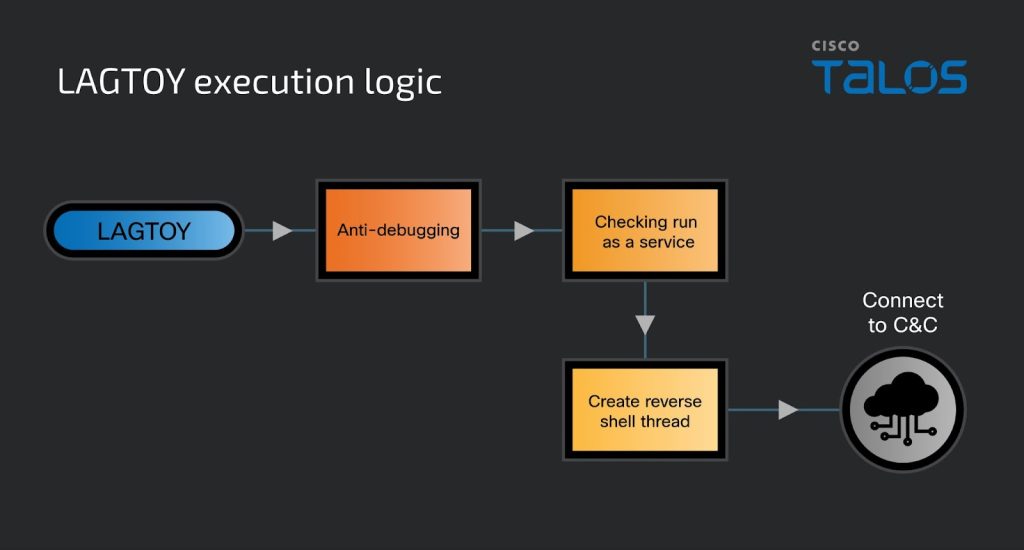
ToyMaker employs specially crafted malware known as LAGTOY, also referred to as HOLERUN, which establishes reverse shells and executes commands on infected devices.
The first reports of this threat surfaced in late March 2023 through analyses by Mandiant, a Google-owned cybersecurity firm. At that time, ToyMaker was linked to the group UNC961, also known as Gold Melody and Prophet Spider.
The attacks leverage a wide array of known vulnerabilities in internet-facing applications. Upon gaining initial access, the attacker quickly surveys the victim’s infrastructure, harvests credentials, and deploys LAGTOY — a process typically completed within a week.
During the operation, ToyMaker connects to a remote server via SSH to download a specialized tool, Magnet RAM Capture, using it to create a memory dump of the target machine — presumably to extract sensitive credentials.
LAGTOY communicates with a hardcoded command-and-control (C2) server, receiving instructions for further exploitation. According to Mandiant, the malware executes processes and commands under the context of specific users with appropriate privileges.
Technical analysis revealed that the malware processes three distinct commands from the C2 server at 11,000-millisecond intervals, ensuring efficient control over the compromised networks.
Following ToyMaker’s initial breach of a company’s systems and the theft of credentials, there was a lull of approximately three weeks. Talos researchers later observed that the CACTUS ransomware group infiltrated the same organization’s network using the stolen information.
The attacker’s behavior — brief presence within the system and rapid handover of access to partners without extensive file exfiltration — points to purely financial motivations, with no evidence of intelligence-gathering objectives.
Once the CACTUS operators gained access, they conducted their own reconnaissance and established a foothold for long-term persistence, employing legitimate tools such as OpenSSH, AnyDesk, and the eHorus Agent to entrench themselves within the network.


