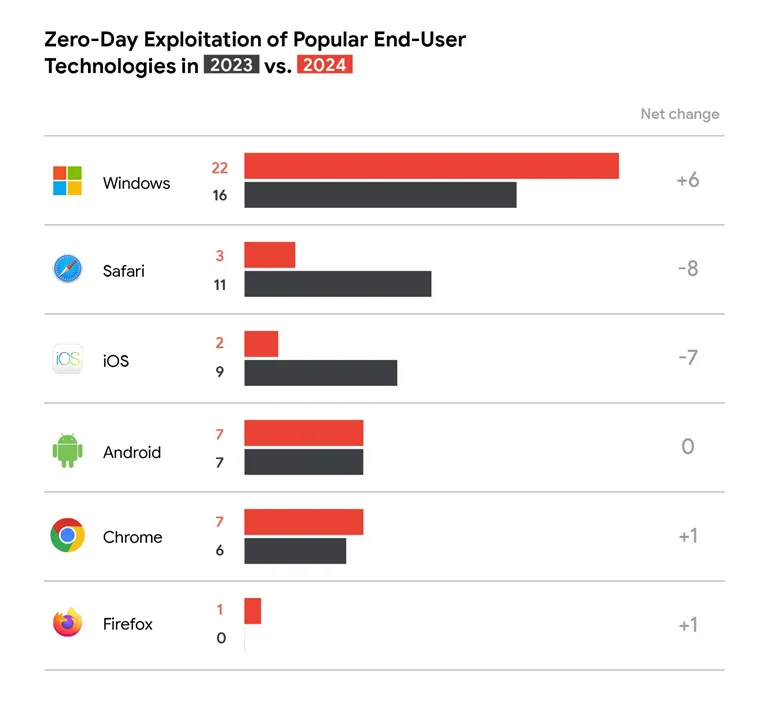
Zero-Day Vulnerabilities by Product, 2023 vs. 2024 (GTIG)
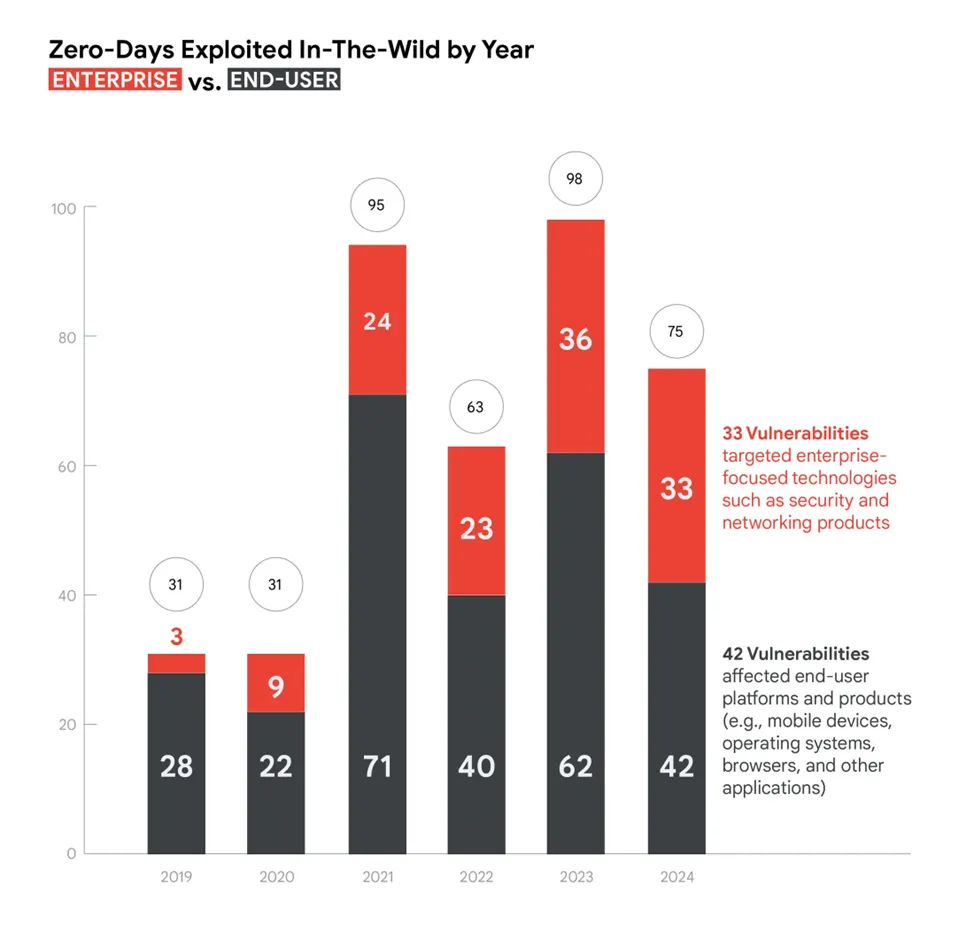
The number of zero-day vulnerabilities actively exploited by malicious actors in 2024 reached 75 — a decline from 98 cases reported in 2023, yet still significantly higher than the figures recorded in 2022. An analysis conducted by Google Threat Intelligence Group (GTIG) reveals that, despite the overall decrease, attackers are increasingly shifting their focus from conventional targets to complex enterprise-grade solutions — particularly those related to cybersecurity and network infrastructure.
The most notable shift has occurred in the balance between consumer and enterprise technologies. Whereas attackers previously concentrated on browsers, mobile devices, and operating systems, nearly half of all zero-day vulnerabilities in 2024 (44%) were tied to business-oriented products. Among the most targeted were solutions from companies such as Ivanti, Cisco, and Palo Alto Networks, with VPNs, threat detection systems, and other critical components of enterprise security bearing the brunt of the attacks.
Traditional targets — browsers and mobile operating systems — saw diminished exploitation. The number of zero-day attacks on browsers dropped from 17 to 11, while those on mobile platforms decreased from 17 to 9. Meanwhile, attacks against desktop operating systems rose to 30%, with Windows maintaining its position as the most targeted platform, accounting for 22 vulnerabilities.
One factor influencing the shifting attack landscape was the increased activity of Commercial Surveillance Vendors (CSV). Although their share of documented attacks declined compared to the previous year, they remain responsible for a substantial portion of zero-day exploits — including those requiring physical access to a device. Notably, GTIG and Amnesty International documented the use of CVE-2024-53104 in a breach of an Android device via a modified USB tool.
Among state-backed threat actors, China and North Korea emerged as the most active. Chinese groups such as UNC5221 launched aggressive campaigns against enterprise technologies, including exploiting a chain of vulnerabilities in Ivanti products. North Korean actors reached a comparable level of activity for the first time, leveraging five distinct zero-day vulnerabilities — including attacks targeting Chrome and Windows. One campaign of particular note, attributed to APT37, involved the silent distribution of malicious code through ad banners on South Korean websites, requiring no user interaction.
Additionally, activity was observed from groups with mixed motivations, such as CIGAR (also known as UNC4895 or RomCom), which combines financial crime with cyber espionage. GTIG attributes the group’s exploitation of Firefox and Windows vulnerabilities to privilege escalation, leading to full system compromise. These attacks enabled a transition from browser-level access to SYSTEM-level command execution — a critical level of control.
The primary objectives of such attacks remain remote code execution and privilege escalation. The most commonly exploited weaknesses included use-after-free bugs, command injection, and cross-site scripting (XSS). Most of these flaws stemmed from fundamental programming errors that could have been avoided through adherence to stringent software development standards.
The report’s authors emphasize that while major vendors continue to be prime targets, they have also gained considerable expertise in building resilient defense mechanisms. In contrast, newer market entrants — especially those in the enterprise space — may be less equipped to withstand such sophisticated threats. GTIG recommends heightened scrutiny of architectural decisions, fortified RPC interface security, and the adoption of zero-trust principles, including network segmentation and the enforcement of least-privilege access.
Although investments in defensive technologies are rising, zero-day exploits remain an exceptionally valuable asset for both cyberespionage and cybercrime. According to GTIG’s forecast, interest in these vulnerabilities is only expected to intensify in the years ahead — particularly in relation to products that enable broad yet covert access to critical infrastructure.


